Security researchers have uncovered critical infrastructure details for the notorious LockBit 5.0 ransomware operation, including the IP address 205.185.116.233 and the domain karma0.xyz, which hosts the group’s latest leak site.
The discovery represents a significant operational security failure for the cybercriminal organization.
Cybersecurity researcher Rakesh Krishnan first publicized the findings on December 5, 2025, identifying the server hosted under AS53667 (PONYNET, operated by FranTech Solutions), a network frequently exploited for illicit activities.
The server displays a DDoS protection page branded with “LOCKBITS.5.0,” confirming its direct role in the ransomware group’s operations.
WHOIS records indicate karma0.xyz was registered on April 12, 2025, with an expiration date in April 2026.
The domain utilizes Cloudflare nameservers and Namecheap privacy protection, listing Reykjavik, Iceland, as the contact location.
The domain status shows client transfer prohibited, suggesting attempts to maintain control amid increased scrutiny.
Critical Vulnerabilities Exposed
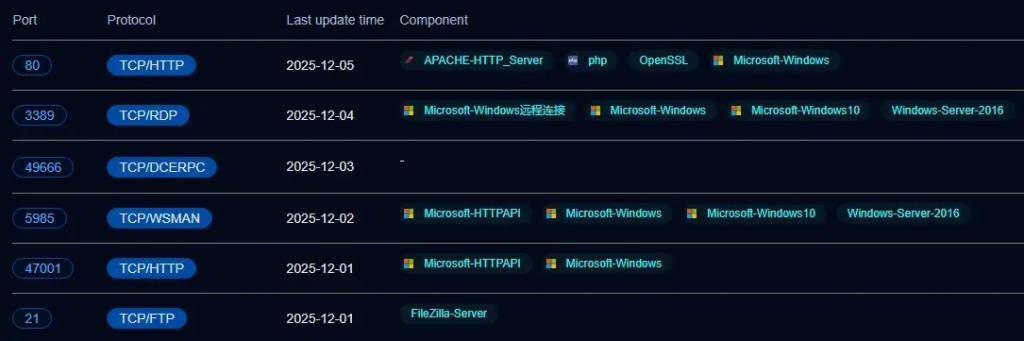
Security scans revealed multiple open ports on the exposed server, creating significant security risks.
Port 21 runs an FTP server, while port 80 operates Apache/2.4.58 (Win64) with OpenSSL/3.1.3 and PHP/8.0.30.
Port 3389 exposes Remote Desktop Protocol (RDP) on a Windows host named WINDOWS-401V6QI, presenting a high-risk vector for unauthorized access.
Additional open ports include 5000 and 5985 for HTTP and WinRM, respectively; port 47001 for HTTP; and port 49666 for a file server.
LockBit 5.0 emerged around September 2025, with enhanced malware capabilities that support Windows, Linux, and ESXi systems.
The ransomware features randomized file extensions, geolocation-based evasion that skips Russian systems, and accelerated encryption using XChaCha20 algorithms.
According to CyberSecurityNews, researchers noted that the group incorporates Smokeloader into its attack campaigns.
Security defenders should immediately block the exposed IP address and domain. Organizations can monitor these indicators for potential compromise attempts.
This exposure highlights persistent operational security failures for LockBit, despite multiple law enforcement disruptions.
The group continues demonstrating resilience while maintaining active ransomware operations targeting organizations worldwide.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
