A sophisticated malware campaign is leveraging a weaponized Foxit PDF Reader to target job seekers through email-based attacks, deploying ValleyRAT.
This remote access trojan grants threat actors complete system control and data exfiltration capabilities.
Security researchers have identified a significant uptick in this campaign, which combines social engineering, obfuscation techniques, and dynamic-link library (DLL) sideloading to compromise unsuspecting users.
ValleyRAT represents a critical threat to both individual job seekers and organizations with HR personnel, including recruiters and sourcing specialists.
Once successfully deployed, the malware enables threat actors to monitor system activity, steal sensitive information, and maintain persistent access to compromised devices.
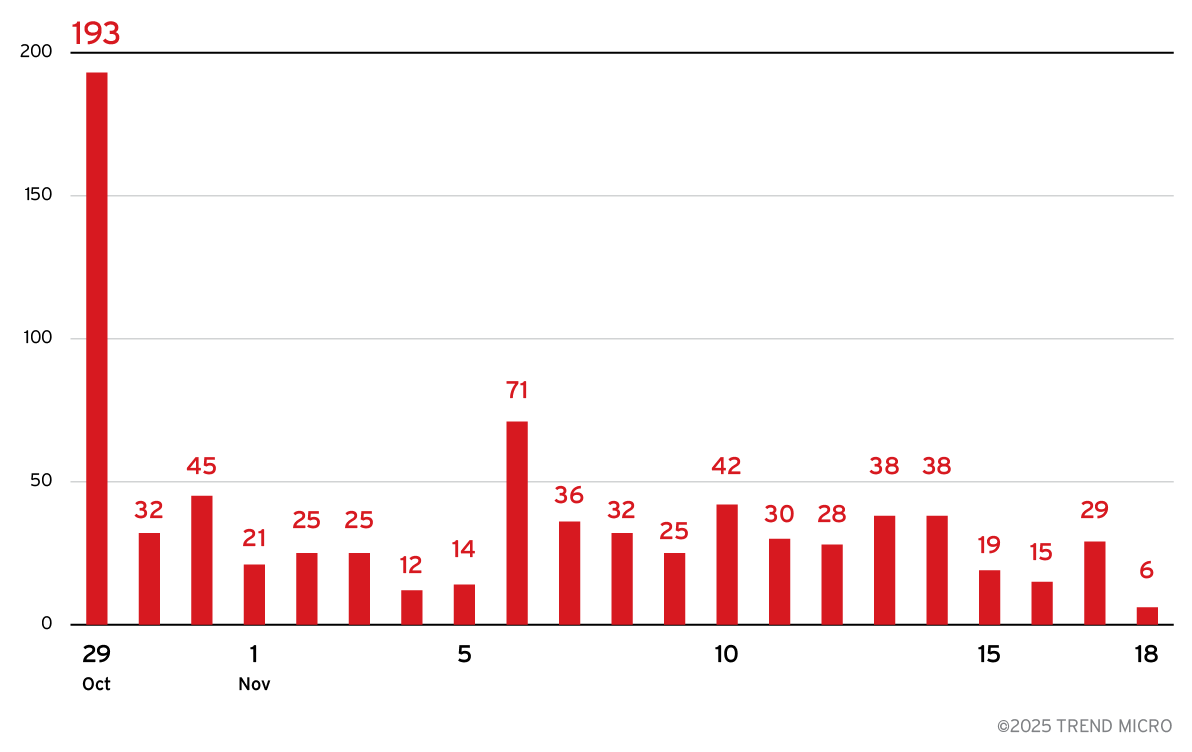
Recent observations show that beyond their usual targets of Chinese-speaking users, ValleyRAT actors now appear to be going after job seekers in general as well.
The campaign demonstrates a marked escalation in cybercriminal sophistication, integrating multiple attack vectors to maximize success rates and evade security defenses.
Exploiting Job Search Urgency
The campaign exploits the psychological vulnerabilities inherent in job seeking. Threat actors distribute archive files with recruitment-themed names such as “Overview_of_Work_Expectations.zip,” “Candidate_Skills_Assessment_Test.rar,” and “Authentic_Job_Application_Form.zip” through email.
These deceptive lures prey on the emotional strain and urgency experienced by job seekers, reducing their natural caution and increasing the likelihood of rapid file downloads.
The emotional intelligence of this approach is deliberate: job seekers actively monitor for opportunities and tend to download attachments quickly, often overlooking warning signs that might otherwise trigger suspicion.
This psychological manipulation directly contributes to the campaign’s exceptional success rate, corroborated by telemetry data showing a significant spike in ValleyRAT detections at the end of October.
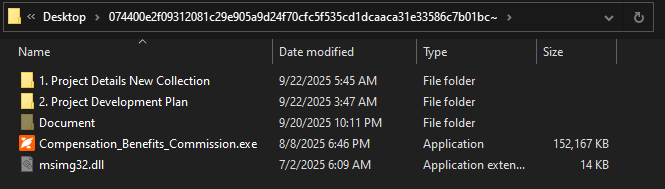
The technical execution demonstrates sophisticated engineering. Archive files contain a renamed version of FoxitPDFReader.exe, disguised with recruitment-related filenames such as “Compensation_Benefits_Commission.exe” and bearing the legitimate Foxit logo as its icon.
Most users assume such files contain PDF documents rather than executables, creating the initial deception layer.
Upon execution, the malware leverages DLL sideloading exploiting the Windows DLL search order mechanism to load malicious code.
The archive contains a hidden msimg32.dll alongside deeply nested directory structures filled with underscore-named subfolders designed to obscure the malware’s presence.
While users view a decoy PDF containing fake job details and salary information, ValleyRAT silently executes in the background.
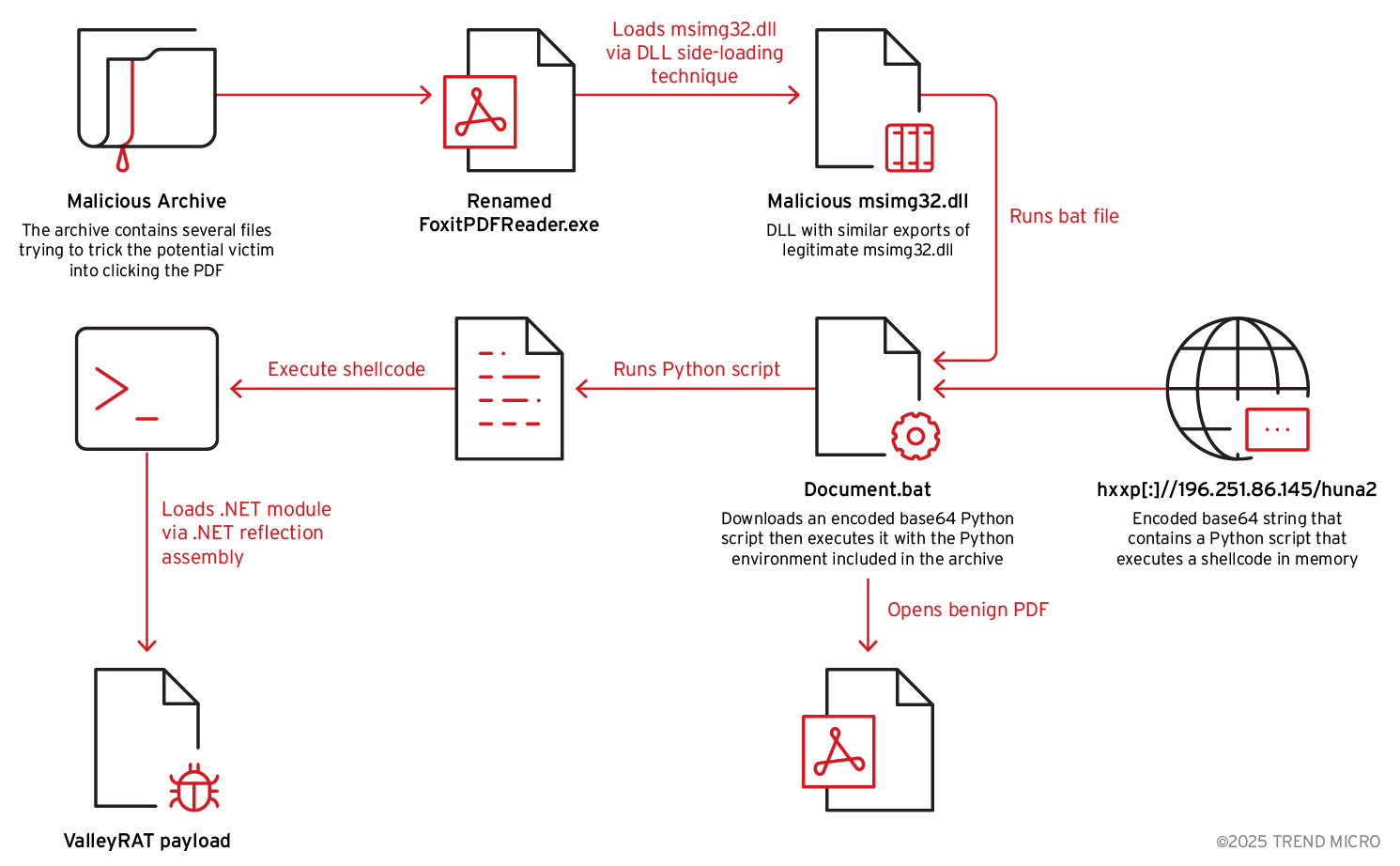
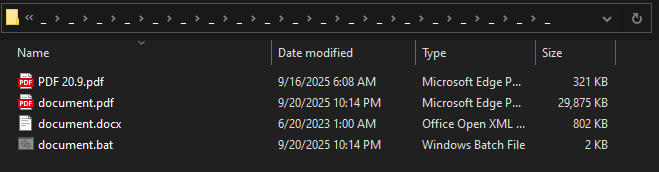
The infection chain involves a sophisticated multi-stage deployment process. A batch file (document.bat) extracts a disguised 7-Zip executable (masquerading as document.docx) that retrieves a Python environment from within a document.pdf file.
The renamed Python interpreter (zvchost.exe) then executes a shellcode loader that downloads base64-encoded malicious scripts from command-and-control servers. This chain ultimately establishes persistent access through autorun registry entries.
Data Exfiltration and Persistence
The deployed ValleyRAT payload systematically steals data from users’ internet browsers, capturing credentials, browsing history, and other sensitive information.
Python script can be executed on the target system even if Python is not pre-installed, leveraging the document.bat script to automate the process.
The malware communicates with C&C infrastructure using self-signed certificates with randomized common names and outdated TLS versions characteristics typical of off-the-shelf RAT builders.
Organizations can leverage security platforms like Trend Vision One to detect and block the indicators of compromise associated with this campaign.
Security awareness training remains critical in helping users identify recruitment-themed phishing attempts and suspicious executable files.
By understanding these sophisticated attack methodologies, both individuals and enterprises can implement proactive defenses to prevent compromise and data theft.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
