Law enforcement authorities from nine countries have taken down over 1,000 servers used by the Rhadamanthys infolstealer, VenomRAT, and Elysium botnet malware operations in the latest phase of Operation Endgame, an international action targeting cybercrime.
The joint action, coordinated by Europol and Eurojust, was also supported by multiple private partners, including Cryptolaemus, Shadowserver, Spycloud, Cymru, Proofpoint, CrowdStrike, Lumen, Abuse.ch, HaveIBeenPwned, Spamhaus, DIVD, and Bitdefender.
Between 10 and 14 November 2025, police officers conducted searches at 11 locations in Germany, Greece, and the Netherlands, seized 20 domains, and took down 1,025 servers used by the targeted malware operations.

This phase of Operation Endgame has also led to the arrest of a key suspect in Greece on November 3, 2025, linked to the VenomRAT remote access trojan.
“The dismantled malware infrastructure consisted of hundreds of thousands of infected computers containing several million stolen credentials,” Europol said in a Thursday press release.
“Many of the victims were not aware of the infection of their systems. The main suspect behind the infostealer had access to over 100 000 crypto wallets belonging to these victims, potentially worth millions of euros.”
Europol also advised using politie.nl/checkyourhack and haveibeenpwend.com to check if computers were infected with these malware strains.
Today’s announcement confirms BleepingComputer’s report from Tuesday that the Rhadamanthys infostealer operation has been disrupted, with the malware-as-a-service’s customers stating they no longer have access to their servers.
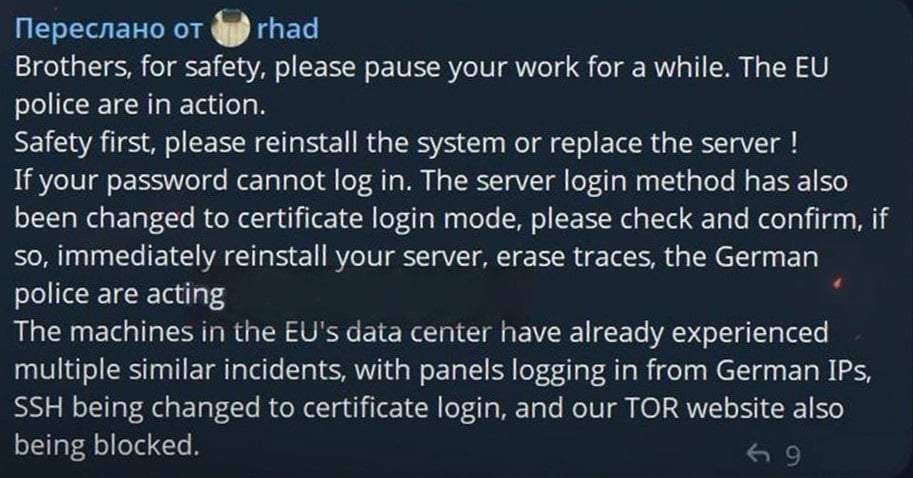
The Rhadamanthys developer also said in a Telegram message that they believed German law enforcement was behind the disruption, as web panels hosted in EU data centers logged German IP addresses connecting before the cybercriminals lost access.
Operation Endgame has been responsible for multiple disruptions, first seizing over 100 servers used by various malware operations, including IcedID, Bumblebee, Pikabot, Trickbot, and SystemBC.
The joint action has also targeted ransomware infrastructure, the AVCheck site, Smokeloader botnet customers and servers, and other major malware operations, such as DanaBot, IcedID, Pikabot, Trickbot, Smokeloader, Bumblebee, and SystemBC.
In April 2024, the Ukrainian cyber police also arrested a Russian man in Kyiv for working with Conti and LockBit ransomware operations to make their malware undetectable by antivirus software.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
