The Acronis Threat Research Unit has uncovered a sophisticated global malvertising campaign called TamperedChef that disguises malware as legitimate everyday applications to compromise systems worldwide.
The operation uses social engineering, search engine optimization tactics, and fraudulently obtained digital certificates to trick users into installing backdoors that grant attackers remote access and control over infected machines.
TamperedChef address an evolution in malware distribution, delivering fully functional fake applications that mimic popular software such as browsers, PDF editors, e-book readers, and games.
These trojanized installers carry valid code-signing certificates from US-registered shell companies, making them appear trustworthy and helping them evade security detection.
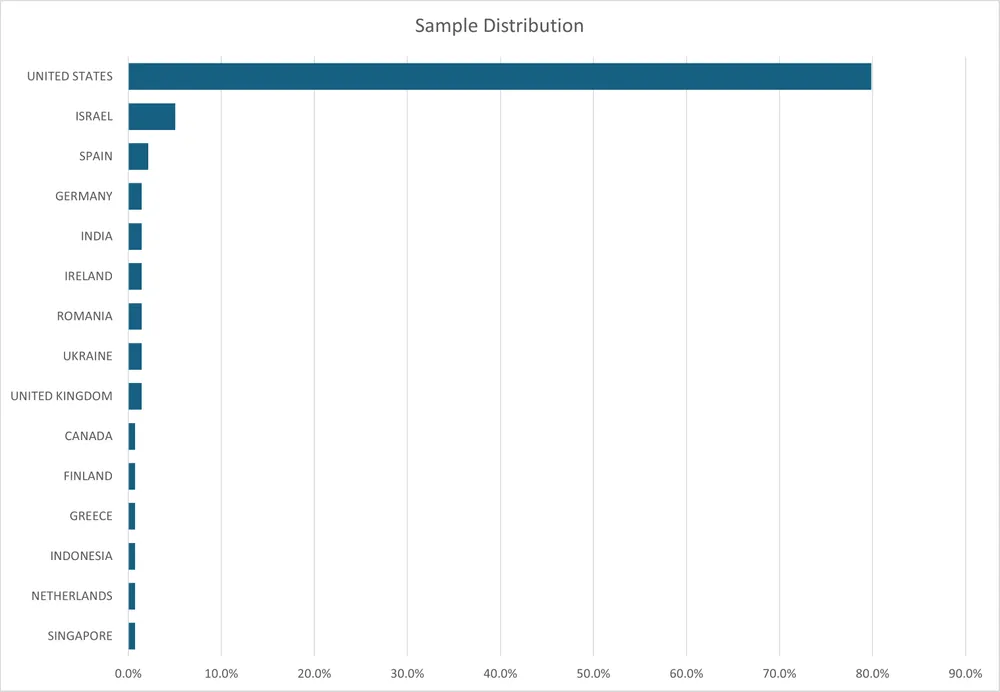
The campaign has primarily affected organizations in the Americas, with approximately 80% of victims located in the United States, though the infrastructure spans globally across multiple continents and industries.
Industrial-Scale Infrastructure
The threat actors behind TamperedChef operate with business-like sophistication, maintaining a network of disposable shell companies registered in states like Delaware and Wyoming.
These entities with names like Performance Peak Media LLC, Fusion Core Reach LLC, and Unified Market Group LLC serve as fronts to acquire Extended Validation certificates from legitimate authorities.
Once a certificate becomes flagged or revoked, operators quickly register a new company under a similar generic name and obtain fresh credentials to maintain their operation’s legitimacy.
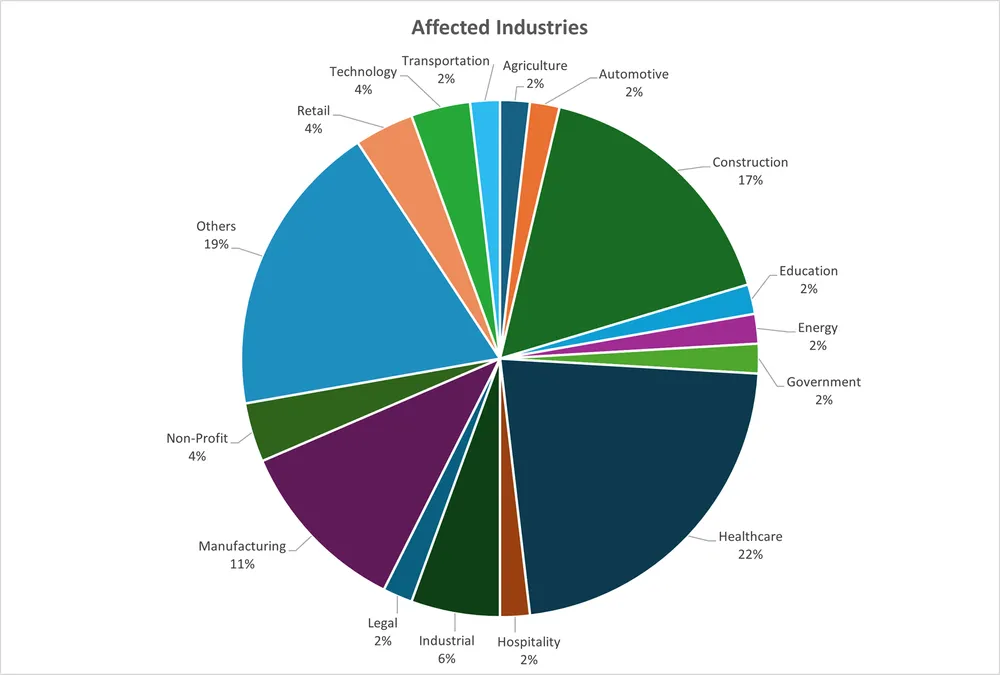
In terms of affected industries, telemetry data shows victims across multiple industries, but a clear concentration on health care, construction and manufacturing.
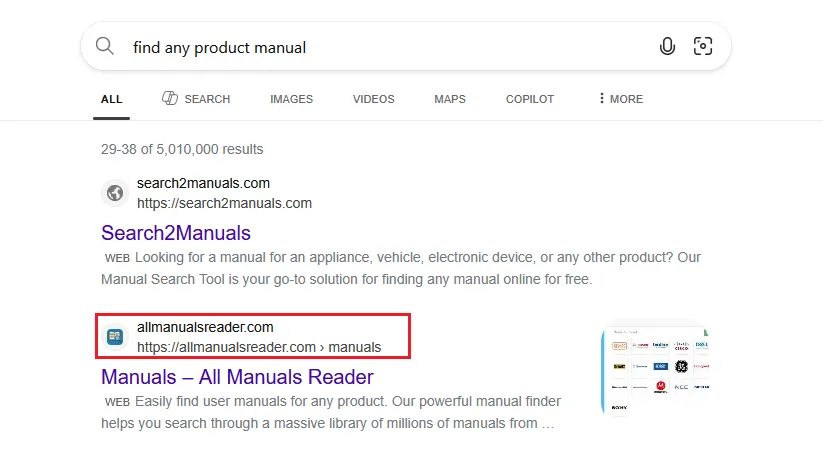
All download domains follow a consistent pattern using “download” as a subdomain, such as download.allmanualsreader.com or download.anyproductmanual.com, registered through NameCheap with Iceland-based privacy protection services.
The domains are registered for only one-year periods, allowing attackers to rebuild infrastructure after takedowns quickly.
Command and control servers initially used random domain-generated strings but have recently shifted to more recognizable names like get.latest-manuals.com to blend with regular network traffic.
Acronis telemetry data reveals that healthcare, construction, and manufacturing sectors face particularly high exposure to this campaign.
These industries frequently require workers to search online for product manuals of highly specialized equipment precisely the behavior that TamperedChef exploits through malvertising and optimized search results.
The difficulty in finding manuals in native languages may explain why English-speaking regions in the Americas show higher victim concentrations.
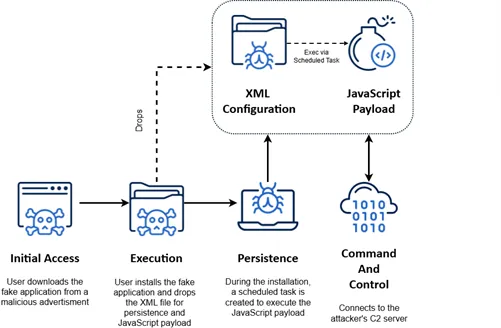
The attack chain begins when users encounter malicious advertisements or manipulated search results directing them to fake download sites.
Upon installation, the application appears completely legitimate, displaying license agreements and thank-you messages that reinforce the illusion of authenticity.
Behind the scenes, the installer drops an XML configuration file that creates a scheduled task, establishing persistence that executes every 24 hours with randomized delays to evade detection.
The JavaScript payload itself is heavily obfuscated using open-source obfuscation tools, making analysis extremely difficult.
Once active, the backdoor enables remote code execution, system fingerprinting through machine ID generation, and encrypted communication with command and control servers using XOR encryption and base64 encoding over HTTPS connections.
Multiple Threat Scenarios
Security researchers believe TamperedChef likely serves multiple purposes simultaneously. The campaign may function as an initial access broker, selling compromised system access to other criminal groups for profit.
While the delivery stages mirror earlier reports, this variant stands out because it relies on a scheduled task seeded by a dropped task.xml for persistence.
Given the concentration of healthcare victims, attackers could also be targeting sensitive patient data and credentials for monetization on dark web marketplaces.
The persistent backdoor access provides ideal conditions for future ransomware deployment, while opportunistic access to government or research institutions could enable espionage activities.
Timeline analysis shows the operators continuously adapting their tactics.
Early campaigns used three-year certificates and domain-generated algorithm patterns for command and control servers, but following multiple revocations, they shifted to short-lived certificates and human-readable domain names by mid-2025, demonstrating their commitment to evading security measures and maintaining operational continuity.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
