A newly discovered security flaw in Windows shortcut files is being actively used by hackers to target diplomatic organisations.
The vulnerability allows attackers to conceal malicious commands within shortcut files (.lnk), making them invisible to users.
The Discovery and Initial Rejection
The issue was first highlighted in March 2025 by researchers at Trend Micro. They found that attackers were creating Windows shortcuts that looked harmless but contained dangerous commands.
When a user right-clicked a file to view its “Properties,” the “Target” field would show only blank spaces or harmless text.
This happened because the “Target” field in Windows only displayed the first 260 characters of the command.
Attackers realised they could fill this space with “whitespace” (blank characters) to conceal their malicious code, such as a PowerShell script, from view. Even if a suspicious user tried to check the file’s details, the dangerous part remained hidden.
At the time, Microsoft decided this was not a security vulnerability worth fixing, arguing that users are already warned when opening files from the internet.
The situation changed in October 2025. Security firm Arctic Wolf reported that a Chinese-affiliated hacking group, known as UNC6384, was using this exact trick to attack diplomatic entities in Hungary and Belgium.
The attackers sent malicious shortcuts that appeared to be PDF documents.
Following these attacks, the issue was assigned a formal tracking number, CVE-2025-9491.
In November 2025, Microsoft quietly addressed the issue. Instead of issuing a traditional security patch to block the attack, they updated the Windows user interface.
Now, the “Properties” window displays the entire command string, regardless of its length. However, critics argue this may not be enough, as the long text is crammed into a small box, and users might still fail to spot the malicious code hidden at the end.
Security company 0patch has released an alternative solution. They argue that legitimate shortcuts created by users rarely exceed 260 characters. Therefore, their “micropatch” actively blocks suspicious behavior.
If a user tries to open a shortcut file with a “Target” longer than 260 characters, the 0patch fix intervenes.
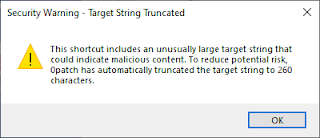
It cuts off the command at 260 characters and alerts the user that a suspicious file was shortened. This effectively neutralises the hidden malicious code without relying on the user to spot it manually.
0patch has made this fix available for multiple versions of Windows, including Windows 10, Windows 11, and several Windows Server editions, some of which did not receive an official fix from Microsoft.
Users are advised to be highly cautious when clicking on shortcut files (.lnk), especially if they arrive via email or look like documents.
Ensuring your Windows systems are fully updated is critical. For those seeking additional protection or running older systems, third-party patches like those from 0patch can help block these attacks entirely.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
