Pakistan-linked cyberespionage group APT36 (Transparent Tribe) has escalated its campaign against Indian government institutions with the deployment of sophisticated Python-based ELF malware specifically designed to compromise Linux-based BOSS operating environments, according to research published by CYFIRMA.
The threat actor, historically focused on Windows systems, has demonstrated expanded technical maturity through multi-platform tooling that bypasses conventional security controls across heterogeneous government infrastructure.
The campaign leverages spear-phishing emails containing weaponized Linux shortcut files that masquerade as legitimate documents while executing malicious payloads in the background.
The attack initiates through Analysis_Proc_Report_Gem_2025.zip, an archive containing a malicious .desktop shortcut file that appears as a standard document.
Unlike directly distributing easily detectable ELF binaries, APT36 conceals malicious logic within Base64-encoded strings inside the shortcut’s Exec field.
When executed, the file displays a password-protected decoy PDF while silently retrieving additional payloads from attacker-controlled infrastructure.
The .desktop entry downloads components from two primary locations: a decoy document from lionsdenim[.]xyz and malicious payloads from 185.235.137.90:32587.
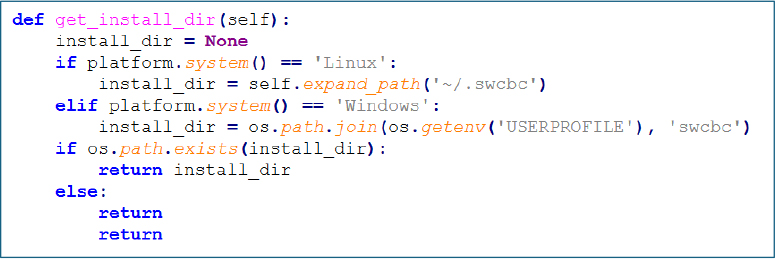
The retrieved files include swcbc, a 64-bit ELF executable, and swcbc.sh, a persistence-enabling shell script, both saved to /tmp/ with execution permissions before launching in the background.
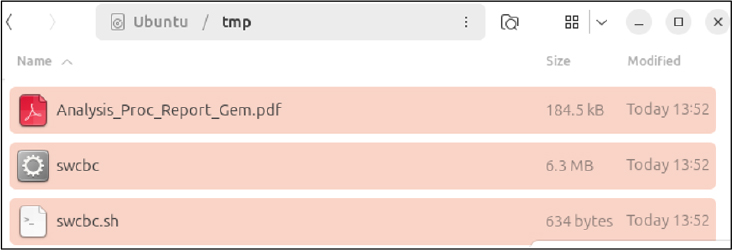
Static analysis reveals the ELF binary is a Python-based Remote Administration Tool (RAT) compiled with PyInstaller, designed for seamless operation across Linux and Windows environments.
However, because the PDF is password protected, LibreOffice displays a password prompt, which may draw the user’s attention.
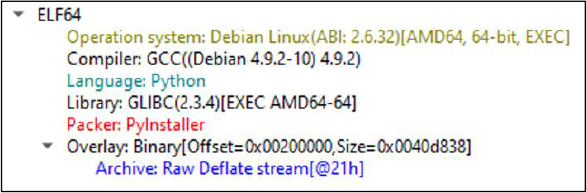
The malware establishes persistence through systemd user services on Linux and registry modifications on Windows, ensuring survival across reboots without requiring elevated privileges.
Upon execution, the implant performs comprehensive system reconnaissance, collecting OS details, hostname, username, and network information, before generating a unique identifier from MAC addresses and usernames.
This tracking mechanism enables attackers to maintain persistent identification of compromised hosts across multiple operational sessions.
The RAT supports a complete command set including directory traversal, file transfer capabilities, arbitrary command execution, Python code injection, screenshot capture, and automated data archiving for bulk exfiltration.
Attackers can remotely deploy additional payloads, harvest sensitive documents, or execute shell commands with full system access.
The binary metadata indicates that it was built on a Debian Linux environment using GCC 4.9.2 and is linked against GLIBC 2.3.4 for the AMD64 architecture.
The campaign infrastructure exhibits classic short-lived operational security patterns. Domain lionsdenim[.]xyz, registered through Namecheap on November 3, 2025, is 22 days old and resolves to 67.223.118.206, a Los Angeles-based server hosting over 275 domains.
The payload delivery server at 185.235.137.90 operates from Frankfurt, Germany, and has been confirmed as malicious by multiple threat intelligence sources.
The .xyz top-level domain choice reflects APT36’s preference for low-cost, minimally verified registration options that provide operational flexibility and rapid infrastructure turnover, complicating takedown efforts and attribution.
Strategic Implications
This campaign marks a significant evolution in APT36’s operational doctrine, moving beyond traditional Windows malware to embrace Linux-targeted tooling tailored for India’s indigenous BOSS operating system.
The group’s ability to customize delivery techniques based on victim ecosystems demonstrates a deep understanding of regional technology deployments and enhances prospects for long-term persistence within critical government networks.
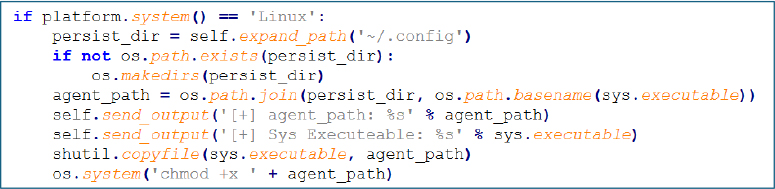
The incorporation of systemd-based persistence mechanisms, cross-platform compatibility, and adaptive phishing techniques underscores a maturing threat actor committed to overcoming platform diversity.
This development poses elevated risks for interconnected government agencies and third-party partners operating hybrid Windows-Linux environments.
Security teams should monitor for .desktop file executions containing embedded commands, track systemd user service creations, and flag network connections to the identified IOCs.
Organizations using BOSS Linux should implement application allowlisting, restrict LibreOffice macro execution, and deploy endpoint detection capabilities capable of identifying PyInstaller-packaged binaries.
The campaign highlights the urgent need for Linux-specific threat detection in government sectors traditionally focused on Windows security, as APT36 continues refining its capabilities for sustained intelligence collection across India’s critical infrastructure.
INDICATORS OF COMPROMISE
| S. No | Indicator | Remarks |
|---|---|---|
| 1 | defa2e29e45168471ce451196e1617b9659b3553b125e5464b1db032d7eac90a | Block |
| 2 | 5ff9777aac434cae5995bf26979b892197e3f0e521c73f127c2e2628e84ef509 | Block |
| 3 | 40a59422fa486c7ae214d6e816c2fd00bf4d75c081993a49c4bc22bb0165b7fe | Block |
| 4 | 4f4e795555740038904bc6365c58536a660d7f3206ac1a4e89612a9fdf97f6dd | Monitor |
| 5 | lionsdenim[.]xyz | Block |
| 6 | 185[.]235[.]137[.]90 | Monitor |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
