By Sila Özeren Hacioglu, Security Research Engineer at Picus Security.
For security leaders, the most dreaded notification isn’t always an alert from their SOC; it’s a link to a news article sent by a board member. The headline usually details a new campaign by a threat group like FIN8 or a recently exposed massive supply chain vulnerability. The accompanying question is brief but paralyzing by implication: “Are we exposed to this right now?“.
In the pre-LLM world, answering that question set off a mad race against an unforgiving clock. Security teams had to wait for vendor SLAs, often eight hours or more for emerging threats, or manually reverse-engineer the attack themselves to build a simulation. Though this approach delivered an accurate response, the time it took to do so created a dangerous window of uncertainty.
AI-driven threat emulation has eliminated much of the investigative delay by accelerating analysis and expanding threat knowledge. However, AI emulation still carries risks due to limited transparency, susceptibility to manipulation, and hallucinations.
At the recent BAS Summit, Picus CTO and Co-founder Volkan Ertürk cautioned that “raw generative AI can create exploit risks nearly as serious as the threats themselves.” Picus addresses this by using an agentic, post-LLM approach that delivers AI-level speed without introducing new attack surfaces.
This blog breaks down what that approach looks like, and why it fundamentally improves the speed and safety of threat validation.
The “Prompt-and-Pray” Trap
The immediate reaction to the Generative AI boom was an attempt to automate red teaming by simply asking Large Language Models (LLMs) to generate attack scripts. Theoretically, an engineer could feed a threat intelligence report into a model and ask it to “draft an emulation campaign”.
While this approach is undeniably fast, it fails in reliability and safety. As Picus’s Ertürk notes, there’s some danger in taking this approach:
“ … Can you trust a payload that is built by an AI engine? I don’t think so. Right? Maybe it just came up with the real sample that an APT group has been using or a ransomware group has been using. … then you click that binary, and boom, you may have big problems.”
The problem is not only risky binaries. As mentioned above, LLMs are still prone to hallucination. Without strict guardrails, a model might invent TTPs (Tactics, Techniques, and Procedures) that the threat group doesn’t actually use, or suggest exploits for vulnerabilities that don’t exist. This leaves security teams struggling to validate their defenses against theoretical threats while not taking the time to address actual ones.
To address these issues, the Picus platform adopts a fundamentally different model: the agentic approach.
Stop relying on risky, hallucination-prone LLMs. Picus uses a multi-agent framework to map threat intelligence directly to safe, validated simulations.
Close the gap between a news alert and your defense readiness with the world’s first Agentic BAS platform.
Get Your Demo
The Agentic Shift: Orchestration Over Generation
The Picus approach, embodied in Smart Threat, moves away from using AI as a code generator and instead uses it as an orchestrator of known, safe components.
Rather than asking AI to create payloads, the system instructs it to map threats to the trusted Picus Threat Library.
“So our approach is … we need to leverage AI, but we need to use it in a smart way… We need to say that, hey, I have a threat library. Map the campaign you built to my TTPs that I know are high quality, low explosive, and just give me an emulation plan based on what I have and on my TTPs.” – Volkan Ertürk, CTO & co-founder of Picus Security.
At the core of this model is a threat library built and refined over 12 years of real-world threat Picus Labs threat research. Instead of generating malware from scratch, AI analyzes external intelligence and aligns it to a pre-validated knowledge graph of safe atomic actions. This ensures accuracy, consistency, and safety.
To execute this reliably, Picus uses a multi-agent framework rather than a single monolithic chatbot. Each agent has a dedicated function, preventing errors and avoiding scaling issues:
-
Planner Agent: Orchestrates the overall workflow
-
Researcher Agent: Scours the web for intelligence
-
Threat Builder Agent: Assembles the attack chain
-
Validation Agent: Checks the work of the other agents to prevent hallucinations
Real-Life Case Study: Mapping the FIN8 Attack Campaign
To show how the system works in practice, here is the workflow the Picus platform follows when processing a request related to the “FIN8” threat group. This example illustrates how a single news link can be converted into a safe, accurate emulation profile within hours.
A walkthrough of the same process was demonstrated by Picus CTO Volkan Ertürk during the BAS Summit.
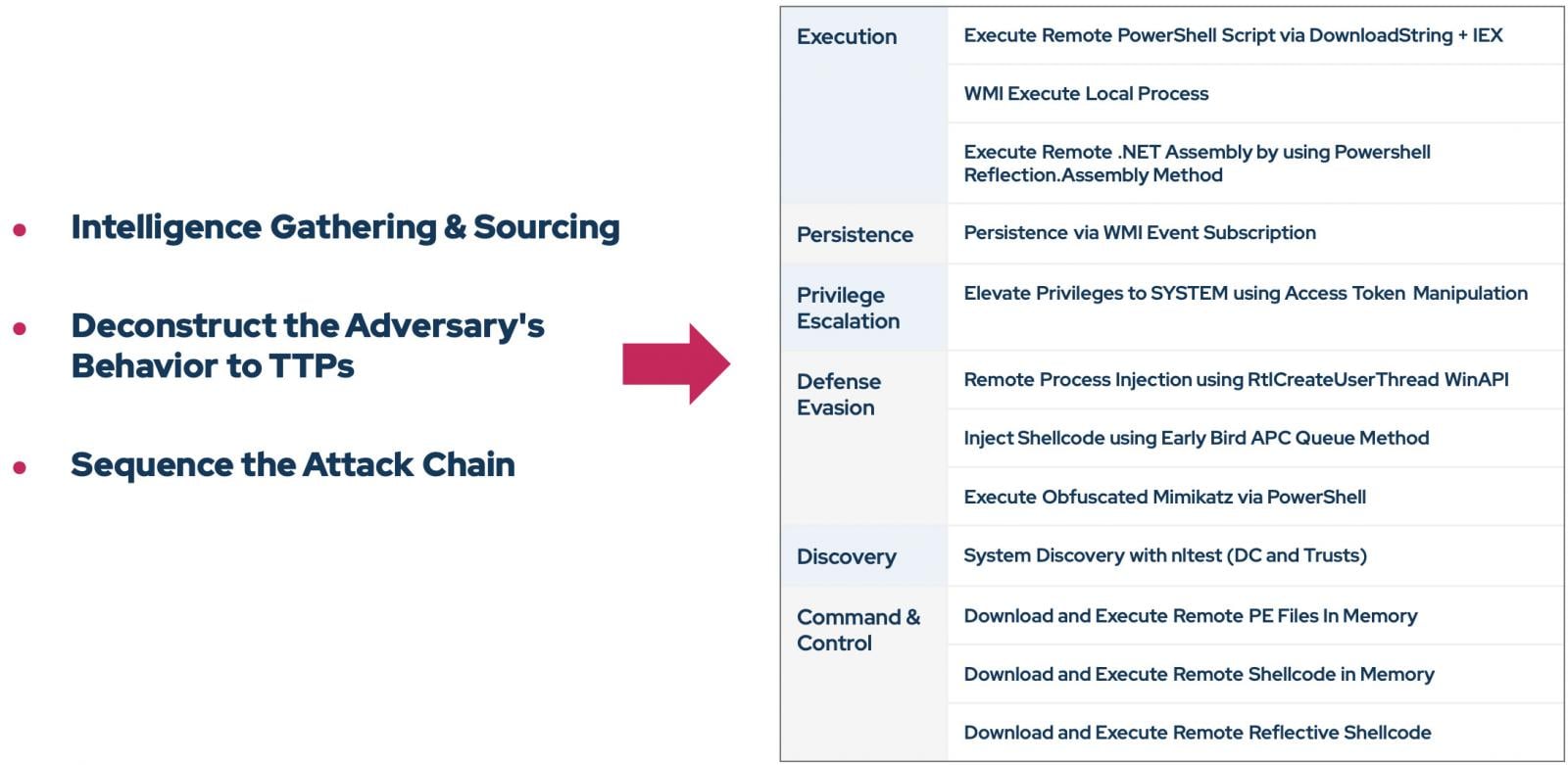
Step 1: Intelligence Gathering and Sourcing
The process begins with a user inputting a single URL, perhaps a fresh report on a FIN8 campaign.
The Researcher Agent doesn’t stop at that single source. It crawls for connected links, validates the trustworthiness of those sources, and aggregates the data to build a comprehensive “finished intel report.”
Step 2: Deconstruction and Behavior Analysis
Once the intelligence is gathered, the system performs behavioral analysis. It deconstructs the campaign narrative into technical components, identifying the specific TTPs used by the adversary.
The goal here is to understand the flow of the entire attack, not just its static indicators.
Step 3: Safe Mapping via Knowledge Graph
This is the critical “safety valve.”
The Threat Builder Agent takes the identified TTPs and queries the Picus MCP (Model Context Protocol) server. Because the threat library sits on a knowledge graph, the AI can map the adversary’s malicious behavior to a corresponding safe simulation action from the Picus library.
For example, if FIN8 uses a specific method for credential dumping, the AI selects the benign Picus module that tests for that specific weakness without actually dumping any real credentials.
Step 4: Sequencing and Validation
Finally, the agents sequence these actions into an attack chain that mirrors the adversary’s playbook. A Validation Agent reviews the mapping to ensure no steps were hallucinated or potential errors were introduced.
The output is a ready-to-run simulation profile containing the exact MITRE tactics and Picus actions needed to test organizational readiness.
The Future: Conversational Exposure Management
Beyond just building threats, this agentic approach is changing the interface of security validation. Picus is integrating these capabilities into a conversational interface called “Numi AI.”
This moves the user experience from navigating complex dashboards to simpler, clearer, intent-based interactions.
As an example, a security engineer can express high-level intent, “I don’t want any configuration threats“, and the AI monitors the environment, alerting the user only when relevant policy changes or emerging threats violate that specific intent.
This shift toward “context-driven security validation” allows organizations to prioritize patching based on what is truly exploitable.
By combining AI-driven threat intelligence with supervised machine learning that predicts control effectiveness on non-agent devices, teams can distinguish between theoretical vulnerabilities and true risks to their specific organization and environments.
In a landscape where threat actors move fast, the ability to turn a headline into a validated defense strategy within hours is no longer a luxury; it’s a necessity.
The Picus approach suggests that the best way to use AI isn’t to let it write malware, but to let it organize the defense.
Close the gap between your threat discovery and defense validation efforts.
Request a demo to see Picus’ agentic AI in action, and learn how to operationalize breaking threat intelligence before it’s too late.
Note: This article was expertly written and contributed by Sila Ozeren Hacioglu, Security Research Engineer at Picus Security.
Sponsored and written by Picus Security.
