A new information stealer called Sryxen has emerged in the underground malware market, targeting Windows systems with advanced techniques to harvest browser credentials and sensitive data.
Sold as Malware-as-a-Service, this C++ based threat demonstrates how modern stealers are adapting to overcome browser security improvements, particularly Google Chrome’s recently implemented App-Bound Encryption protection.
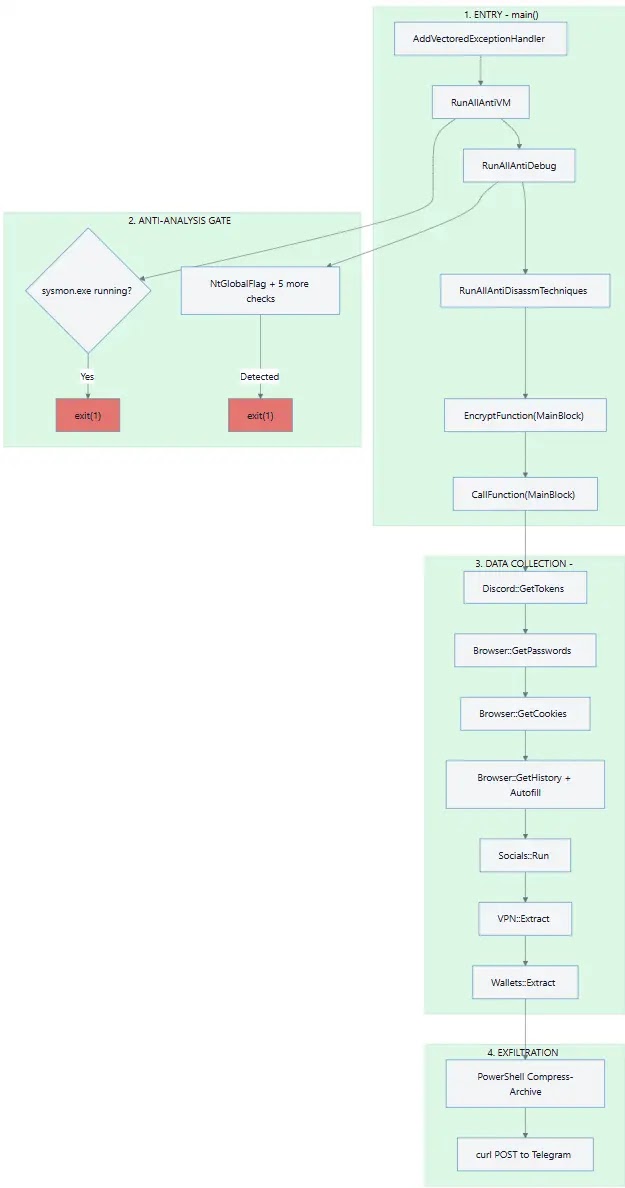
Sryxen operates as a smash-and-grab credential harvester, designed for quick execution without establishing persistence on infected machines.
The malware targets Chrome version 127 and above, where Google introduced App-Bound Encryption to protect cookies and sensitive browser data.
Instead of attempting to crack this encryption directly, Sryxen takes an innovative approach by launching Chrome in headless mode and using the browser’s own DevTools Protocol to request decrypted cookie data, effectively bypassing the security measure entirely.
.webp)
DeceptIQ security researchers identified that Sryxen employs multiple layers of protection to avoid detection and analysis.
The malware uses Vectored Exception Handling-based code encryption, keeping its main payload encrypted at rest and only decrypting it during execution through exception handling mechanisms.
This technique makes static analysis challenging, as the malicious code appears as garbage data when examined without running it.
Additionally, the stealer implements six separate anti-debug checks, including NtGlobalFlag inspection and PEB analysis, terminating execution if debugging tools are detected.
Chrome Encryption Bypass Mechanism
The most significant innovation in Sryxen is its approach to stealing Chrome cookies protected by App-Bound Encryption.
When the malware detects Chrome version 127 or higher, it abandons traditional database extraction methods. Instead, it terminates any running Chrome processes and relaunches the browser with specific command-line arguments including –headless, –remote-debugging-port, and –user-data-dir parameters.
.webp)
These flags enable remote debugging capabilities without displaying any visible windows.
Once Chrome launches in this configuration, Sryxen connects to the debugging port via WebSocket and sends a DevTools Protocol command requesting all cookies through the Network.getAllCookies method.
.webp)
Chrome processes this request internally, decrypting the cookies using its own App-Bound Encryption key and returning the plaintext data to the stealer. The decrypted cookies never touch the disk, making file-based monitoring ineffective.
After receiving the data, Sryxen terminates the Chrome process and continues harvesting other browser information, passwords, and cryptocurrency wallet data before compressing everything into an archive and uploading it to a Telegram bot controlled by the attackers using curl commands executed through PowerShell.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
