GreyNoise Labs has launched a free tool called GreyNoise IP Check that lets users check if their IP address has been observed in malicious scanning operations, like botnet and residential proxy networks.
The threat monitoring firm that tracks internet-wide activity via a global sensor network says this problem has grown significantly over the past year, with many users unknowingly helping malicious online activity.
“Over the past year, residential proxy networks have exploded and have been turning home internet connections into exit points for other people’s traffic,” explains GreyNoise.

“Sometimes folks knowingly install software that does this in exchange for a few dollars. More often, malware sneaks onto devices, usually via nefarious apps or browser extensions, and quietly turns them into nodes in someone else’s infrastructure.”
While there are ways to determine if someone has become part of malicious botnet activity, like examining device logs, configurations, network traffic, and activity patterns, a tool that simply checks the IP address is the least intrusive method
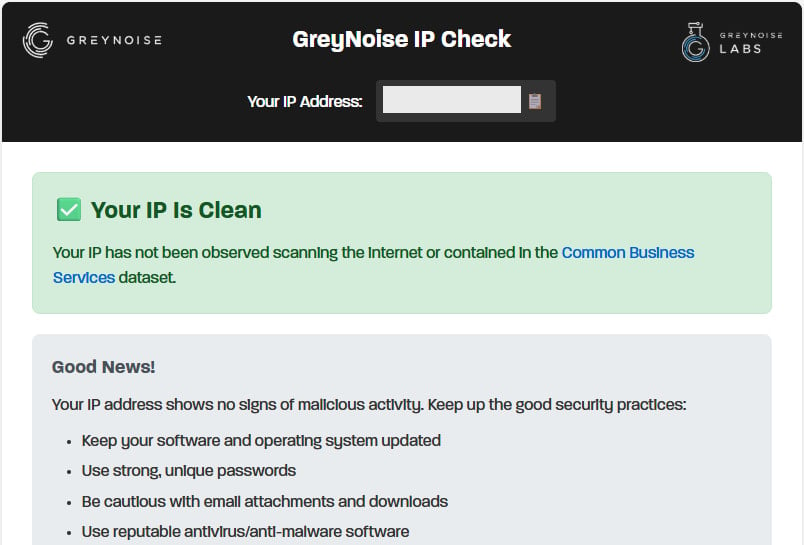
People visiting the scanner’s webpage will get one of the three possible results:
- Clean: No malicious scanning activity detected.
- Malicious/Suspicious: The IP has shown scanning behavior. Users should investigate devices on their network.
- Common Business Service: The IP belongs to a VPN, corporate network, or cloud provider, and the scanning activity is normal for those environments.
Source: BleepingComputer
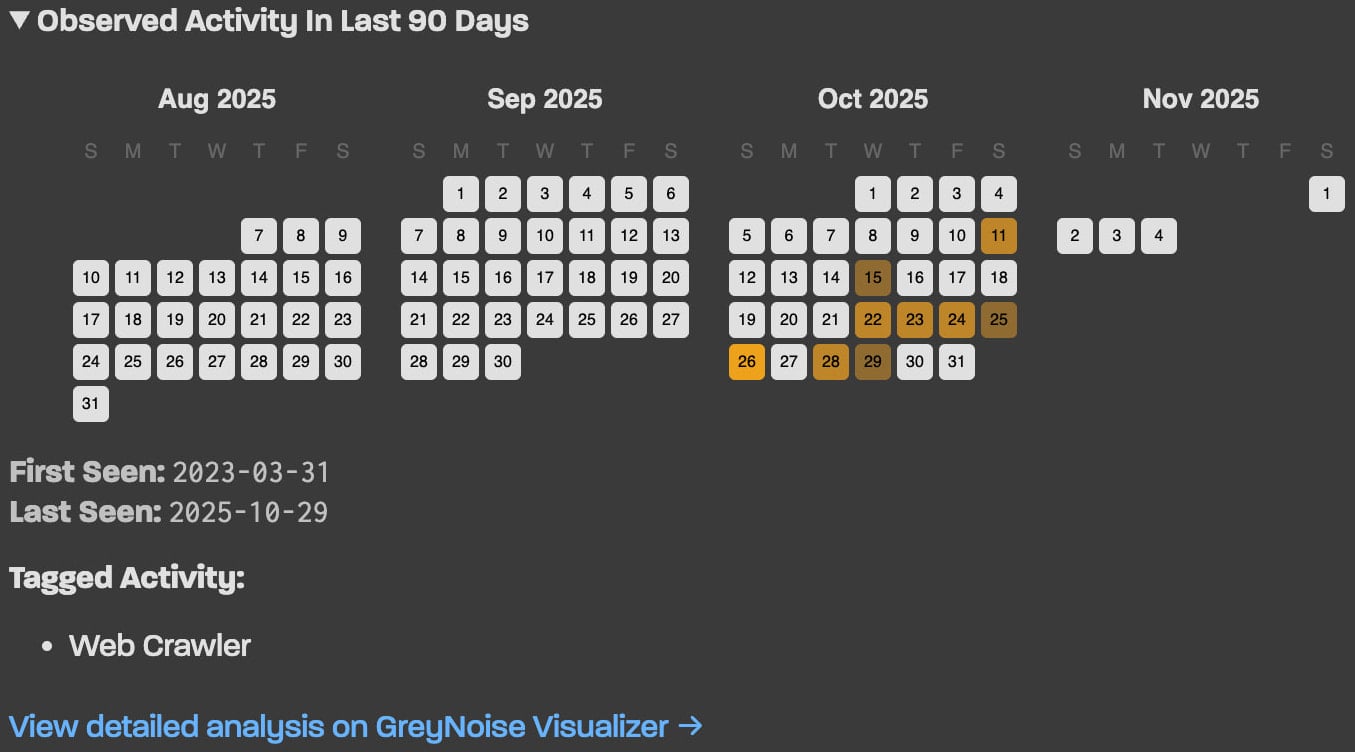
When any activity is correlated with the provided IP address, the platform will also include a 90-dayhistorical timeline, which may help pinpoint a potential infection point.
For example, when the installation of a bandwidth-sharing client or a shady application precedes malicious scanning, strong correlations can be made that enable remediation action.
Source: GreyNoise
For more technical users, GreyNoise also provides an unauthenticated, rate-limit-free JSON API accessible via curl, which can be integrated into scripts or checking systems.
If your scan results show ‘Malicious/Suspicious,’ it’s a good idea to start the investigation by running malware scans on all devices on the same network, especially focusing on devices like routers and smart TVs.
Users are advised to update their devices to the latest available firmware, change admin credentials, and disable remote access features if they’re not needed.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
