A sophisticated Android malware campaign dubbed NexusRoute is actively targeting Indian users by impersonating the Indian Government Ministry, mParivahan, and e-Challan services to steal credentials and carry out large-scale financial fraud.
The operation combines phishing, malware, and surveillance capabilities. It is being distributed via malicious APKs hosted on GitHub and clusters of phishing domains that run fake challan and ₹1 verification workflows.
The campaign is financially motivated and professionally engineered, using a multi-stage, native-backed Android Remote Access Trojan (RAT) that abuses advanced obfuscation, dynamic code loading, and persistent background execution to evade detection and maintain long-term control over infected devices.
Stolen data includes UPI PINs, OTPs, card information, banking credentials, call logs, SMS, contacts, device details, and GPS location, which are funneled to a centralized command-and-control (C2) infrastructure for real-time fraud and surveillance.
NexusRoute starts with phishing pages hosted on GitHub Pages and lookalike domains such as rtochallan[digits].store, .shop, and .online, all branded as “NexGen mParivahan.”
These pages prompt users to enter mobile and vehicle numbers, then push a bogus ₹1 “ownership verification” payment.
Victims are then redirected to fake UPI, card, and net-banking interfaces crafted to harvest sensitive financial data, including UPI PINs, which enable direct unauthorized debits without further user interaction.
A central lure is a fake Parivahan APK downloaded from GitHub. The app instructs victims to enable installation from unknown sources, then deploys a multi-stage loader that decrypts and loads hidden DEX payloads and hands execution off to native .so libraries via JNI.
Malware Targets Android Users
The malware declares and requests a wide range of high-risk permissions, such as REQUEST_INSTALL_PACKAGES, SYSTEM_ALERT_WINDOW, READ_SMS, SEND_SMS, READ_CONTACTS, full file access, and accessibility services. It also checks for emulators and rooted environments to evade analysis.
The code tries to start a service and then redirects the user to the MANAGE_APP_ALL_FILES_ACCESS_PERMISSION settings page.
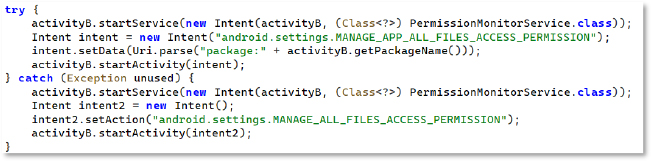
Once installed, NexusRoute abuses BroadcastReceivers, foreground services, scheduled jobs, OEM-specific auto-start settings, wake-locks, and battery optimization exemptions to ensure continuous execution.
On some devices, it manipulates default home app settings to trap users in system screens until its hidden payload is installed.
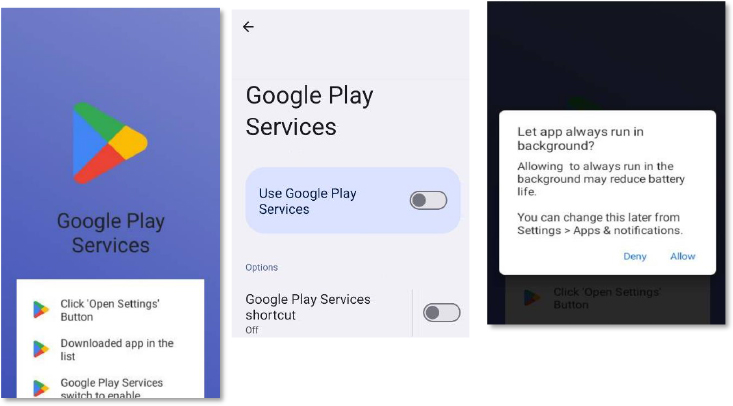
It then displays fake Google Play style update prompts and security alerts to trick users into granting Accessibility and other sensitive permissions, silently auto-approving future prompts in the background.
The malware’s capabilities include SMS interception and exfiltration, dual-SIM profiling and targeted SMS sending, keylogging, screen capture via MediaProjection, remote camera and microphone control, file access and deletion, and continuous GPS tracking.
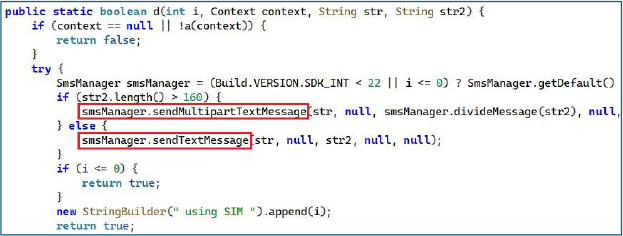
A Socket.IO-based C2 channel with automatic reconnection maintains persistent operator control, appending detailed device metadata to fingerprint each victim uniquely.
Impact on Victims
Coordinated action by CERTs, law enforcement, telecom operators, banks, and platform providers is urgently needed to dismantle hosting infrastructure, disrupt C2 servers, issue public advisories, and clamp down on related fraud.
OSINT links the malware’s crash-reporting and data exfiltration routines to the email address [email protected], which is associated with a broader ecosystem of Android obfuscation, protection, and spyware tooling under the “Gymkhana Studio” branding.
Public blogs, developer profiles, and an archived surveillance control panel interface suggest this is part of a semi-commercial Android spyware and fraud platform, not a low-skill scam kit.
The scale of GitHub repository abuse, automated phishing domain generation, and centralized RAT dashboards indicates a mature, industrialized operation.
Given its direct impact on UPI and card-based payments, its mistreatment of critical Indian government digital brands, and its surveillance capabilities, NexusRoute constitutes a national-scale financial and cyber-surveillance threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
