Security researchers at Socket have uncovered a deceptive Chrome extension called Crypto Copilot that masquerades as a legitimate Solana trading tool while secretly siphoning SOL from users’ swap transactions.
The malicious extension, published on June 18, 2024, extracts undisclosed fees by injecting hidden transfer instructions into every transaction users execute.
Crypto Copilot markets itself on the Chrome Web Store as a convenience tool enabling users to “execute trades instantly from your X feed.”
The extension integrates with popular Solana wallets, including Phantom and Solflare, displays token data from DexScreener, and routes trades through Raydium.
For traders following fast-moving token launches on X (formerly Twitter), the promise of one-click trading directly from social media feeds is appealing.
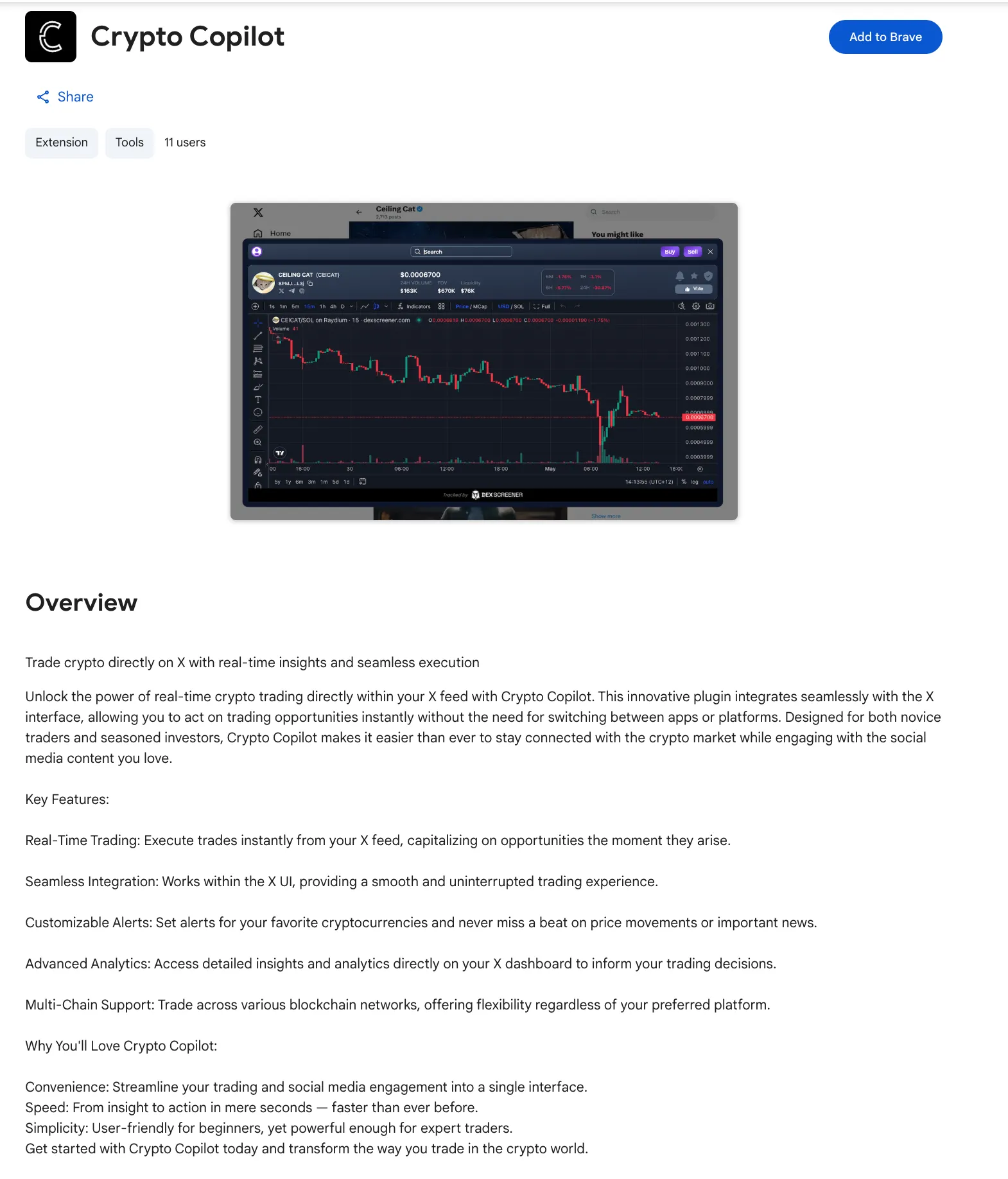
However, the Web Store listing makes no mention of fees, hidden transfers, or any additional charges a critical omission that proves central to the extension’s malicious design.
Behind the benign interface lies sophisticated code designed to extract SOL from unsuspecting users.
After assembling legitimate Raydium swap instructions, the extension calculates a platform fee using hardcoded parameters and appends a hidden SystemProgram.transfer instruction to send SOL to the attacker’s wallet: Bjeida13AjgPaUEU9xrh1iQMwxZC7QDdvSfg73oxQff7.
The fee structure charges users the greater of 0.0013 SOL or 0.05% of the swap amount. This means trades under 2.6 SOL incur the fixed minimum fee, while larger trades trigger the percentage-based charge. For example, a 100 SOL swap would extract 0.05 SOL directly to the attacker.
The malicious code uses aggressive minification and variable renaming to obscure the fee extraction logic.
Critically, the additional outbound transfer embeds itself within the same transaction as the legitimate swap, and most wallet confirmation screens fail to surface individual instructions clearly.
Users unknowingly sign what appears to be a single swap operation while both instructions execute atomically on-chain.
A Fabricated Infrastructure
Analysis reveals the extension maintains connections to a backend at crypto-coplilot-dashboard[.]vercel[.]app, ostensibly for wallet registration, points tracking, and referral reporting.
However, investigation shows neither the backend domain nor the main website (cryptocopilot[.]app) hosts any functional product.
The backend domain loads only a blank placeholder, while the main website sits parked by GoDaddy.
The typo in the backend hostname itself “coplilot” instead of “copilot” is inconsistent with any legitimate trading platform and suggests disposable infrastructure typical of malicious operations.
To date, on-chain analysis shows limited fee transfers to the attacker’s wallet, likely reflecting low distribution rather than low risk.
![Chrome Extension Malware Secretly Adds Hidden SOL Fees to Solana Swap Transactions 3 The backend domain used by the extension crypto-coplilot-dashboard[.]vercel.app loads.](https://cdn.sanity.io/images/cgdhsj6q/production/e7a75ebe07ebc88e52afd11fffabd0b46d25d725-2048x625.png?w=1600&q=95&fit=max&auto=format)
crypto-coplilot-dashboard[.]vercel.app loads.Nevertheless, the mechanism scales directly with transaction volume and size. Active traders with substantial holdings face cumulative losses that could become substantial over time, transforming the extension into a recurring revenue mechanism for the operator.
Recommendations for Users
At the time of writing, Crypto Copilot remains available on the Chrome Web Store, though Socket has submitted a takedown request to Google security team.
Avoid closed-source trading extensions requesting signing permissions, and install wallet extensions only from verified publisher pages rather than Chrome Web Store search results.
Users who installed Crypto Copilot should immediately migrate assets to clean wallets and revoke all connected sites.
Going forward, review each instruction in transactions before signing, particularly on Solana, and watch for unexpected SystemProgram.transfer instructions.
Similar patterns are likely to emerge in other Solana and EVM trading extensions, making vigilance essential.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
