The office of Pennsylvania’s attorney general has confirmed that the ransomware gang behind an August 2025 cyberattack stole files containing personal and medical information.
This comes after Attorney General Dave Sunday confirmed in early September that the incident was a ransomware attack and his office refused to pay the ransom requested by the cybercriminals after they encrypted compromised systems.
“The OAG later learned that certain files may have been accessed without authorization. The OAG reviewed which data may have been involved and learned that certain personal information was contained in some files,” said the Pennsylvania Office of the Attorney General (OAG) in a Friday press release.

“Based on the OAG’s review of the data involved, for some individuals the information involved may have included name, Social Security number, and/or medical information.”
On August 9th, when the breach was discovered, the threat actors took down systems and services on Pennsylvania OAG’s network, including the office’s website, employees’ email accounts, and landline phone lines, in an attack with widespread and crippling impact.
While the Pennsylvania OAG has yet to share more information on how the network was breached, cybersecurity expert Kevin Beaumont found that the Pennsylvania AG’s network had several public-facing Citrix NetScaler appliances vulnerable to ongoing attacks exploiting a critical vulnerability (CVE-2025-5777) known as Citrix Bleed 2.
According to Beaumont, one of the two devices was taken down since July 29th, while the other has been offline since August 7th.
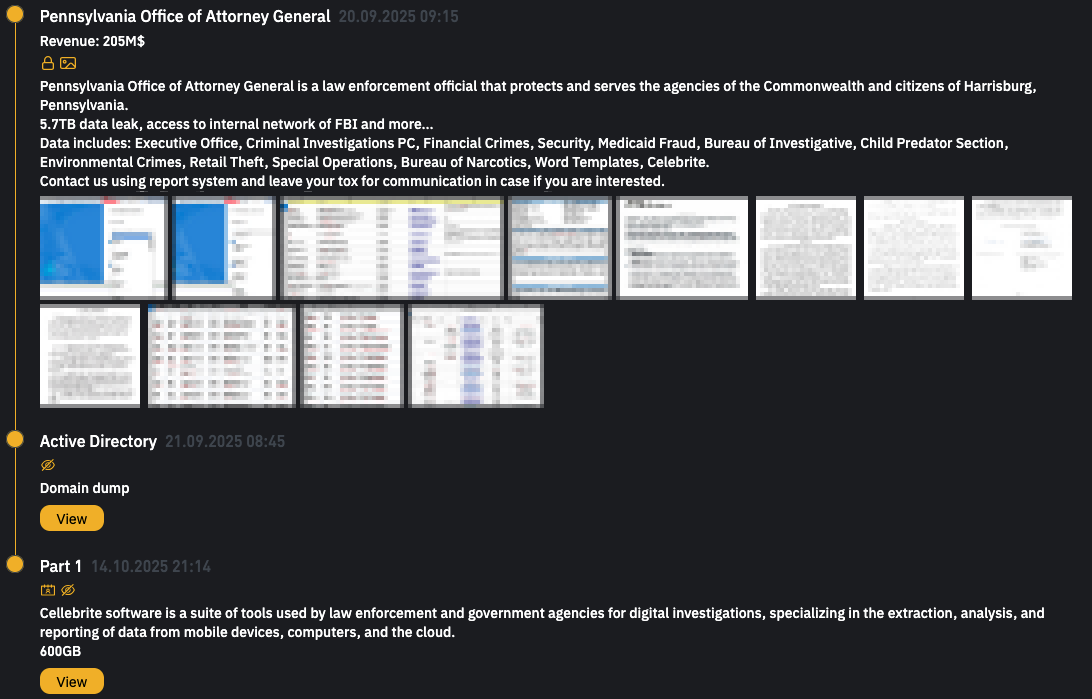
Breach claimed by INC Ransom
Although the Pennsylvania OAG didn’t publicly attribute the breach to a specific ransomware operation, the INC Ransom gang claimed responsibility for the attack on September 20th, when they added it as a new entry on their dark web leak site.
At the time, the ransomware group claimed that they had stolen 5.7TB worth of files from the Pennsylvania OAG’s network and said that the breach allegedly provided them with access to an FBI internal network.
INC Ransom surfaced as a ransomware-as-a-service (RaaS) operation in July 2023 and has since targeted organizations in the private and public sectors worldwide.
Its list of victims spans a wide range of sectors, from education and healthcare to government and entities like Yamaha Motor Philippines, Scotland’s National Health Service (NHS), food retail giant Ahold Delhaize, and the U.S. division of Xerox Business Solutions (XBS).
This is the third time that Pennsylvania state entities have been breached in a ransomware attack: Delaware County paid a $500,000 ransom following a DoppelPaymer attack in 2020 to recover encrypted systems, and a ransomware attack took down the Pennsylvania Senate Democratic Caucus’ network in 2017.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
