A Russian-speaking threat actor attributed to the username “koneko” has resurfaced with a sophisticated new botnet named Tsundere, discovered by Kaspersky GReAT around mid-2025.
This marks a significant evolution from a previous supply chain campaign that targeted Node.js developers in October 2024, revealing disturbing parallels in methodology and infrastructure.
Using typosquatting techniques registering package names nearly identical to legitimate libraries the attacker distributed 287 malicious Node.js packages through npm.
The October 2024 campaign demonstrated the threat actor’s initial proof-of-concept for compromising the JavaScript ecosystem.
Popular targets included Puppeteer, Bignum.js, and various cryptocurrency packages, affecting Windows, Linux, and macOS users across the developer community.
The unpackaging script is responsible for recreating this structure, including the node_modules directory with all its libraries, which contains packages necessary for the malware to run.
The campaign was short-lived, abandoned after detection, but it provided crucial insight into the attacker’s capabilities.
New Botnet, Expanded Scope
Tsundere represents a matured version of this threat. Rather than relying solely on supply chain compromise, the botnet employs multiple infection vectors including MSI installers disguised as popular games (Valorant, CS2, R6X) and PowerShell scripts.
Initial discovery of one implant traced back to a Remote Monitoring and Management (RMM) tool that downloaded a suspicious PDF.msi file, demonstrating the threat actor’s willingness to exploit legitimate tools for malware distribution.
The MSI installer strategy proved remarkably effective, bundling Node.js executables with malicious JavaScript files that run in the background.
The installer executes through Windows Installer CustomAction table, spawning hidden Node.js processes that load encrypted bot scripts using AES-256-CBC encryption.
The PowerShell variant similarly downloads Node.js from official repositories, creating a facade of legitimacy while deploying identical functionality.
What distinguishes Tsundere is its use of Ethereum smart contracts for command-and-control infrastructure resilience.
Rather than relying on traditional domain names vulnerable to takedown, the botnet stores WebSocket C2 addresses on the Ethereum blockchain using wallet 0x73625B6cdFECC81A4899D221C732E1f73e504a32 and contract 0xa1b40044EBc2794f207D45143Bd82a1B86156c6b.
This approach allows operators to rotate C2 servers at will without DNS-level interruption.
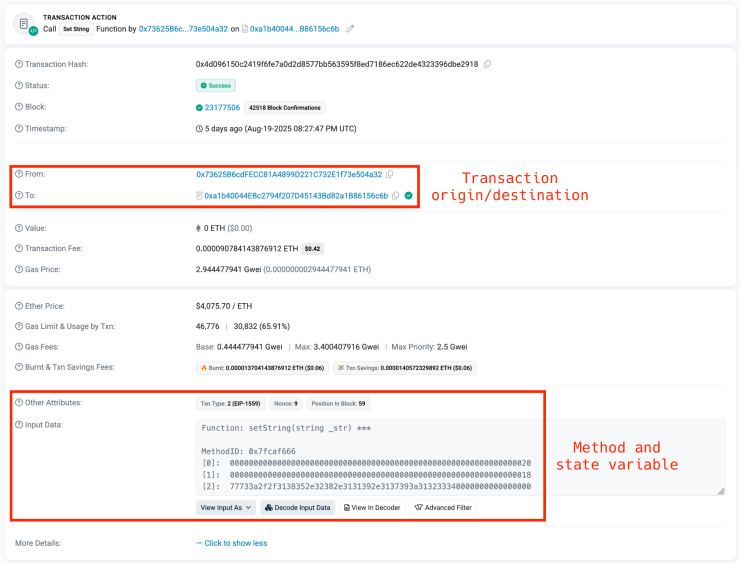
Infected machines query public Ethereum RPC endpoints to retrieve the current C2 address, establishing encrypted WebSocket connections for command execution.
The botnet employs dynamic JavaScript code evaluation, enabling operators to deploy arbitrary functionality through the C2 panel.
Marketplace Model and Infrastructure
The Tsundere control panel features an open-registration system allowing any user to build custom bots, create malware variants, and offer services on an integrated marketplace.
The panel integrates Monero wallet functionality, SOCKS proxy capabilities, and a Build system for generating unique bot variants. At the time of analysis, 90-115 bots maintained active connections.
Attribution evidence links Tsundere to the 123 Stealer (a commercial stealer available for $120 monthly) through shared infrastructure, with both threats operating from the same backend servers.
The threat actor’s profile on dark web forums listed the title “node malware senior,” reinforcing expertise in Node.js-based malware development.
With Tsundere infrastructure actively responding to bot connections and the underlying threat actor simultaneously promoting additional malware, security researchers expect this threat to escalate rather than diminish.
Organizations should monitor for related threats and implement robust supply chain security practices to mitigate the risk posed by this evolving botnet family.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
