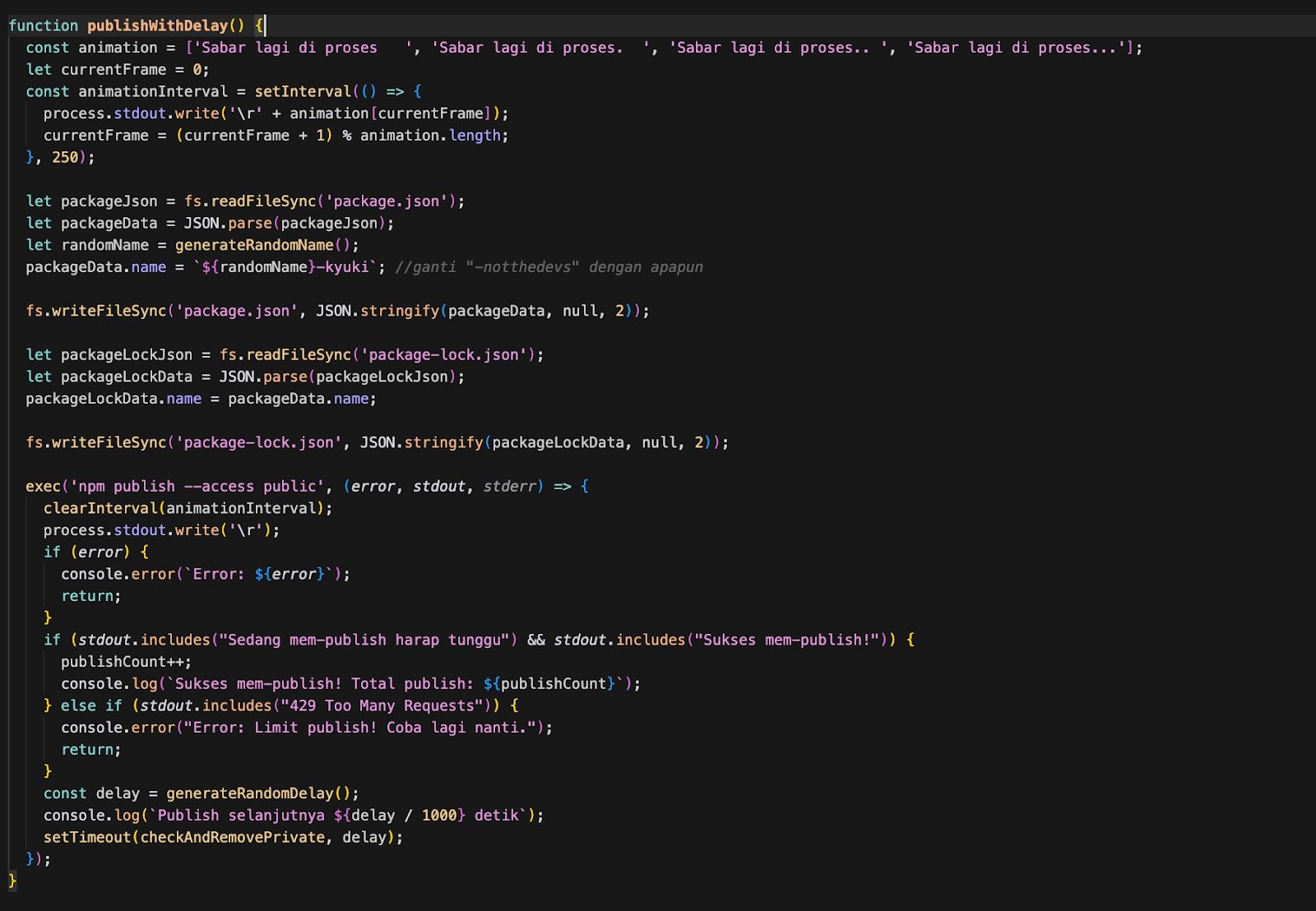
A self-spreading package published on npm spams the registry by spawning new packages every every seven seconds, creating large volumes of junk.
The worm, dubbed ‘IndonesianFoods,’ due to its distinctive package naming scheme that picks random Indonesian names and food terms, has published over 100,000 packages according to Sonatype, and the number is growing exponentially.
Although the packages do not have a malicious component for developers (e.g., stealing data, backdooring hosts), this could change with an update that introduces a dangerous payload.

The level of automation and large-scale nature of the attack create the potential for broad supply-chain compromise.
Security researcher Paul McCarty, who first reported this spam campaign, created a page to track the offending npm publishers and the number of packages they have released on the platform.
Sonatype reports that the same actors performed another attempt on September 10, with a package named ‘fajar-donat9-breki.’ Although that package contained the same replication logic, it failed to spread.
“This attack has overwhelmed multiple security data systems, demonstrating unprecedented scale,” Sonatype’s principal security researcher, Garret Calpouzos, told BleepingComputer.
“Amazon Inspector is flagging these packages through OSV advisories, triggering a massive wave of vulnerability reports. Sonatype’s database alone saw 72,000 new advisories in a single day.”
The researcher commented that IndonesianFoods does not appear to focus on infiltrating developer machines, but rather to stress the ecosystem and disrupt the world’s largest software supply chain.
“The motivation is unclear, but the implications are striking,” noted Calpouzos.
A report from Endor Labs on the IndonesianFoods campaign mentions that some packages appear to abuse the TEA Protocol, a blockchain system that rewards OSS contributions with TEA tokens, containing tea.yaml files listing TEA accounts and wallet addresses.
By publishing thousands of interconnected packages, attackers inflated their impact scores to earn more tokens, indicating a financial motive behind the attack.
Source: Endor Labs
Also, Endor Labs reports that the spam campaign actually began two years ago, with 43,000 packages being added in 2023, TEA monetization being implemented in 2024, and the worm-like replication loop introduced in 2025.
The IndonesianFoods campaign comes in the context of several similar automation-based supply-chain attacks on open-source ecosystems, including the GlassWorm attack on OpenVSX, the Shai-Hulud worm employing dependency confusion propagation, and the hijacks of widely used packages like chalk and debug.
Individually, these incidents caused limited damage, but they highlight a new trend in which attackers increasingly exploit automation and scale to overwhelm open-source ecosystems.
Sonatype also warned that these simple yet impactful operations create ideal conditions for threat actors to slip in more serious malware into open-source ecosystems.
As the attack continues to unfold, software developers are advised to lock down dependency versions, monitor for abnormal publishing patterns, and implement strict digital signature validation policies.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
