Security researcher Paul McCarty has uncovered a massive coordinated spam campaign targeting the npm ecosystem. The IndonesianFoods worm, comprising over 43,000 malicious packages published across at least 11 user accounts, remained active in the registry for nearly two years before detection.
The campaign derives its distinctive name from its unique package naming scheme. The embedded malicious script randomly combines Indonesian names (“andi,” “budi,” “cindy,” “zul”) with Indonesian food terms (“rendang,” “sate,” “bakso,” “tapai”), appends random numbers from 1-100, and adds suffixes like “-kyuki” or “-breki.”
This naming pattern generates package names such as “zul-tapai9-kyuki” and “andi-rendang23-breki.”
This represents more than 1% of the entire npm ecosystem and demonstrates significant gaps in current supply chain security measures.
A random version number, such as “2.3.1” or “4.1.3”, to bypass npm’s duplicate version detection.
What makes this campaign particularly insidious is that the packages appear legitimate at first inspection.
How Hackers Infiltrated the npm Ecosystem
Each contains a standard Next.js project structure with proper configuration files, legitimate dependencies (React, Next.js, Tailwind CSS), and professional documentation.
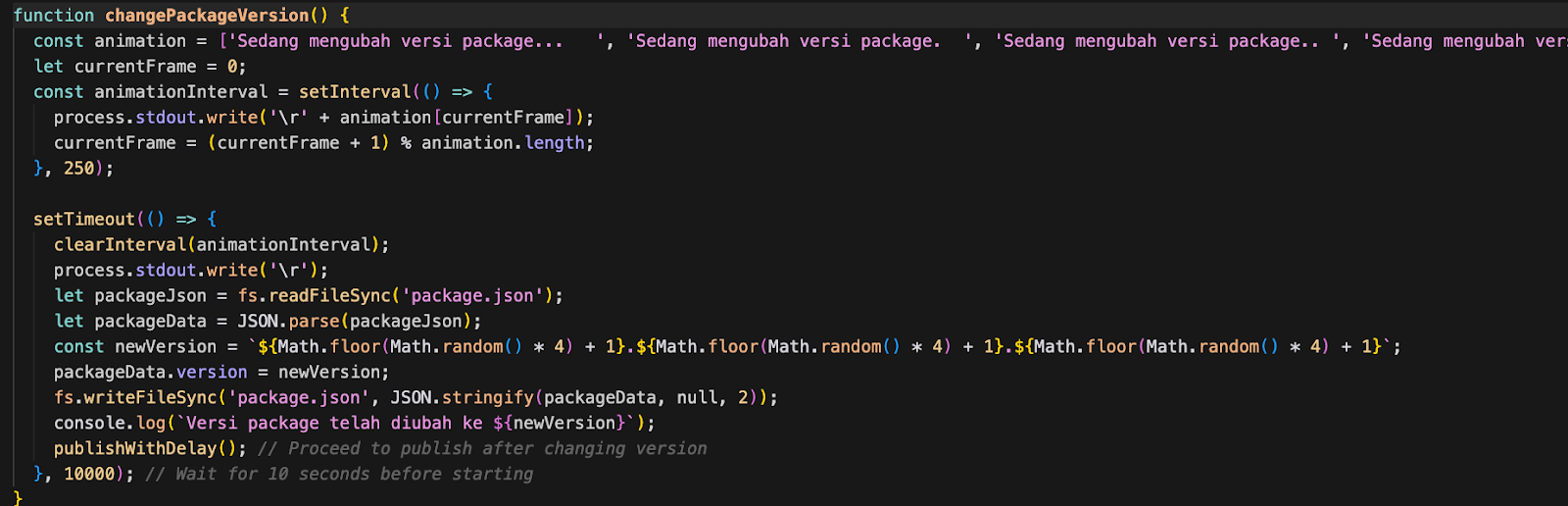
The malicious component a script file named either “auto.js” or “publishScript.js” sits unreferenced in the package structure and remains dormant until manually executed.
There are no postinstall hooks or lifecycle scripts that trigger automatically during installation, allowing the packages to evade automated security scanners.
When the script executes, it performs three coordinated actions in an infinite loop. First, it removes the “private” flag from package.json to bypass protections preventing accidental public publishing.


Second, it generates random version numbers to circumvent npm’s duplicate version detection. Third, it publishes new packages to the registry with randomized names.
A single execution publishes approximately 12 packages per minute, 720 per hour, or 17,000 per day, suggesting either multiple victims or direct attacker involvement in the flood.
The campaign operates with worm-like spreading capabilities through dependency chains. These spam packages reference each other as dependencies, creating a self-replicating network.
Installing one package can trigger automatic downloads of 8-10 additional spam packages, exponentially multiplying registry bandwidth usage and complicating cleanup efforts.
Researchers discovered that several attacker-controlled packages include “tea.yaml” files listing TEA accounts, revealing an attempt to monetize the campaign through tokens on blockchain reward systems designed for open-source contributions.
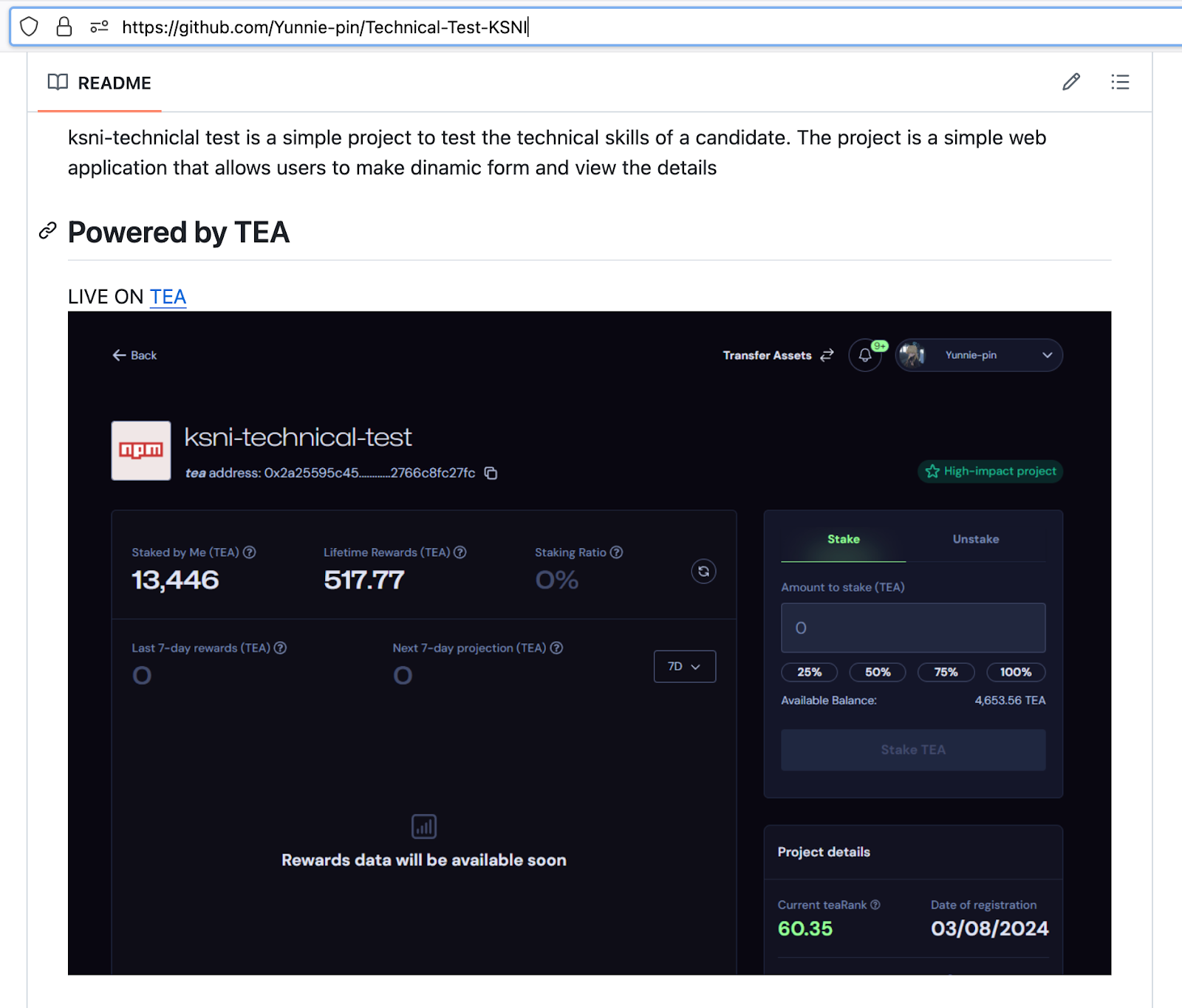

This represents a sophisticated multi-phase attack that evolved from simple registry spam to cryptocurrency monetization schemes.
At least one package maintainer appears to have an associated LinkedIn profile identifying them as an Indonesian software engineer, explaining the regional specificity of the operation.
The campaign used multiple naming variants, with some packages employing the legitimate “unique-names-generator” npm package to create alternative patterns like “able_crocodile-notthedevs,” suggesting deliberate operational evolution.
Organizations should immediately verify their dependencies against the eleven compromised accounts: voinza, yunina, noirdnv, veyla, vndra, vayza, bipyruss, sernaam.b.y, jarwok, doaortu, and rudiox.
Notably, some packages accumulated over 2,000 weekly downloads, creating potential vectors for future malicious code injection.
The IndonesianFoods campaign highlights a troubling shift in supply chain attack strategies. Rather than targeting high-profile packages for immediate impact, attackers deployed a volume-based approach with thousands of low-profile packages, letting probability work in their favor.
This demonstrates that persistence, scale, and strategic thinking can circumvent traditional security measures designed to catch technically sophisticated attacks during installation.
The npm ecosystem requires immediate defensive improvements: tighter rate limiting on publishers, automated pattern detection for bulk campaigns, and stricter account verification for high-volume publishing. Additionally, the TEA project should deactivate offending accounts and wallets to prevent continued unauthorized token earnings.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




