A security researcher has unveiled a novel web exploitation technique dubbed “SVG clickjacking,” which significantly elevates the sophistication of traditional user-interface redress attacks.
Unlike standard clickjacking, which typically involves tricking users into clicking a hidden button on a static overlay, this new method allows attackers to create complex, responsive, and highly interactive fake interfaces that sit on top of legitimate websites.
The core of this technique lies in the creative misuse of Scalable Vector Graphics (SVG) filters.
These filters, commonly used for visual effects like blurring or color shifting, act as a functional logic engine in this context.
Researcher Lyra Horse discovered that standard SVG elements such as feColorMatrix, feDisplacementMap, and feComposite can be combined to create logic gates (like AND, OR, and XOR).
This allows an attacker to build a functional “program” directly within the browser’s rendering engine.
Crucially, these filters can analyze pixels from a cross-origin iframe (a website embedded inside another) and react to what is happening on the screen in real time.
For example, the attack script can detect whether a specific dialog box has opened, whether a checkbox is selected, or whether error text has appeared on the target site.
Based on this visual data, the SVG filters can dynamically update the fake overlay the user sees.
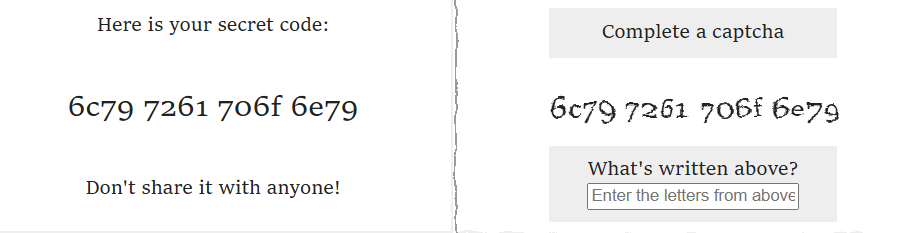
This creates a seamless illusion where the user believes they are interacting with a harmless game or a “prove you are human” captcha, while they are actually clicking buttons, typing text, or toggling settings on a sensitive application like Google Docs or an email service.
In a proof-of-concept exploit targeting Google Docs, the researcher demonstrated how this technique could trick a user into generating a document and typing data into it, all while thinking they were solving a puzzle.
The attack successfully hid the real Google Docs interface behind a convincing fake UI that reacted to the user’s input in real time.
Google awarded a $3,133.70 bug bounty for this discovery, acknowledging the severity of this interactive redress method.
The technique also introduces new avenues for data exfiltration. The researcher showed that it is possible to read sensitive pixel data from a target site and encode it into a QR code generated entirely by SVG filters.

An attacker could then prompt the user to scan this code, effectively stealing information from the protected website without ever directly accessing the target page’s code.
This research marks a significant shift in the landscape of browser-based threats. By turning the browser’s own graphical rendering tools into a logic engine, SVG clickjacking bypasses many traditional assumptions about static web attacks, proving that even purely visual elements can be weaponized to facilitate complex unauthorized actions.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
