Security researchers have unveiled a dangerous new technique that allows malware to completely hide its tracks by faking Windows call stacks a method designed to bypass modern endpoint detection systems.
The technique, called Moonwalk++, extends previous research on Stack Moonwalking and demonstrates a critical vulnerability in how security tools validate whether malware is calling sensitive Windows functions.
By forging the chain of function calls that appear in system memory, attackers can make malicious code look like it’s coming from legitimate software.
“Call stacks have become a critical detection surface for modern EDR tools,” explains the research. Security products like Elastic Security have invested heavily in analyzing call stacks to catch suspicious API calls.
However, Moonwalk++ shows these defenses have significant blind spots.
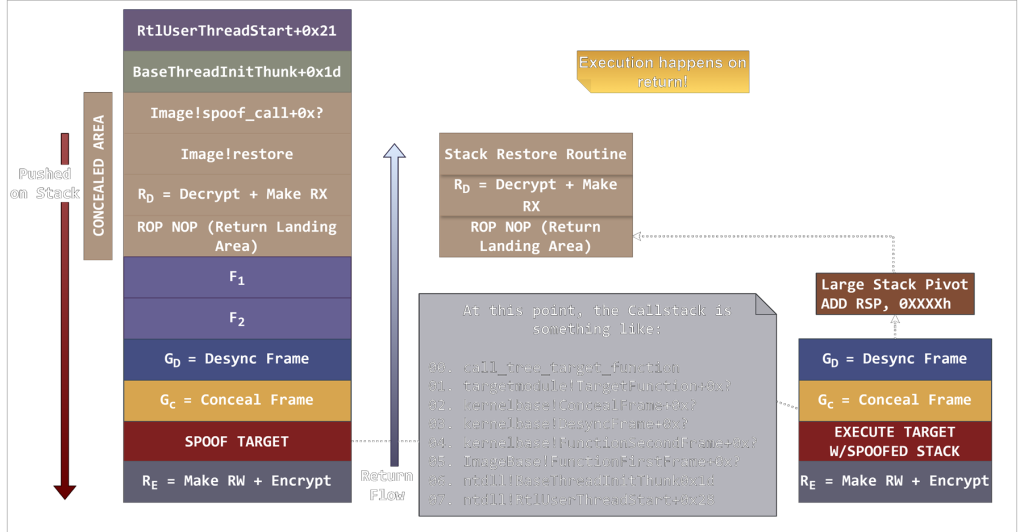
The attack exploits how Windows stores information about which functions call other functions.
Normally, when malware calls a sensitive Windows API like creating a new process or allocating memory security tools examine this call chain to trace the malware’s origin.
Moonwalk++ manipulates this chain to hide the real attacker and point to legitimate Windows system functions instead.
What makes Moonwalk++ particularly dangerous is its ability to encrypt the malicious code while it’s running.
Previous versions of Stack Moonwalking couldn’t do this because the technique relied on specific execution patterns that would break if the code was encrypted.
The new version solves this problem through a clever stack manipulation trick, allowing malware to remain hidden even while executing.
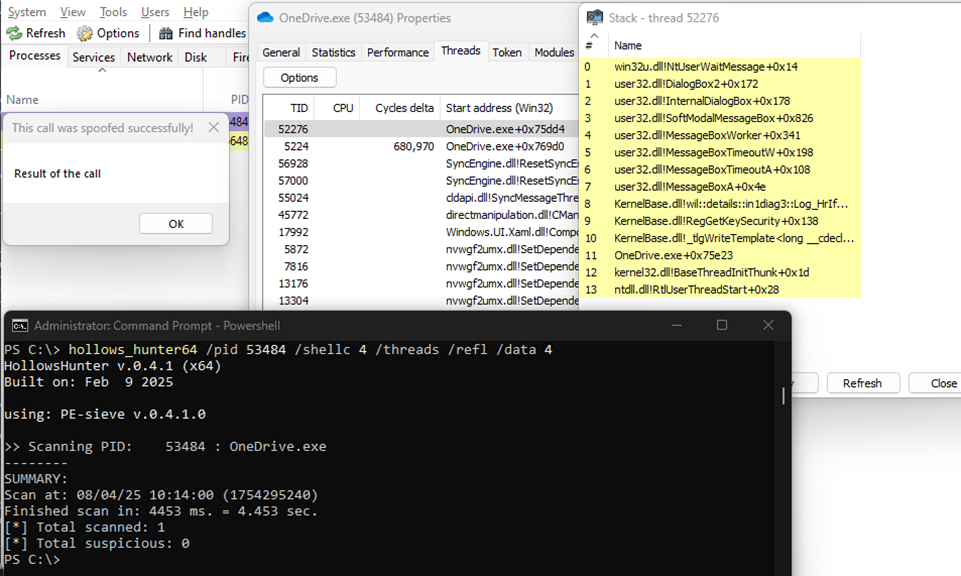
The researchers tested their proof-of-concept against popular detection tools, including Hunt-Sleeping-Beacons, Get-InjectedThreadEx, and Hollow’s Hunter.
All of them failed to detect the Moonwalk++ technique when it was injected into legitimate Windows processes like OneDrive.exe.
The technique defeats current detection methods by meeting several key conditions. First, it removes any direct references to the actual malicious code from the call stack.
Second, it makes the thread appear to start from legitimate Windows functions. Third, it conceals any suspicious memory regions that malware typically leaves behind.
This research represents a significant escalation in the ongoing cat-and-mouse game between attackers and defenders.
As detection strategies become more sophisticated, adversaries are developing equally advanced evasion techniques.
The authors built on research originally presented at DEFCON 31 and have released their proof-of-concept code publicly on GitHub.
For security teams, this research highlights the limitations of relying solely on call stack analysis for detection.
Defense strategies must incorporate additional telemetry beyond stack inspection, including behavioral analysis, memory patterns, and API usage frequency monitoring.
The full technical details and proof-of-concept code are available to security researchers and defenders studying advanced evasion techniques.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
