Compromised VPN credentials are the most common initial access vector for ransomware attacks, according to a new report.
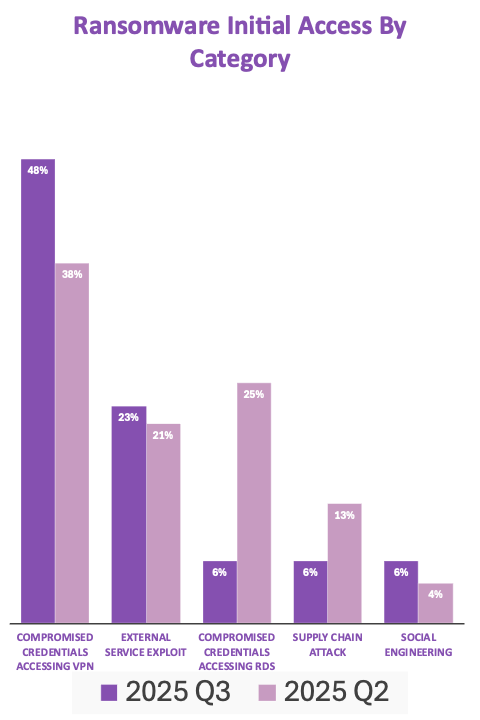
Nearly half of ransomware attacks in the third quarter abused compromised VPN credentials as the initial access point, according to research from Beazley Security, the cybersecurity arm of Beazley Insurance.
Nearly a quarter of initial access attacks came from external service exploitation, while remote desktop service (RDS) credential compromises, supply chain attacks and social engineering accounted for 6% each (chart below).
“This trend underscores the importance of ensuring that multifactor authentication (MFA) is configured and protecting remote access solutions and that security teams maintain awareness and compensating controls for any accounts where MFA exceptions have been put in place,” the report said.
In addition to the critical need for MFA, the report also underscores the importance of dark web monitoring for leaked credentials, which are often a precursor to much bigger cyberattacks.
SonicWall Compromises Led Attacks on VPN Credentials
A “prolonged campaign” targeting SonicWall devices by the Akira ransomware group was responsible for some of the 10-point increase in the percentage of VPN attacks. “Adding to SonicWall’s misery this quarter was a significant breach of their cloud service, including sensitive configuration backups of client SonicWall devices,” the report added.
Akira, Qilin and INC were by far the most active ransomware groups in the third quarter, Beazley said – and all three exploit VPN and remote desktop credentials.
Akira “typically gains initial access by exploiting weaknesses in VPN appliances and remote services,” the report said. In the third quarter, they used credential stuffing and brute force attacks to target unpatched systems and weak credentials.
Akira accounted for 39% of Beazley Security incident response cases in the third quarter.
Akira “consistently gained access by using valid credentials in credential stuffing attacks against SonicWall SSLVPN services, exploiting weak access controls such as absent MFA and insufficient lockout policies on the device,” the report said.
Qilin’s initial access techniques include phishing emails, malicious attachments, and brute forcing weak credentials or stolen credentials in remote desktop protocol (RDP) and VPN services.
INC Ransomware uses a combination of phishing, credential theft, and exploitation of exposed enterprise appliances for initial access. “Beazley Security responders observed the group leverage valid, compromised credentials to access victim environments via VPN and Remote Desktop,” the report said.
Cisco, Citrix Vulnerabilities, SEO Poisoning Also Exploited
Critical vulnerabilities in Cisco and Citrix NetScaler were also targeted by attackers in the third quarter.
In one campaign, a sophisticated threat actor leveraged CVE-2025-20333 and CVE-2025-20363 in Cisco ASA VPN components to gain unauthorized access into environments, Beazley said. Another campaign targeted a critical SNMP flaw (CVE-2025-20352) in Cisco IOS.
Threat actors also targeted Citrix NetScaler vulnerabilities CVE-2025-7775 and CVE-2025-5777. The latter has been dubbed “Citrix Bleed 2” because of similarities to 2023’s “Citrix Bleed” vulnerability (CVE-2023-4966).
A “smaller yet noteworthy subset” of ransomware attacks gained access via search engine optimization (SEO) poisoning attacks and malicious advertisements, used for initial access in some Rhysida ransomware attacks.
“This technique places threat actor-controlled websites at the top of otherwise trusted search results, tricking users into downloading fake productivity and administrative tools such as PDF editors,” the report said. “These tools can be trojanized with various malware payloads, depending on threat actor objectives, and can potentially give threat actors a foothold directly on the endpoint in a network. The attack is effective because it bypasses other traditional social engineering protections like email filters that prevent phishing attacks.”
