In October 2025, a significant breach exposed internal operational documents from APT35, also known as Charming Kitten, revealing that the Iranian state-sponsored group operates as a bureaucratized, quota-driven cyber-espionage unit with hierarchical command structures, performance metrics, and specialized attack teams.
The leaked materials provide an unprecedented window into how this Islamic Revolutionary Guard Corps Intelligence Organization (IRGC IO) affiliate runs a formalized intelligence collection apparatus focused on diplomatic, governmental, and corporate targets across the Middle East and Asia.
The leaked documents reveal APT35 functions as a militarized intelligence organization rather than a loose hacking collective.
Below him, Manouchehr Vosoughi Niri operates as a mid-level coordinator managing performance tracking and operational oversight.
The group deploys specialized teams with distinct technical lanes: an exploit development unit weaponizing Ivanti and Exchange/ProxyShell vulnerabilities; credential and access teams conducting LSASS dumps and token replay attacks; a phishing unit executing HERV (Human Engineering and Remote Validation) campaigns; and real-time monitoring teams tasked with sustained mailbox surveillance.
All items are cross-referenced in a DTI evidence repository, producing an end-to-end evidentiary chain from vulnerability research and exploitation.
Operators including Engineer Reza, Engineer Kian, and others are formally titled, salaried personnel whose work is monitored through standardized monthly performance reports measuring completed tasks, credential yields, phishing success rates, and mailbox dwell times.
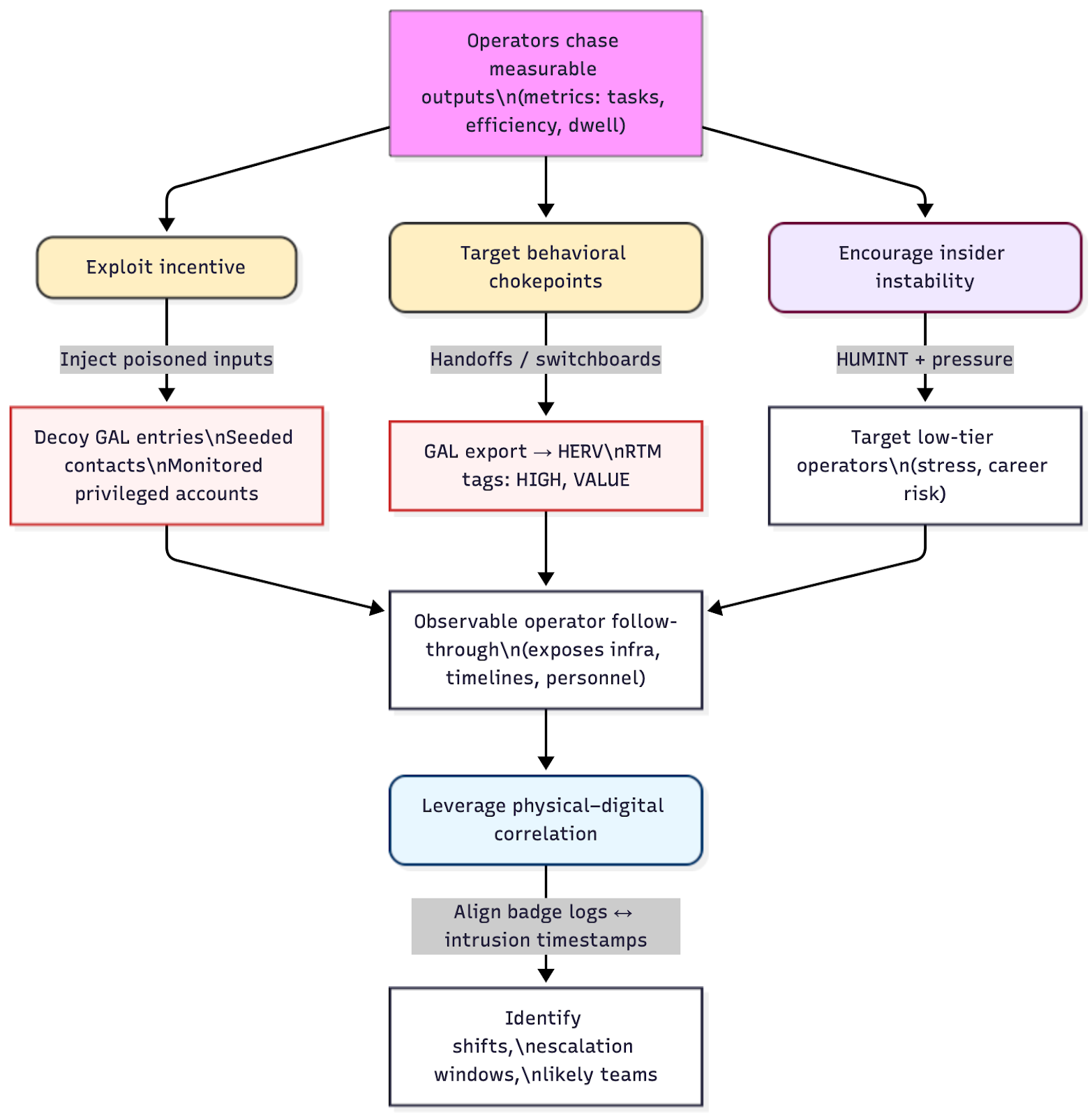
Critically, physical evidence confirms centralized operations. Badge entry and exit logs document that personnel work from a secured, on-premises facility, with timestamps aligning precisely with operational activity windows.
Each campaign corresponds to a named lead analyst, who oversees operational sub teams tasked with exploitation, credential harvesting, phishing operations, and real time mailbox monitoring (RTM).
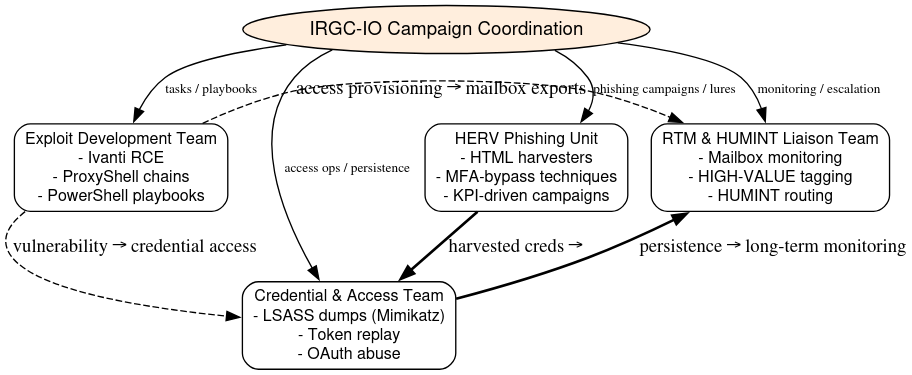
This centralization reinforces supervisory control and ensures synchronized campaign execution across teams.
Attack Methods and Campaign Tradecraft
APT35’s operational workflow follows a systematic, repeatable cycle designed for high-volume intelligence collection.
The group conducts dual-mode reconnaissance: broad internet scanning identifies vulnerable infrastructure, while manual refinement produces prioritized target lists focused on diplomatic, governmental, and telecommunications entities.
The primary exploitation vector centers on Microsoft Exchange infrastructure. The group weaponizes ProxyShell, Autodiscover, and Exchange Web Services (EWS) to gain initial access, then deploys ASPX webshells for persistence.
Once inside, operators extract Global Address Lists (GALs) and harvest plaintext credentials, which become both intelligence and operational infrastructure.
Persistence relies on credential-based mechanisms rather than fragile webshells. The group harvests credentials through LSASS dumps (processed with Mimikatz-style utilities) and token-replay attacks, converting initial access into sustainable footholds resistant to standard remediation.
At the apex sits Abbas Rahrovi, identified as a senior IRGC-IO cyber command authority overseeing a network of front companies that provide administrative cover for ongoing operations.
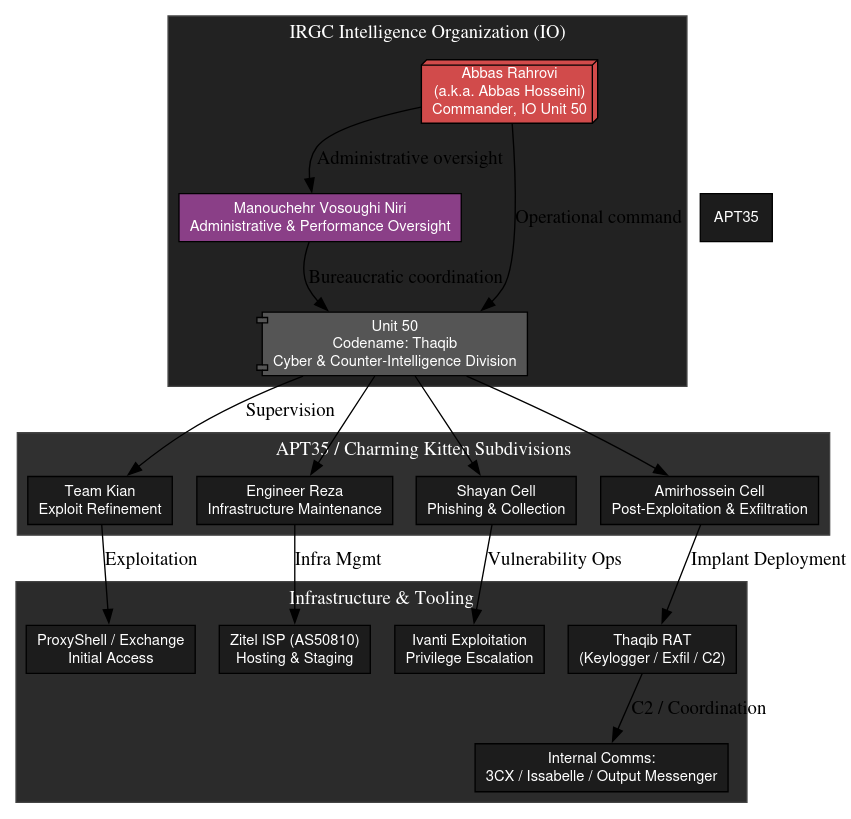
Post-exploitation tooling includes custom .NET webshells, Python parsers, and modified beacon-style implants deployed under obfuscated system-service names within ProgramData directories, enabling hands-on adversary control and lateral movement using WMIC and administrative share protocols.
Analysis of operational documentation reveals strategic, region-wide targeting rather than opportunistic compromise.
The primary geographic footprint encompasses Turkey, the Turkish Republic of Northern Cyprus, Lebanon, Kuwait, Saudi Arabia, Jordan, South Korea, and domestic Iranian targets.
High-value collection points include ministries of foreign affairs, telecommunications operators, energy providers, customs authorities, and managed service providers entities that provide both diplomatic intelligence and economic strategic advantage.
Documented targets include Türk Telekom (212.175.168.58), Nour Communication Co. Ltd in Saudi Arabia, Fast Communication Company Ltd in Kuwait, and South Korean infrastructure operators.
Each region faces tailored tasking aligned with Iranian intelligence priorities: Turkish targets yield NATO and regional political visibility; Saudi operations target GCC coordination and energy policy; Korean compromise supports technology and defense intelligence collection.
Bureaucratic Intelligence Collection Machinery
The leaked materials document a mature, operator-driven intrusion toolkit optimized for large-scale credential capture and sustained access.
The harvested contacts seed subsequent HERV phishing campaigns, creating a self-sustaining collection cycle where reconnaissance, exploitation, and social engineering continuously reinforce each other.
The group maintains hardened C2 infrastructure using encrypted channels, with command injection embedded in HTTP headers (notably Accept-Language fields) and static token fingerprints providing operational handshakes.
Exfiltration channels employ encrypted staging to cloud providers (Mega, Dropbox, ProtonDrive), SMTP relays through compromised Exchange systems, and DNS tunneling for covert communications.
Perhaps most revealing is the formalized, quota-driven operational culture embedded in monthly performance reviews and supervisor annotations.
Operators routinely file KPI reports enumerating hours worked, tasks completed, phishing success rates, and exploitation metrics.
This metrics-obsessed approach transforms cyber operations into a measurable production line, prioritizing volume and speed a dynamic that creates predictable behavioral signatures defenders can exploit.
The leaked documents also reveal operators’ attendance at ideological events, including a 2023 conference titled “Israel: The Fragile Mirror” where fifteen named individuals from the technical units were registered as attendees.
The exposure of this intelligence apparatus creates immediate operational imperatives for defenders.
Organizations should prioritize hardening Exchange infrastructure with enhanced logging, enforce phishing-resistant multi-factor authentication such as FIDO2, and deploy detection rules targeting scanning patterns, token-relay behavior, and anomalous mailbox access.
Hunting efforts should focus on characteristic artifacts: ASPX webshells under predictable paths, service masquerades within ProgramData directories, and suspicious Accept-Language HTTP headers embedding operator commands.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
