Uhale Android-based digital picture frames come with multiple critical security vulnerabilities and some of them download and execute malware at boot time.
Mobile security company Quokka conducted an in-depth security assessment on the Uhale app and found behavior suggesting a connection with the Mezmess and Voi1d malware families.
The researchers reported the issues to ZEASN (now ‘Whale TV’), the Chinese firm behind the Uhale platform used in the digital picture frames of numerous different brands, but received no reply to multiple notificaitions since May.

Automatic malware delivery
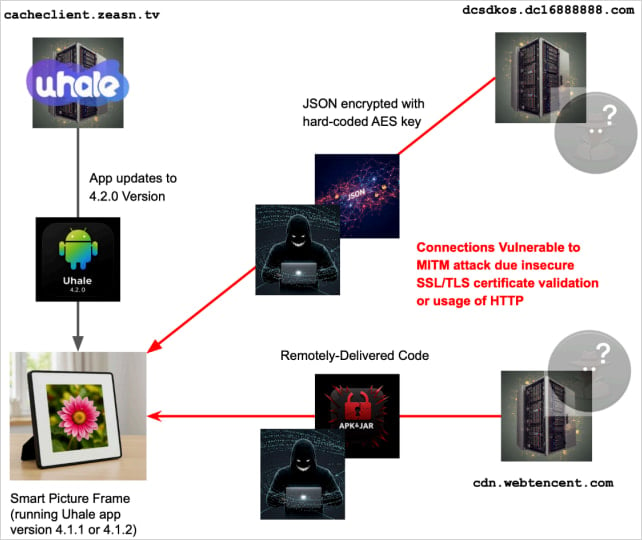
Starting with the most alarming findings, many of the analyzed Uhale photo frames download malicious payloads from China-based servers at boot.
“Upon booting, many investigated frames check for and update to the Uhale app version 4.2.0,” Quokka researchers say in the report.
“The device then installs this new version and reboots. After the reboot, the updated Uhale app initiates the download and execution of malware.”
The downloaded JAR/DEX file that is saved under the Uhale app’s file directory is loaded and executed at every subsequent boot.
The devices that Quokka examined had the SELinux security module disabled, came rooted by default, and many system components were signed with AOSP test-keys.
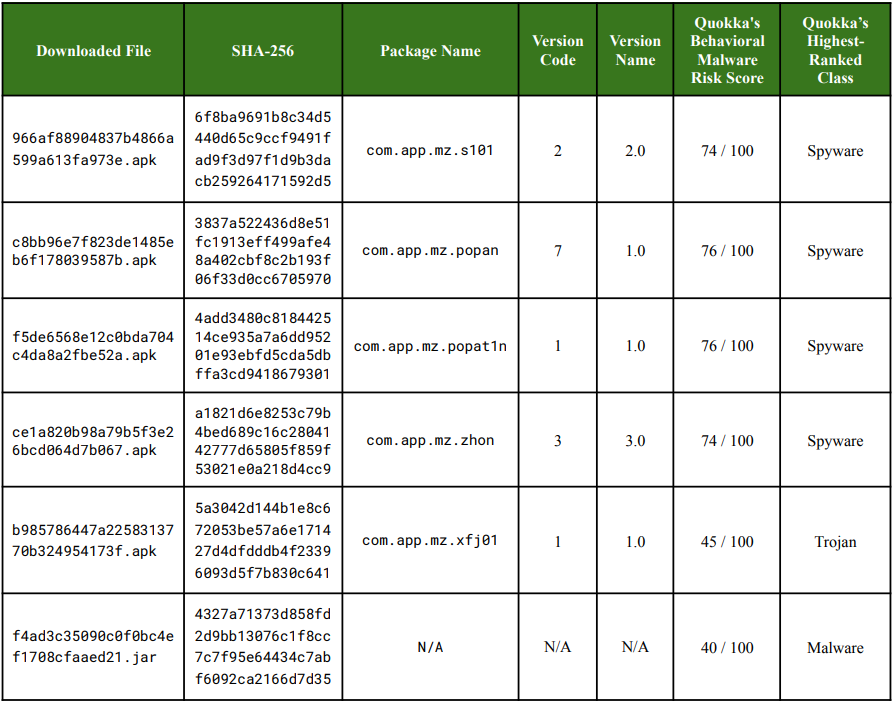
Source: Quokka
The researchers found evidence linking the downloaded payloads to the Vo1d botnet and Mzmess malware families, based on package prefixes, string names, endpoints, delivery workflow, and artifact locations.
However, it is unclear how the devices got infected.
Source: Quokka
Multiple security gaps
Aside from the malware delivery, which did not occur on all Uhale-branded picture frames, the researchers also discovered more than a dozen vulnerabilities.
Among the 17 security issues that Quokka discloses in the report, 11 of which have CVE-IDs assigned, below are the most significant:
- CVE-2025-58392 / CVE-2025-58397 – An insecure TrustManager implementation allows man-in-the-middle injection of forged encrypted responses, leading to remote code execution as root on affected devices.
- CVE-2025-58388 – The app’s update process passes unsanitized filenames directly into shell commands, enabling command injection and remote installation of arbitrary APKs.
- CVE-2025-58394 – All tested frames ship with SELinux disabled, are rooted by default, and use public AOSP test-keys, so they’re essentially fully compromised out of the box.
- CVE-2025-58396 – The pre-installed app exposes a file server on TCP port 17802 that accepts unauthenticated uploads, allowing any local network host to write or delete arbitrary files.
- CVE-2025-58390 – The app’s WebViews ignore SSL/TLS errors and permit mixed content, allowing attackers to inject or intercept data displayed on the device, enabling phishing or content spoofing.
- Hardcoded AES key (DE252F9AC7624D723212E7E70972134D) used to decrypt sdkbin responses.
- Several models include Adups update components and outdated libraries, while the app also uses weak crypto patterns and hardcoded keys, creating supply-chain risks.
Since most of these products are marketed and sold under various brands without mentioning the platform they use, it is difficult to estimate the exact number of potentially impacted users.
The Uhale app has more than 500,000 downloads on Google Play and 11,000 user reviews in the App Store. Uhale-branded photo frames on Amazon have nearly a thousand user reviews.
BleepingComputer has independently contacted ZEASN with a request for comment, but we have not received a response by publication time.
It is recommended that consumers only buy electronic devices from reputable brands that use official Android images without firmware modifications, Google Play services, and built-in malware protections.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
