In November 2025, security researchers at Raven AI identified a sophisticated zero-day phishing campaign impersonating the Income Tax Department of India, targeting enterprises across the country with a multi-stage malware chain.
The attack combined authentic-looking government communications with advanced evasion techniques, delivering both a shellcode-based RAT loader and a malicious executable disguised as a GoTo Resolve updater.
The campaign’s success lay in its ability to exploit trust in government authority while bypassing traditional email security defenses that typically rely on signature-based detection.
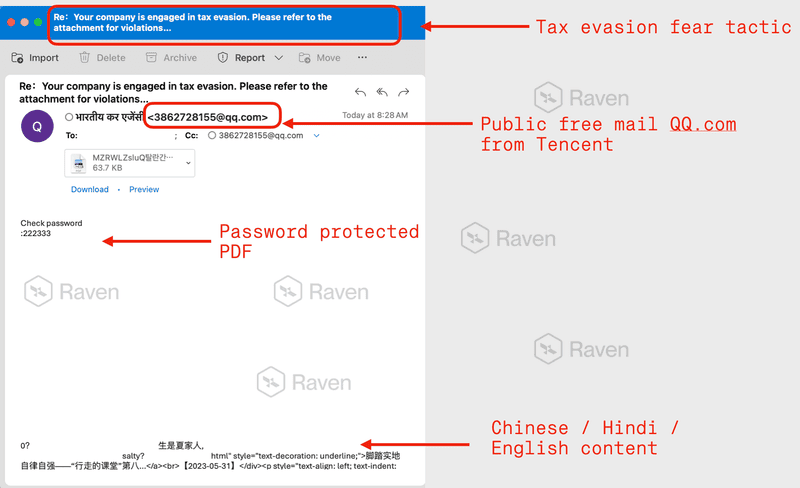
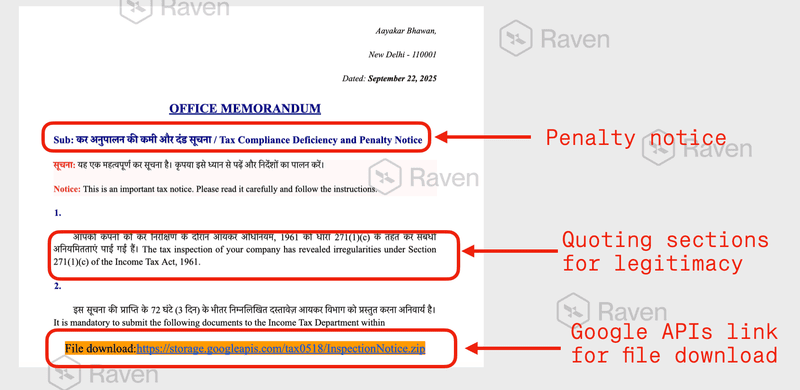
The phishing emails were meticulously crafted to mirror genuine tax compliance notices, featuring bilingual content in Hindi and English, legal references to specific sections of the Income Tax Act of 1961, and urgent 72-hour deadlines that created psychological pressure on recipients.
These messages originated from legitimate QQ.com email accounts that passed SPF, DKIM, and DMARC authentication checks, a critical detail that allowed them to evade sender reputation filtering.
The attackers leveraged multiple delivery mechanisms, including password-protected PDF attachments and Google Docs-hosted documents, making it impossible for traditional antivirus engines to scan the payloads before execution.
Malicious Emails Deliver AsyncRAT
The first phishing variant presented itself as a Tax Compliance Deficiency and Penalty Notice, directing recipients to download a password-protected ZIP file or access a Google Docs link.
Once extracted, the archive revealed a 10.48 MB shellcode loader classified as Trojan.Shellcode and Fragtor.
This multi-stage payload was engineered to execute through regsvr32 proxy loading, a fileless execution technique that avoids static signature detection by leveraging trusted Windows utilities.
Network indicators linked to this stage revealed connections to AsyncRAT and ResolverRAT command-and-control infrastructure, with JA3 SSL fingerprints matching known remote administration tool families.
The second attack variant deployed a 23.34 MB executable named GoToResolveUnattendedUpdater.exe, a rogue Remote Access Backdoor classified as Hacktool.LogMeIn.
This malware masqueraded as a legitimate update for GoToResolve, an authentic remote management platform, and loaded a suspicious DLL called RstrtMgr.dll.
This particular library is notorious for its use by prominent ransomware families including Conti and Cactus to terminate security processes and establish persistence.
The executable exhibited full remote administration capabilities including screen sharing, file transfer, and remote command execution, suggesting that attackers planned interactive lateral movement following the initial compromise.
Flag Rising RAT-Based Threats
Traditional Secure Email Gateways failed to detect this campaign because the authentication infrastructure passed validation while the password-protected attachments prevented content scanning.
The bilingual nature of the notices, combined with legitimate legal references and government-style formatting, created a credibility factor that legacy content filters could not evaluate.
The attackers further evaded detection by incorporating AI-generated Unicode filler text and random spacing patterns consistent with automated phishing kit generation, designed specifically to circumvent Bayesian filtering algorithms.
Indian enterprises faced particular vulnerability to this campaign for several reasons. Tax communication frequently occurs through digital channels, compliance deadlines generate urgency that clouds judgment, and many small and medium-sized enterprises rely solely on basic email filtering.
Additionally, government impersonation carries inherent trust value, particularly among financial services firms, NBFCs, and securities companies that routinely exchange documents with regulators.
Raven AI’s detection success stemmed from a fundamentally different approach than traditional gateways.
Rather than relying on known threat signatures or authentication protocols, the platform analyzed communication intent, behavioral signals, and metadata inconsistencies.
Key detection signals included the identity mismatch of a government tax notice originating from a foreign free mailbox, the behavioral pattern of false urgency combined with document submission demands, and anomalies in how cloud-hosted payloads were being delivered outside normal government workflows.
This campaign underscores a critical evolution in phishing tactics targeting Indian businesses. Attackers are increasingly sophisticated in blending authentic government communication templates with advanced malware chains and misused legitimate remote administration tools.
As authentication mechanisms continue to be exploited by threat actors, organizations must adopt detection strategies that evaluate communication context and behavioral intent rather than relying exclusively on perimeter-based signatures.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
