Seven packages published on the Node Package Manager (npm) registry use the Adspect cloud-based service to separate researchers from potential victims and lead them to malicious locations.
The purpose of the attack is to lead victims to cryptocurrency scam sites, according to an analysis from researchers at application security company Socket.
All malicious packages were published under the developer namee ‘dino_reborn’ (geneboo@proton[.]me) between September and November. However, six of them contain malicious code while the seventh is used to build a malicous webpage:

- signals-embed
- dsidospsodlks
- applicationooks21
- application-phskck
- integrator-filescrypt2025
- integrator-2829
- integrator-2830
The researchers say that signals-embed is not inherently malicious and contains only the code to create a white decoy webpage. The other six have code that collects data about the visitors to determine if the traffic comes from a researcher or from a potential victim.
This is achieved by collecting information from the browser environment, such as browser identifiers, page and URL data, host and hostname of the current page, and prepares it for sending to Adspect’s API.
Adspect cloaking
The six malicious packages contain a 39kB code that features the cloaking mechanism, Socket researchers note, adding that the code executes automatically on page load without extra user action, due to Immediately Invoked Function Expression (IIFE) wrapping.
The attack executes when the compromised developer’s web application loads the malicious JavaScript in a browser.
According to Socket, the injected code features anti-analysis such as blocking right-click, F12, Ctrl+U, Ctrl+Shift+I, and reloading the page if DevTools is detected. This makes it more difficult for security researchers to inspect the webpage.
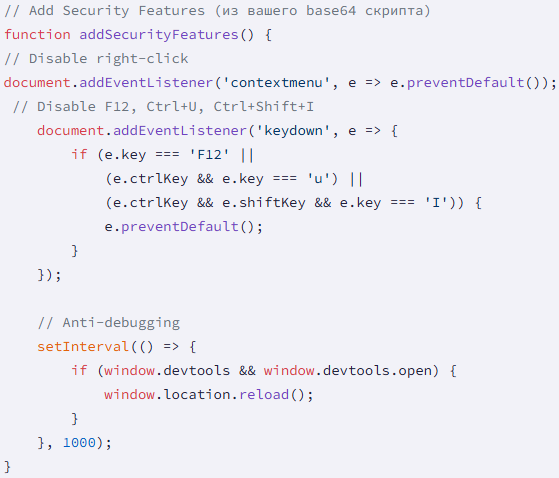
Source: Socket
The script gathers the visitor’s user agent, host, referrer, URI, query string, protocol, language, encoding, timestamp, and accepted content types, and sends the fingerprinting data to a threat actor proxy.
The real victim’s IP address is retrieved and forwarded to the Adspect API, which then evaluates the data to classify the visitor.
Visitors who qualify as targets are redirected to a fake cryptocurrency-branded (Ethereum, Solana) CAPTCHA page, triggering a deceptive sequence that opens an Adspect-defined URL in new tab while masking it as a user-initiated action.
If the visitors are flagged as potential researchers, a fake but benign Offlido company page is loaded to reduce suspicion.
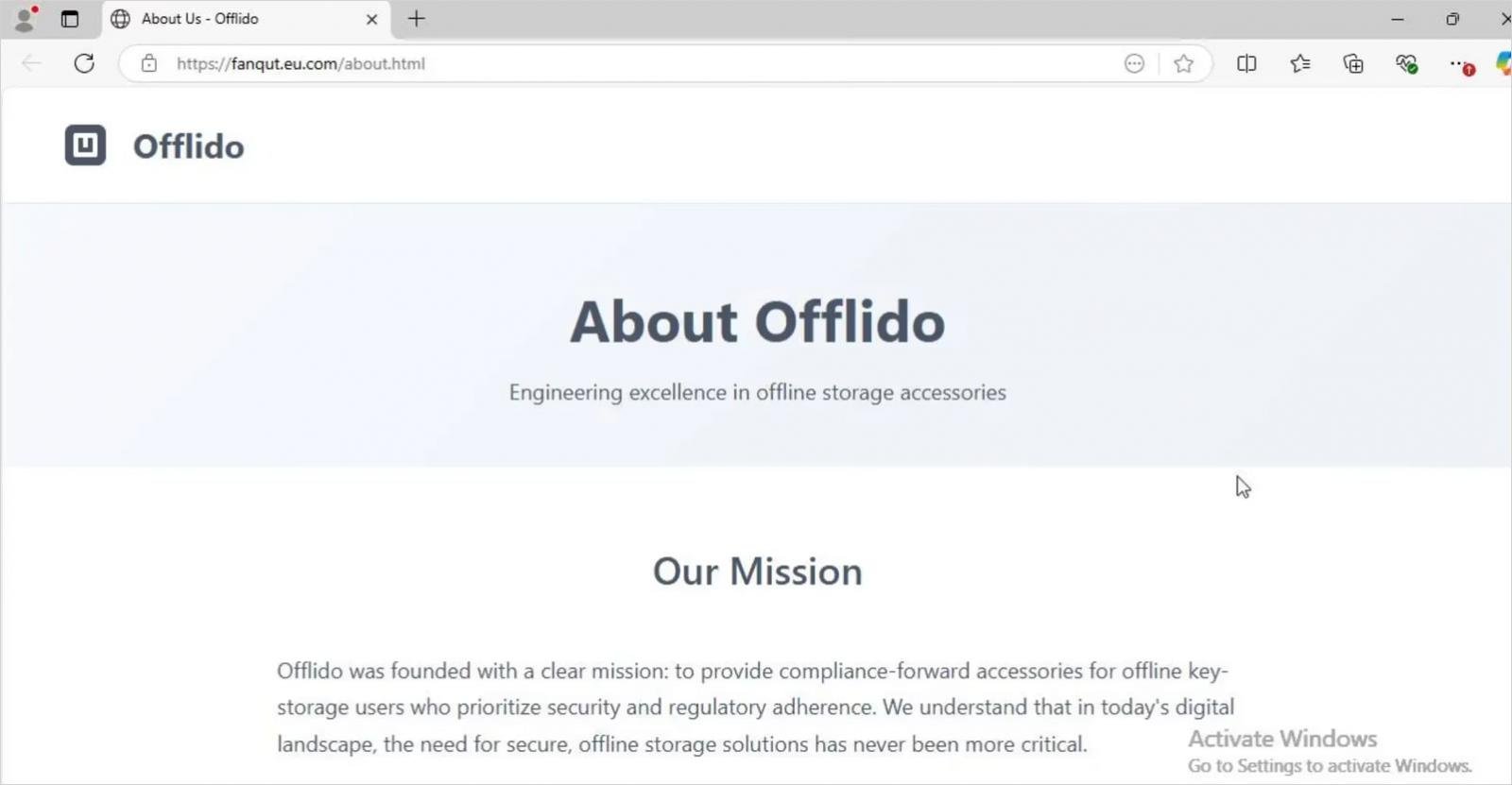
Source: Socket
Adspect is marketed as a cloud-based service that filters unauthorized acceess to a webpage, blocking bots and malicious actors and allowing legitimate users.
BleepingComputer has contacted the firm to determine if they are aware of the abuse and what mechanisms are in place to prevent it, but we have not received a response by publication time.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
