Google has taken a significant step toward its vision of an Agentic SOC by announcing the public preview of the Alert Triage and Investigation agent, a purpose-built AI agent natively embedded into Google Security Operations.
This advancement brings the promise of intelligent agents assisting human analysts with routine tasks, decision-making, and workflow automation closer to reality.
The Alert Triage and Investigation agent fundamentally transforms how security practitioners respond to alerts by autonomously performing initial triage, evidence gathering, and analysis.
Rather than requiring manual investigation of every alert, the agent conducts comprehensive examinations and delivers verdicts, enabling security teams to redirect their focus toward alerts that genuinely require human attention.
This capability addresses one of the most pressing challenges in security operations: alert fatigue and the overwhelming volume of alerts that often go untriaged.
During the private preview, the agent investigated hundreds of thousands of alerts across organizations of varying sizes and sectors, demonstrating its practical effectiveness.
A security analyst at a financial services firm noted that the alert and investigation summaries enabled rapid decision-making by clearly identifying whether alerts were malicious or benign.
The comprehensive investigations and explainability provided by the agent built trust with the technology while significantly reducing time spent on manual investigations.
Similarly, large US retailers reported that the agent drastically improved investigation timelines by consolidating information and running complex queries autonomously, eliminating an additional step in their workflow.
Streamline Security Incident Response
The Alert Triage and Investigation agent begins by conducting an initial investigation of Google Security Ops alerts, providing evidence and precise next steps based on analysis principles derived from Mandiant best practices.
The agent clarifies its process and references sources when making recommendations, ensuring analysts understand how conclusions were reached.
The agent’s investigative capabilities leverage multiple sophisticated functions. Dynamic Search Queries allow the agent to create and execute YARA-L searches to retrieve relevant environmental events, eliminating the need for analysts to craft these queries manually.
Threat Intel Enrichment integrates best-in-class threat intelligence from Google and Mandiant experts, providing context about key indicators and connecting investigative findings to the broader threat landscape.
Command Line Analysis examines command lines including encoded or obfuscated variations to determine their purpose and impact, delivering summaries in natural language for quick comprehension.
Process Tree Reconstruction dynamically creates process trees from telemetry to understand the full scale of attacks or alerts by analyzing child processes associated with alerts.
Additionally, the team leverages AI techniques such as auto-evaluators and golden datasets to ensure reliable quality and increased accuracy over time.
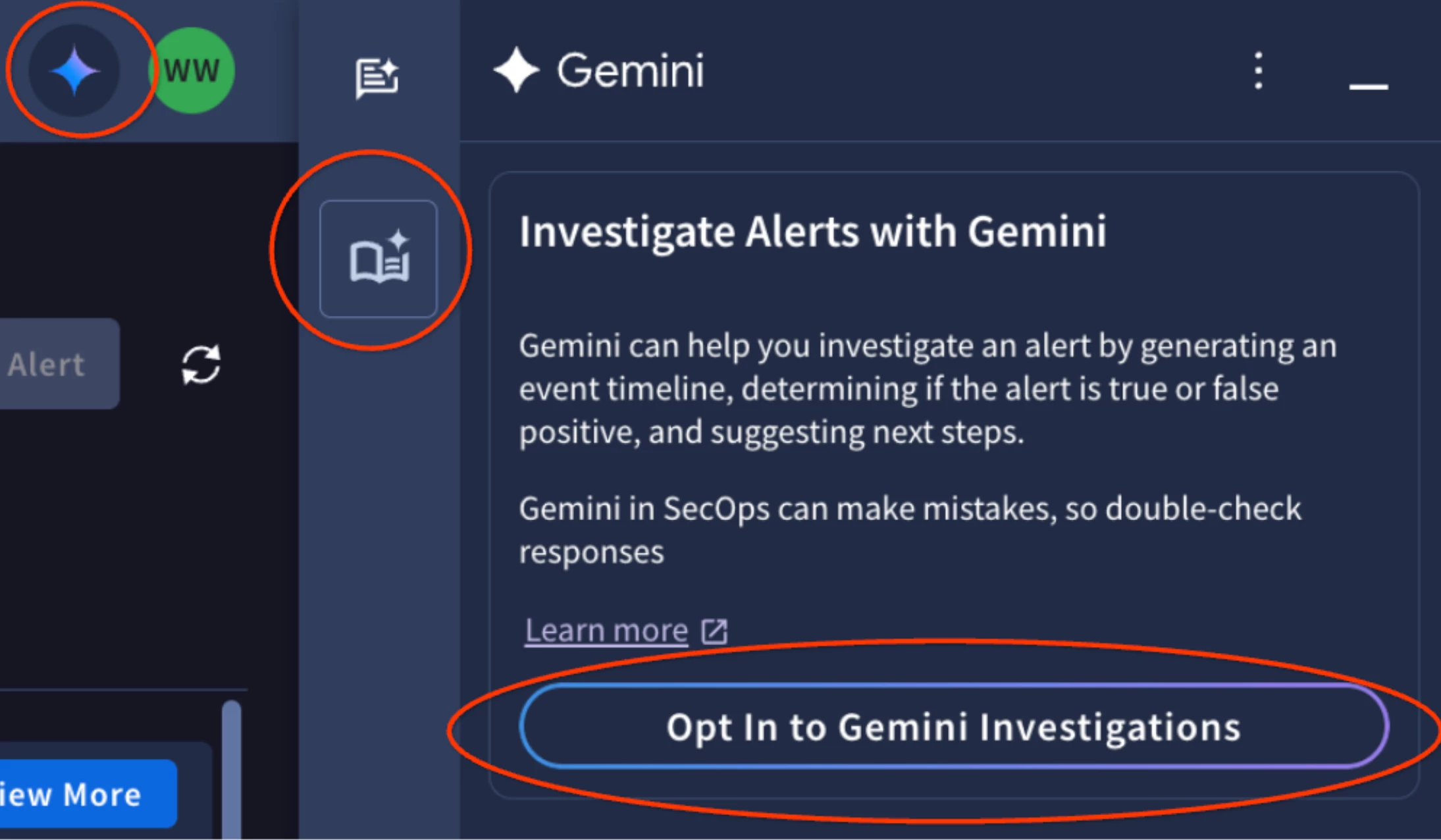
All eligible Google Security Operations Enterprise and Enterprise Plus users can opt into the public preview through the Gemini icon in their Google Security Operations interface.
Upon investigation completion, the agent determines whether to escalate alerts based on comprehensive analysis, deciding if evidence warrants further human review (True Positive) or lacks substantial supporting evidence (False Positive).
These determinations include confidence scores quantifying certainty based on available corroborating evidence.
Recognizing that agents require explainability and accuracy for security operations, Google implemented a multi-pronged evaluation approach.
The agent’s verdict alignment is continuously evaluated against human analysts investigating identical alerts, with accuracy measurements performed by combinations of Mandiant experts and Google Security Operations users.
The Alert Triage and Investigation agent is built entirely on Google’s AI technology stack, composed of multiple sub-agents leveraging Google Gemini Models through the Vertex AI Platform.
Mandiant expertise is encoded directly into the agent’s investigation decisions, and the agent integrates threat information from Google Threat Intelligence for decisions based on current threat landscapes.
Once enabled, automatic investigations begin immediately, with options for manual triggering through the Alerts & IOCs page or individual alert views using the blue “Run Investigation” button.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
