ESET researchers have uncovered a sophisticated attack chain orchestrated by the China-aligned threat actor PlushDaemon, revealing how the group leverages a previously undocumented network implant, EdgeStepper, to conduct adversary-in-the-middle attacks.
By compromising network devices and redirecting DNS queries to malicious servers, PlushDaemon intercepts legitimate software updates and replaces them with trojanized versions containing the SlowStepper backdoor.
This technique has enabled the threat actor to compromise targets across multiple continents since at least 2018.
The core of PlushDaemon’s attack infrastructure centers on EdgeStepper, internally called dns_cheat_v2 by developers.
Compiled as a MIPS32 ELF file written in using the GoFrame framework, EdgeStepper operates as a DNS proxy that fundamentally alters network traffic patterns within compromised networks.
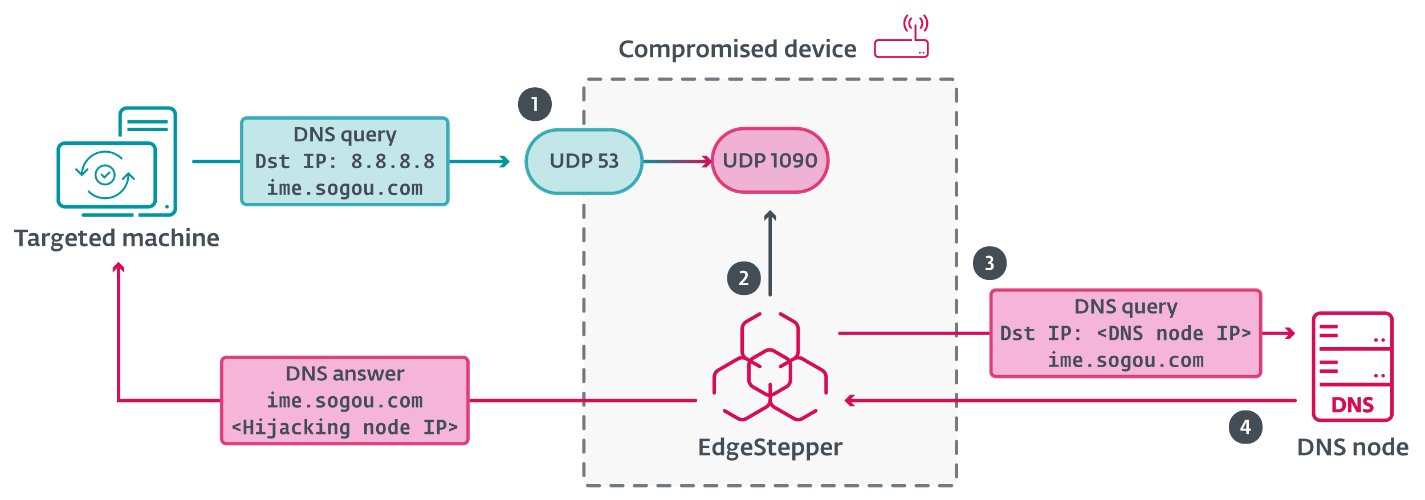
The tool begins by loading encrypted configuration data from /etc/bioset.conf, decrypting it using AES CBC with the default key “I Love Go Framework!”
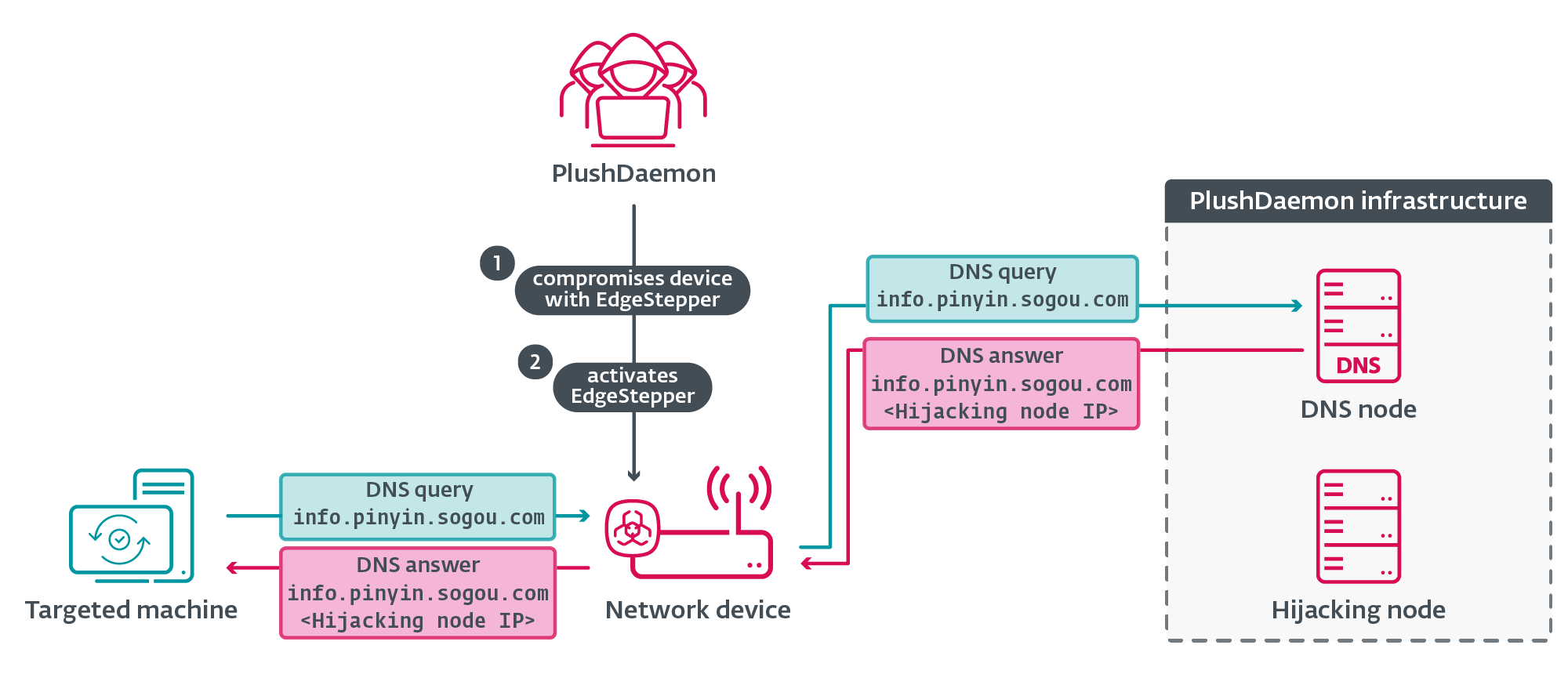
Once deployed on a compromised network device typically a router exploited through known vulnerabilities or weak credentials EdgeStepper redirects all DNS traffic to port 53 through its listener port 1090.
PlushDaemon that have been compromised through malicious updates, since 2019, according to ESET telemetry.
The implant then forwards DNS queries to a malicious DNS node controlled by PlushDaemon operators.
When the attacker’s DNS server receives a query for legitimate software update domains like Sogou Pinyin’s info.pinyin.sogou.com, it responds with the IP address of an attacker-controlled hijacking node.
Legitimate software attempting to download updates connects to this fake server instead, receiving malicious payloads disguised as genuine updates.
Network Compromise to Backdoor Installation
The attack sequence unfolds across multiple stages involving sophisticated downloader components.
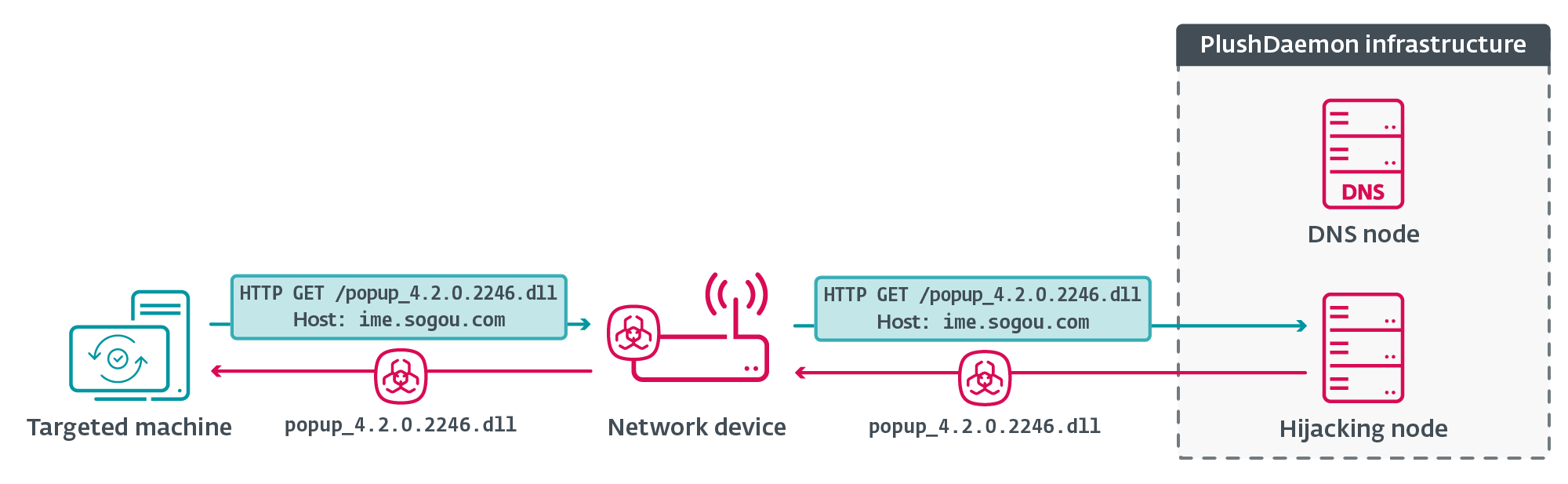
When legitimate software requests an update through EdgeStepper’s compromised network, the hijacking node serves LittleDaemon, a 32-bit PE executable that functions as the first-stage payload.
LittleDaemon checks whether the SlowStepper backdoor already exists on the system and, if absent, downloads DaemonicLogistics a position-independent code executed directly in memory without touching disk.
DaemonicLogistics interprets HTTP status codes as commands from the hijacking server, implementing at least seven distinct operations.
The downloader performs OS version identification and MAC address collection before requesting the final SlowStepper implant.
It validates received payloads using specific magic byte sequences: PK34 for ZIP archives and GIF89a for encrypted payloads, employing XOR decryption to extract and deploy the backdoor across the Windows system.
PlushDaemon’s campaigns leveraging EdgeStepper have compromised individuals and organizations across seven countries and regions since 2019.
Victims span the United States, Taiwan, mainland China including a Beijing university and Taiwanese electronics manufacturer Hong Kong, New Zealand, and Cambodia.
The 2025 Cambodian operations targeted automotive and manufacturing sector entities, including a Japanese company branch.
The software sends an HTTP GET request to ime.sogou.com to try to obtain the DLL; however, the communication is again redirected to the hijacking node.
Taiwan experienced consecutive compromise waves in 2021 and 2024, indicating sustained focus on the region.
Technical Infrastructure
The recovered EdgeStepper configuration reveals PlushDaemon’s infrastructure design, with the malicious DNS node domain resolving through ds20221202.dsc.wcsset[.]com.
An unused configuration block within the binary contained the domain test.dsc.wcsset[.]com, which resolved to IP address 47.242.198[.]250 identified as the hijacking node source since 2021.
Payload delivery typically routes through compromised legitimate domains (ime.sogou.com or mobads.baidu.com) or direct IP addresses, leveraging the hijacking node’s traffic interception to appear as authentic update servers.
This campaign demonstrates PlushDaemon’s evolution toward sophisticated supply-chain attack methodologies and network-level compromise techniques.
Organizations should prioritize DNS query monitoring, implement DNS-over-HTTPS to prevent hijacking, and conduct thorough network device hardening.
The group’s demonstrated capability to compromise network infrastructure represents a critical threat to entities in geopolitically sensitive regions and those handling sensitive intellectual property or government intelligence.
IoCs
Files
| SHA-1 | Filename | ESET Detection Name | Description |
|---|---|---|---|
| 8F569641691ECB3888CD4C11932A5B8E13F04B07 | bioset | Linux/Agent.AEP | EdgeStepper. |
| 06177810D61A69F34091CC9689B813740D4C260F | bioset.conf | Win32/Rozena.BXX | EdgeStepper encrypted configuration. |
| 69974455D8C13C5D57C1EE91E147FF9AED49AEBC | popup_4.2.0.2246.dll | Win32/Agent.AGXK | LittleDaemon. |
| 2857BC730952682D39F426D185769938E839A125 | sogou_wubi_15.4.0.2508_0000.exe | Win32/Agent.AFDT | LittleDaemon. |
Network
| IP Address | Domain | Hosting provider | First seen | Details |
|---|---|---|---|---|
| 8.212.132[.]120 | ds20221202.dsc.wcsset[.]com | Alibaba (US) Technology Co., Ltd. welivesecurity | 2024‑07‑12 | DNS/Hijacking node welivesecurity |
| 47.242.198[.]250 | test.dsc.wcsset[.]com | Alibaba Cloud LLC welivesecurity | 2024‑07‑12 | DNS/Hijacking node welivesecurity |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
