A severe remote code execution vulnerability in the Sneeit Framework WordPress plugin is under active exploitation, with attackers launching thousands of attacks within hours of public disclosure.
WordPress site administrators must immediately update to version 8.4 or later to prevent complete site compromise.
On June 10th, 2025, a remote code execution vulnerability was discovered in Sneeit Framework, a WordPress plugin installed on approximately 1,700 active WordPress sites.
The vulnerability, assigned CVE-2025-6389 with a critical CVSS rating of 9.8, affects all versions of the plugin up to and including version 8.3.
The vendor responded with a security patch released on August 5th, 2025, but the vulnerability remained largely unknown to the public until Wordfence publicly disclosed it in their Intelligence Vulnerability Database on November 24th, 2025.
The vulnerability lies in the sneeit_articles_pagination_callback() function, which accepts user-supplied input and passes it directly to PHP’s call_user_func() without any validation or restrictions.
WordPress Plugin Vulnerability
This design flaw allows unauthenticated attackers to call arbitrary PHP functions with arbitrary parameters, effectively executing any code they choose on the affected server.
The plugin is particularly dangerous because it is bundled in multiple premium WordPress themes, expanding its potential reach beyond the official plugin repository.
Attackers have wasted no time exploiting this vulnerability. Within hours of the public disclosure, exploitation attempts flooded the internet.
The Wordfence Firewall has already blocked over 131,000 exploit attempts targeting this vulnerability.
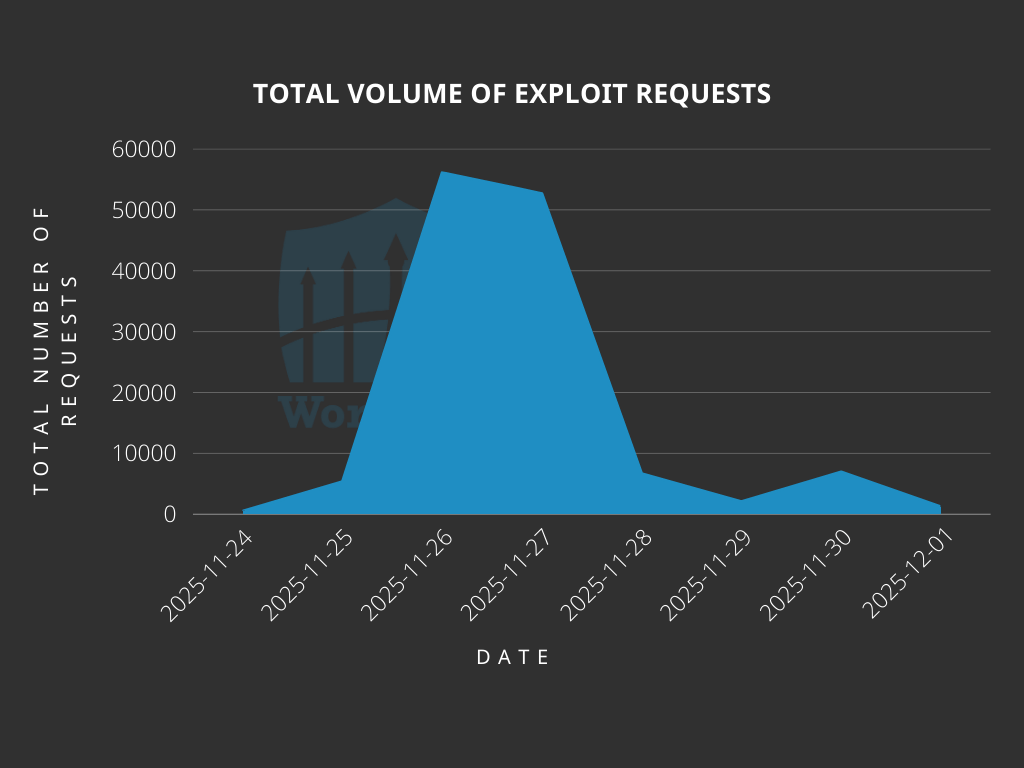
Attack volumes spiked dramatically on November 26th and 27th, indicating coordinated scanning and exploitation campaigns.
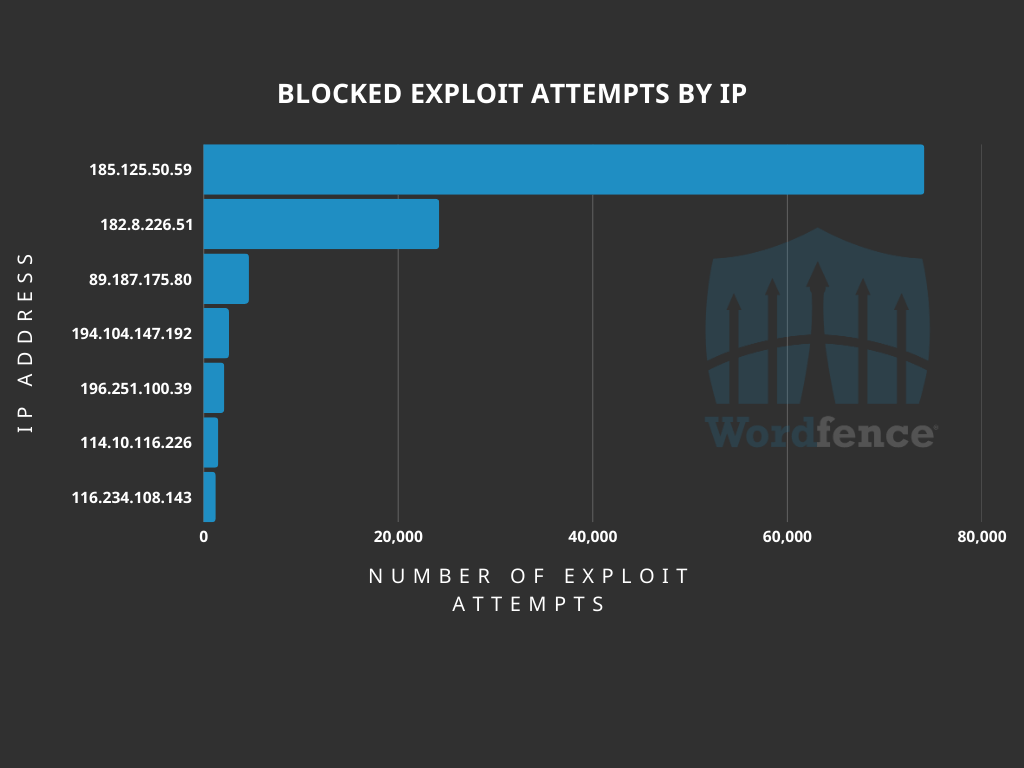
The attacks originate from multiple IP addresses, with one address (185.125.50.59) alone responsible for over 74,000 blocked requests.
The exploitation techniques observed in the wild demonstrate the severe nature of the threat.
Attackers are using multiple attack vectors to gain control of compromised websites. In some cases, attackers leverage the vulnerability to create new administrative user accounts using the wp_insert_user() function, granting themselves persistent access to the WordPress admin panel.
In other instances, attackers execute system commands to download and execute malicious PHP files containing backdoors, allowing them to maintain hidden access even if the vulnerability is patched.
Millions of WordPress Sites at Risk
Some reconnaissance attempts use the phpinfo() function to gather information about the target server’s PHP configuration before launching more targeted attacks.
The threat was not entirely unexpected to the security community. Wordfence Premium, Care, and Response customers received protective firewall rules on June 23rd, 2025, nearly six months before public disclosure.
This early protection allowed paid users to defend their sites long before the vulnerability became widely known.
Free Wordfence users received the same protection after the standard 30-day delay on July 23rd, 2025. However, sites without Wordfence protection or those using outdated plugin versions remain highly vulnerable.
Site administrators should prioritize updating the Sneeit Framework plugin to version 8.4 or later immediately.
Given the active exploitation and the critical nature of the vulnerability, delaying this update significantly increases the risk of complete site compromise.
Attackers can inject backdoors, steal sensitive data, deface websites, or hijack sites for malware distribution.
For additional protection, site owners without security plugins should consider implementing a web application firewall or installing Wordfence to block ongoing exploitation attempts while updates are deployed across their infrastructure.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
