The Python-based information-stealing tool Xillen Stealer has reached versions 4 and 5, significantly expanding its targeting capabilities and functionality across platforms.
Documented initially by Cyfirma in September 2025, this cross-platform infostealer targets sensitive data, including credentials, cryptocurrency wallets, system information, and browser data, while employing sophisticated anti-analysis techniques to evade detection.
The latest updates introduce substantially expanded functionality that transforms Xillen Stealer into a comprehensive data harvesting platform.
The malware now targets credentials from password managers, social media accounts, and browser data from over 100 browsers.
It can extract cryptocurrency from more than 70 different wallets and includes support for Kubernetes configs, Docker scanning, and IoT device targeting.
Additionally, the stealer implements persistence mechanisms, polymorphic code generation, system hooks, and peer-to-peer command-and-control communications to maintain operational resilience.
Advanced AI Evasion Capabilities
A particularly notable feature is the AIEvasionEngine module, designed to help the malware evade AI-based and behavior-based detection systems including endpoint detection and response (EDR) solutions and sandboxes.
This engine mimics legitimate user and system behavior by simulating mouse movements, fake browser usage, and file network activity.
It injects statistical noise through random memory, CPU, and network operations while randomizing execution timing patterns with irregular delays to avoid anomaly detection.
The system further camouflages resource usage by adjusting CPU and memory allocation to imitate normal applications, obscures API calls with random patterns, and alters memory access patterns to bypass machine learning models.
Interestingly, the stealer includes an AITargetDetection class that claims to use artificial intelligence for identifying high-value targets.
However, technical analysis reveals the implementation relies entirely on rule-based pattern matching rather than actual machine learning algorithms.
The system identifies targets based on predefined indicators including cryptocurrency wallets, banking data, premium accounts, developer accounts, and business emails, with geographic scoring favoring nations like the United States, United Kingdom, Germany, and Japan.
The DevToolsCollector function demonstrates the stealer’s enterprise focus, extracting sensitive data from IDE configurations including VS Code, JetBrains products, and Sublime Text.
It targets cloud credentials from AWS, Google Cloud, Azure, and Digital Ocean, alongside SSH keys, Docker and Kubernetes configurations, database connection information, VPN settings, and API keys from environment files.
The BiometricCollector attempts to extract Windows Hello and biometric configuration data, while PasswordManagerCollector targets OnePass, LastPass, BitWarden, Dashlane, NordPass, and KeePass.
Wealth indicators such as keywords like CEO, trader, investor and VIP have also been defined in a dictionary but are not in use at this time, pointing towards the group’s intent to develop further in the future.
Additional collectors extract Single Sign-On tokens from Azure Active Directory and Kerberos systems, Time-Based One-Time Passwords from Authy Desktop and Microsoft Authenticator, and enterprise credentials from VPN clients and RDP systems.
A SuperExtendedApplication Collector scans for 160 different applications including Teams, Slack, Zoom, and security products.
Multi-Layered Exfiltration Methods
Data exfiltration employs multiple approaches including steganography techniques that hide stolen data within images using least significant bit encoding, NTFS alternate data streams, Windows Registry keys, and polyglot files.
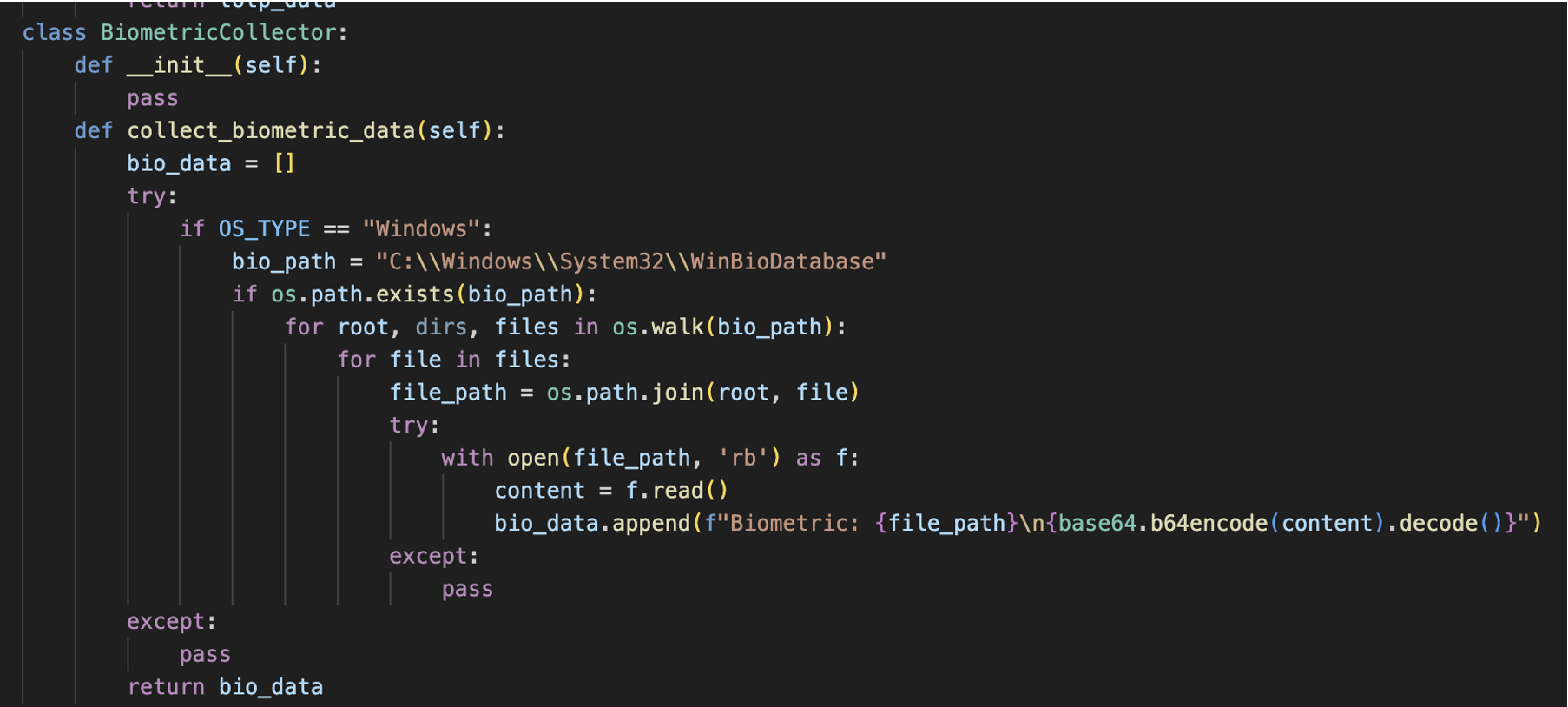
The BiometricCollector attempts to extract Windows Hello and biometric configuration data, while PasswordManagerCollector targets OnePass, LastPass, BitWarden, Dashlane, NordPass, and KeePass.
The CloudProxy module routes data through cloud service domains including AWS, GCP, and Azure, while the P2PEngine embeds instructions within blockchain transactions and utilizes anonymizing networks like Tor and I2P.
Marketed on Telegram with tiered licensing options, Xillen Stealer provides operators with a professional GUI for viewing exfiltrated data and managing infections.
While some components remain underdeveloped, the comprehensive feature set positions this stealer as a significant evolving threat to organizations managing sensitive credentials and cryptocurrency assets.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
