A new malware campaign has emerged that exploits the trust users place in popular applications.
Threat actors are distributing trojanized installers for Telegram, WinSCP, Google Chrome, and Microsoft Teams to deploy ValleyRat, a remote access trojan designed for long-term system compromise.
The campaign has been attributed to the China-aligned APT group known as Silver Fox, which has remained active since at least 2022.
The infection begins when victims download what appears to be a legitimate application installer through spear-phishing emails or malicious advertisements.
On the surface, users see a normal installation interface, but hidden processes run silently in the background.
The malware stages files, deploys kernel-level drivers, tampers with endpoint security, and ultimately launches a ValleyRat beacon that maintains persistent access to the compromised system.
Nextron Systems security researchers identified this campaign through their detailed analysis of the entire infection chain.
Their investigation revealed that the attackers combine multiple layers of obfuscation, endpoint security tampering, and kernel-level techniques to evade detection while establishing command-and-control communications with remote servers.
.webp)
The distribution primarily occurs through trojanized Telegram installers. One analyzed sample, named tg.exe, carries the SHA-256 hash 9ede6da5986d8c0df3367c395b0b3924ffb12206939f33b01610c1ae955630d1.
Despite displaying a genuine Telegram Desktop 6.0.2 interface, closer inspection reveals notable inconsistencies.
.webp)
The PE header timestamp dates to 2019, while its first VirusTotal submission occurred in August 2025, representing an unusual six-year gap for a frequently updated application.
Infection Mechanism and Defense Evasion
Once executed, the installer creates the directory C:ProgramDataWindowsData and drops essential files, including a renamed 7-Zip binary (funzip.exe) and an encrypted archive disguised as main.xml.
The malware then uses PowerShell to add a Microsoft Defender exclusion for the entire C: drive, effectively silencing antivirus protection.
The archive extraction command reveals the embedded password:-
"C:ProgramDataWindowsDatafunzip.exe" x -y -phtLcENyRFYwXsHFnUnqK -o"C:ProgramDataWindowsData" "C:ProgramDataWindowsDatamain.xml"This extraction deploys men.exe, the main orchestrator that performs environmental reconnaissance by scanning for security processes, including Microsoft Defender’s MsMpEng.exe and Chinese security products like ZhuDongFangYu.exe and 360tray.exe.
.webp)
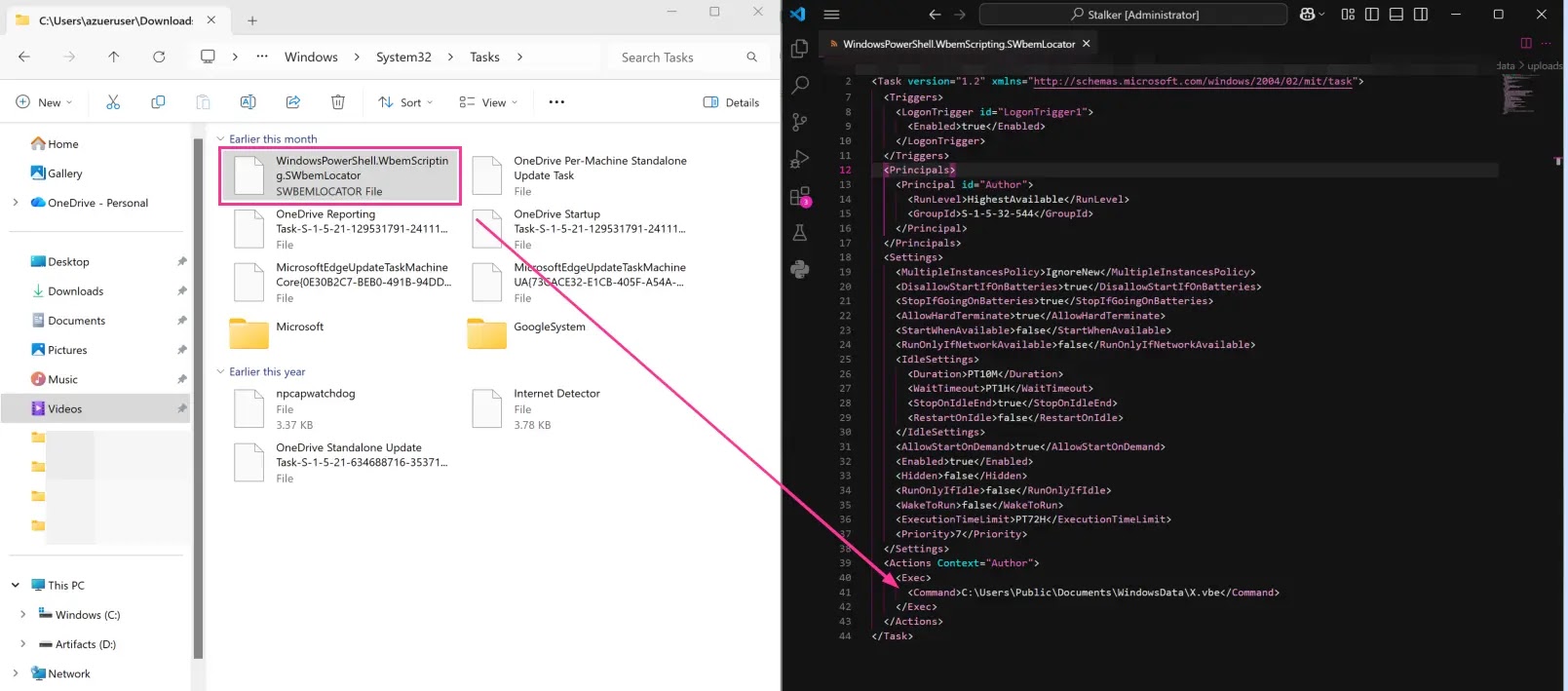
The campaign establishes persistence through a scheduled task named WindowsPowerShell.WbemScripting.SWbemLocator, designed to mimic legitimate Windows components, which executes an encoded VBScript launching the ValleyRat beacon for continued system access.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
