While preparing for Pwn2Own Ireland 2025, a security researcher revisiting N-day bugs in Synology NAS has demonstrated a powerful new twist on an existing Synology BeeStation (BST150-4T) exploit chain, achieving unauthenticated root Remote Code Execution (RCE) by abusing the system task scheduler instead of more traditional PHP-based payloads.
The work builds on a BeeStation chain originally disclosed by DEVCORE’s Pumpkin and Orange Tsai during Pwn2Own 2024, and later detailed in their research “Writing Sync, Reading Shell.”
The researcher, performing independent N-day analysis after patches were released, realized that although the core bugs were already public, their exploitation path diverged significantly most notably in how SQLite Injection was weaponized.
The chain combines three vulnerabilities tracked as CVE-2024-50629, CVE-2024-50630, and CVE-2024-50631, affecting Synology DSM, BeeStation Manager (BSM), and Synology Drive Server.
Together, they allow an unauthenticated attacker to escalate from pre-auth file read to conditional authentication bypass and finally to post-auth SQL injection that results in root-level code execution.
The first bug, CVE-2024-50629, is a CRLF injection in the SYNO.API.Auth.RedirectURI handler. By injecting carriage return and line feed characters into the redirect_url parameter, an attacker can smuggle arbitrary HTTP headers into the response.
Synology BeeStation Vulnerabilities
Leveraging X-Accel-Redirect within nginx, this can be turned into an internal file-read primitive, exposing sensitive paths such as Synology Drive logs that reveal valid usernames.
Armed with a leaked username, the attacker can move to CVE-2024-50630, an improper authentication flaw in syncd.
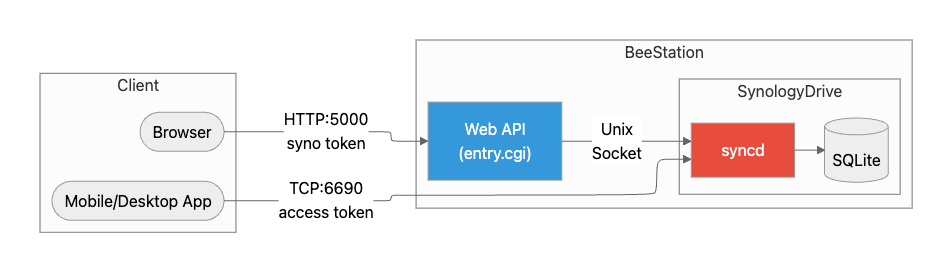
Because AuthenticatorMiddleware::AuthSession prioritizes authentication methods, omitting the password while providing a username in a local (Unix Domain Socket) context causes the flow to fall through to a domain-socket–based trust path.
This yields an access_token based solely on the username, effectively bypassing regular credential checks.
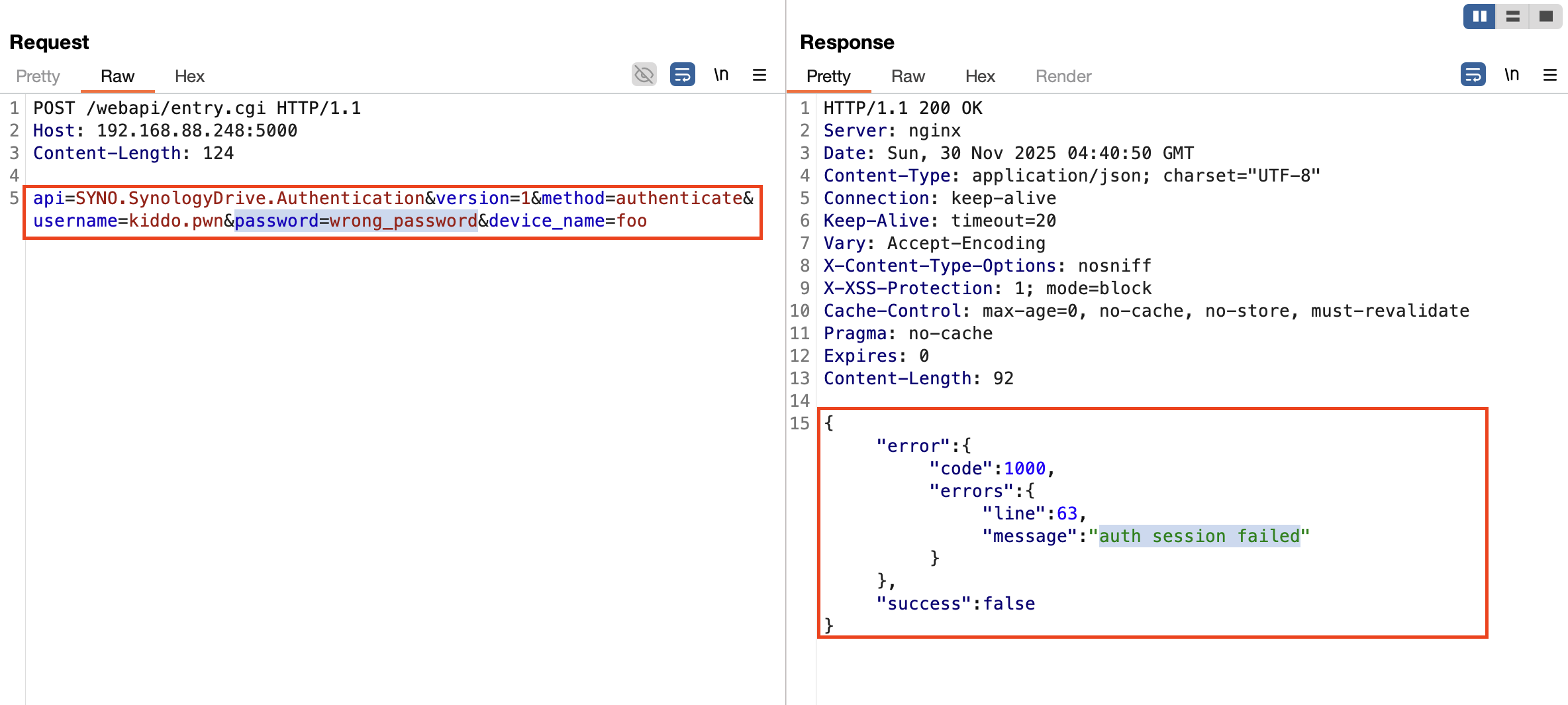
syncd validates authentication.The final stage, CVE-2024-50631, is a SQL injection in the update_settings command of Synology Drive Server.
Attack path leads from user-level to root control
Traditionally, attackers use SQLite injection to perform a “Dirty File Write” and drop a PHP web shell via ATTACH DATABASE. However, BeeStation does not ship with PHP, forcing a different approach.
Here the researcher introduces a novel, universal technique: using SQLite’s file-write primitive to create a malicious cron file under /etc/cron.d/.
Because cron tolerates malformed lines and skips binary garbage, a valid crontab entry surrounded by newlines can coexist with SQLite binary headers. The injected line schedules a reverse shell as root, giving the attacker full system compromise without relying on PHP.
A proof-of-concept exploit chain demonstrating unauthenticated RCE on vulnerable BeeStation devices has been released publicly, and Synology has issued patches in advisories Synology-SA-24:20 and Synology-SA-24:21. Users are strongly urged to update DSM, BeeStation firmware, and Synology Drive Server to the latest versions.
Beyond the immediate impact on Synology users, this research underscores the enduring power of “low-severity” primitives when chained, and showcases cron-based SQLite Dirty File Writes as a broadly applicable RCE technique in PHP-free Linux environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
