Threat actors have been exploiting a command injection vulnerability in Array AG Series VPN devices to plant webshells and create rogue users.
Array Networks fixed the vulnerability in a May security update, but has not assigned an identifier, complicating efforts to track the flaw and patch management.
An advisory from Japan’s Computer Emergency and Response Team (CERT) warns that hackers have been exploiting the vulnerability since at least August in attacks targeting organizations in the country.
The agency reports that the attacks originate from the IP address 194.233.100[.]138, which is also used for communications.
“In the incidents confirmed by JPCERT/CC, a command was executed attempting to place a PHP webshell file in the path /ca/aproxy/webapp/,” reads the bulletin (machine translated).
The flaw impacts ArrayOS AG 9.4.5.8 and earlier versions, including AG Series hardware and virtual appliances with the ‘DesktopDirect’ remote access feature enabled.
JPCERT says that Array OS version 9.4.5.9 addresses the problem and provides the following workarounds if updating is not possible:
- If the DesktopDirect feature is not in use, disable all DesktopDirect services
- Use URL filtering to block access to URLs containing a semicolon
Array Networks AG Series is a line of secure access gateways that rely on SSL VPNs to create encrypted tunnels for secure remote access to corporate networks, applications, desktops, and cloud resources.
Typically, they are used by large organizations and enterprises that need to facilitate remote or mobile work.
Macnica’s security researcher, Yutaka Sejiyama, reported on X that his scans returned 1,831 ArrayAG instances worldwide, primarily in China, Japan, and the United States.
The researcher verified that at least 11 hosts have the DesktopDirect feature enabled, but cautioned that the possibility of more hosts with DesktopDirect active is significant.
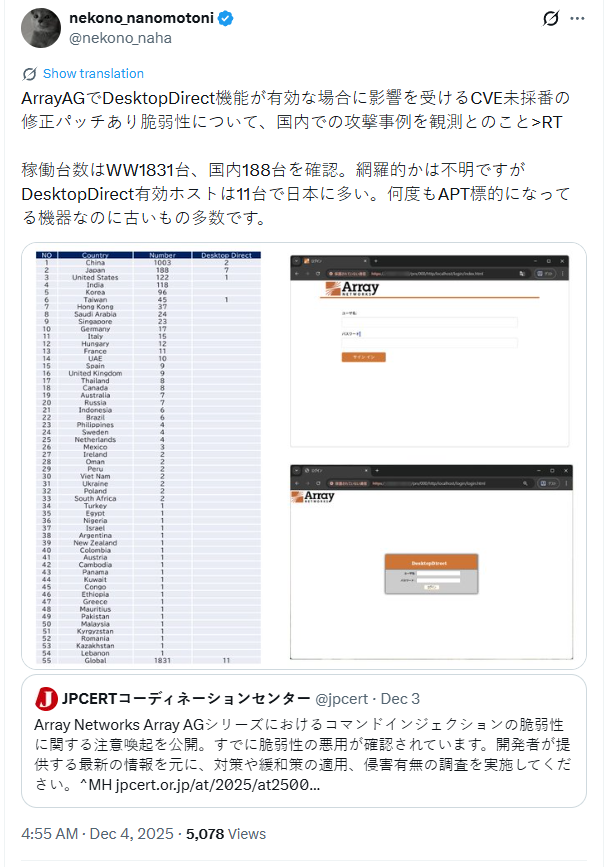
“Because this product’s user base is concentrated in Asia and most of the observed attacks are in Japan, security vendors and security organizations outside Japan have not been paying close attention,” Sejiyama told BleepingComputer.
BleepingComputer contacted Array Networks to ask whether they plan to publish a CVE-ID and an official advisory for the actively exploited flaw, but a reply was not available by publication time.
Last year, CISA warned about active exploitation targeting CVE-2023-28461, a critical remote code execution in Array Networks AG and vxAG ArrayOS.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
