Russian state-linked hackers are impersonating high-profile European security conferences to compromise cloud email and collaboration accounts at governments, think tanks, and policy organizations, according to new research from cybersecurity firm Volexity.
The campaigns, active through late 2025, abuse legitimate Microsoft and Google authentication workflows and rely on painstaking social engineering to trick victims into effectively handing over access to their accounts.
Volexity attributes the activity to the Russian threat actor UTA0355, previously linked to attacks that abuse Microsoft 365 OAuth and Device Code authentication flows.
The latest operations show that, despite public exposure of these methods earlier in 2025, the group continues to refine its lures and delivery tactics rather than its core technical approach.
In two major campaigns, UTA0355 created convincing phishing infrastructure around real international security events in Europe.
One operation spoofed the Belgrade Security Conference, scheduled for November 17–19, 2025, while another impersonated the Brussels Indo-Pacific Dialogue (BIPD), an Indo-Pacific policy forum hosted in Brussels in early December 2025.
Spoofing European Events to Deceive Victims
In both cases, the attackers built professional-looking websites and registration flows designed to mimic authentic event processes, then used those sites as launchpads into Microsoft 365 phishing workflows.
For the Belgrade Security Conference, Volexity investigated an October 2025 incident in which a user’s Microsoft 365 account was compromised after an anomalous login was detected.
The victim had been engaged via a rapport-building phishing campaign in an existing email thread about the conference.
Once the victim authenticated, the attacker instructed them over WhatsApp to send back the full browser URL under the pretext of “finalizing” their registration. That URL contained the OAuth authorization code needed to complete the attack.
After obtaining access, the intruder registered a new device in Microsoft Entra ID using the same name as one of the victim’s legitimate devices and accessed files from what appeared to be an Android device masquerading as an iPhone.
Volexity later observed the same actor broadening its targeting through emails sent from an attacker-controlled Gmail account, directing recipients to a fake conference site at bsc2025[.]org.
Recommendations
Depending on the target’s email domain, visitors were either shown a generic registration confirmation or silently funneled into a Microsoft 365 login sequence designed to harvest credentials.
The attacker first maintained benign correspondence, then sent an invitation to register for conference resources via a Microsoft OAuth URL.
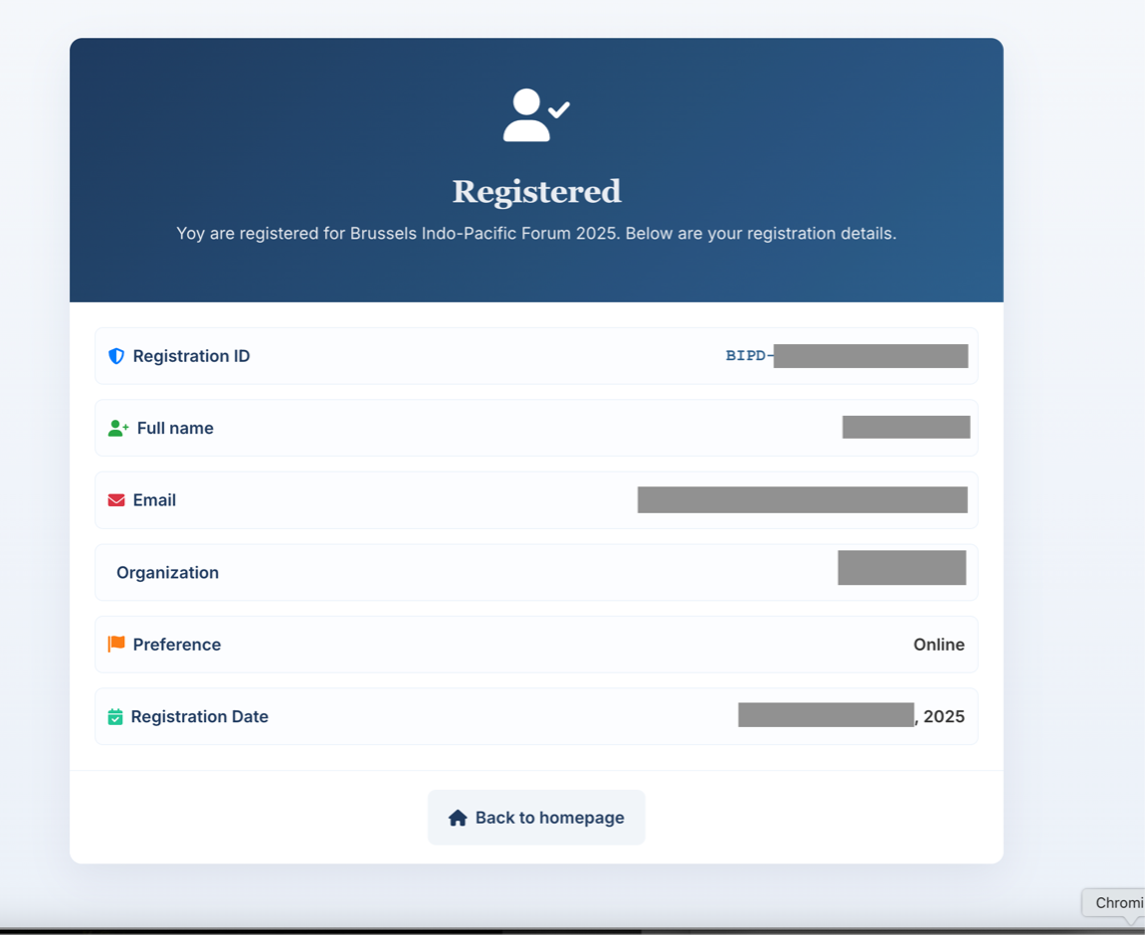
A parallel campaign spoofed the Brussels Indo-Pacific Dialogue. Emails, purportedly from staff at the Centre for Security, Diplomacy, and Strategy at Vrije Universiteit Brussel, targeted individuals working on foreign policy, European affairs, or formerly in senior U.S. government roles.
After several emails to build trust, the attacker sent a unique URL and instructed victims to send back the exact URL if they encountered errors another OAuth code phishing pattern.
The infrastructure included repurposed domains such as ustrs[.]com and a dedicated lookalike site, brussels-indo-pacific-forum[.]org, which ultimately drove targets into a Microsoft 365 Device Code phishing workflow disguised as a conference registration system.
Volexity’s analysis suggests UTA0355 is also experimenting with infrastructure for other significant events.
Volexity concludes that UTA0355’s sustained investment in realistic event-themed lures, multi-channel communication via email and messaging apps, and abuse of trusted cloud authentication flows underscores both the actor’s resources and the continued effectiveness of these techniques against high-value targets.
WHOIS records tied to bsc2025[.]org led investigators to additional domains spoofing the World Nuclear Exhibition in Paris, scheduled for November 4–6, 2025, including world-nuclear-exhibition-paris[.]com and wne-2025[.]com.
While their operational use has not been confirmed, researchers assess that they were likely prepared for related or earlier campaigns.
Across these operations, UTA0355 systematically expands its target pool by asking non-attending invitees to share contact details of colleagues who might be interested, effectively crowdsourcing a curated victim list.
Access to compromised accounts is then routed through proxy networks, further obscuring attribution and location.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
