The Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA), joined by Canadian cyber authorities, have issued a joint alert warning of a sophisticated new malware campaign dubbed “BRICKSTORM.”
According to the advisory released, state-sponsored hackers from the People’s Republic of China (PRC) are actively using this tool to infiltrate and hide inside critical government and technology networks.
The alert describes BRICKSTORM as a dangerous “backdoor,” a type of malicious software that functions like a secret unlocking mechanism, allowing attackers to return to a victim’s system whenever they please.
The malware is specifically designed to target VMware vSphere, a widely used software for running virtual servers, as well as standard Windows environments.
Officials stated that the primary goal of the campaign is espionage. By targeting the underlying software that manages corporate servers (specifically VMware vCenter and ESXi), the attackers can effectively become “ghosts” in the machine.
They can monitor activity, steal sensitive data, and even copy entire “snapshots” of servers to extract passwords and cryptographic keys without triggering standard security alarms.
How the Attack Works
The report reveals that these attacks are highly calculated. In one confirmed case, hackers gained entry to a victim’s network as early as April 2024 and remained undetected until September 2025.
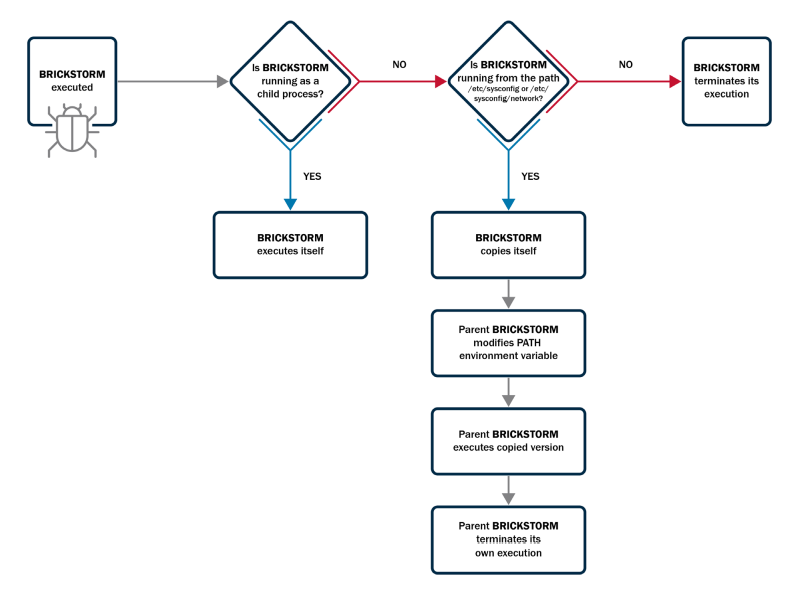
They initially broke in through a vulnerable web server, then moved sideways through the network using stolen passwords. Once deep inside, they planted the BRICKSTORM malware.
What makes BRICKSTORM particularly difficult to detect is its ability to blend in. The malware uses complex encryption techniques to hide its communications.
It disguises its commands as regular web traffic or secure internet connections, making it look like regular business activity to network defenders.
It also has a “self-watching” feature. If a security program tries to stop or delete it, BRICKSTORM can automatically reinstall itself and reboot, ensuring the attackers never lose their foothold.
The agencies warned that this campaign is targeting “Government Services and Facilities” and the “Information Technology” sectors.
The impact of a successful infection can be severe. In the analyzed attacks, hackers stole critical digital keys, enabling them to impersonate legitimate users and access highly restricted areas of the network.
CISA and the NSA are urging all organizations, especially those in critical infrastructure, to search their networks for signs of this specific threat immediately.
The agencies have released technical “signatures”, digital fingerprints that security teams can use to identify the malware.
Administrators are advised to update their VMware products immediately, strictly limit access to management systems, and monitor for any unusual account activity. “
This is a long-term persistence tool,” the alert concludes, warning that simply removing the initial infection may not be enough if the attackers have already burrowed deep into the virtualization infrastructure.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
