Cybersecurity researchers at GreyNoise have identified a large-scale, coordinated campaign targeting enterprise VPN authentication systems.
The attackers are systematically attempting to breach Cisco SSL VPN and Palo Alto Networks GlobalProtect services through credential-based attacks rather than exploiting specific vulnerabilities.
The campaign activity was observed during mid-December across a concentrated two-day period, revealing a sophisticated approach to compromising enterprise access points.
Attack Details
The campaign began on December 11 when GreyNoise detected a massive spike in automated login attempts targeting Palo Alto Networks GlobalProtect portals.
The attackers generated approximately 1.7 million login sessions within just 16 hours, originating from more than 10,000 unique IP addresses.
The attack traffic targeted GlobalProtect portals primarily located in the United States, Pakistan, and Mexico, with all requests originating from infrastructure managed by 3xK GmbH, a German hosting provider.
The attackers employed a uniform attack pattern, reusing common username and password combinations with a Firefox user agent an unusual choice for automated attacks.
This consistency suggests the campaign was designed to identify weakly protected or exposed GlobalProtect portals and inventory them at scale.
One day later, on December 12, the same threat actors shifted focus to Cisco SSL VPN endpoints.
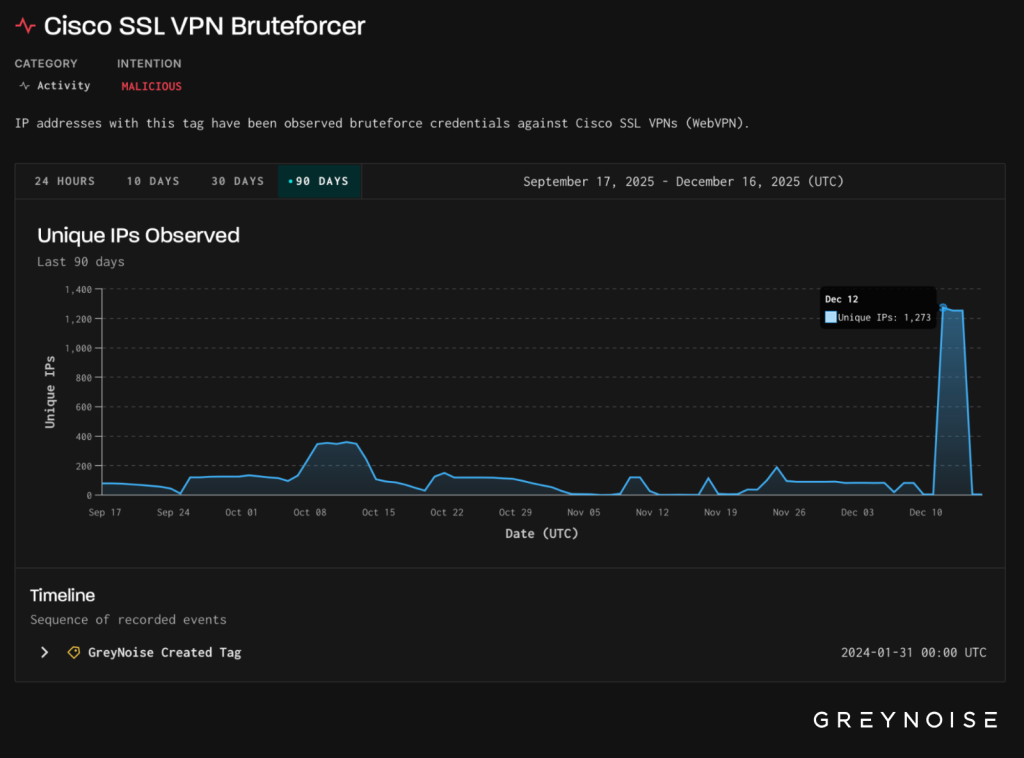
The number of unique attacking IP addresses jumped dramatically from a typical baseline of fewer than 200 to 1,273 IPs, representing a significant deviation from normal activity patterns.
Analysis confirmed this activity shared the same infrastructure, TCP fingerprint, and originating hosting provider as the Palo Alto attack wave.
Login attempts followed standard SSL VPN authentication workflows, including CSRF token handling and parameterized username and password fields.
The requests were consistent with credential stuffing and password spraying techniques attacks designed to test stolen or common credential pairs against enterprise systems.
Notably, GreyNoise found no evidence linking this campaign to a separate Cisco Talos operation targeting Cisco Secure Email Gateway services.
GreyNoise has published blocklists for both the Palo Alto Networks Login Scanner and Cisco SSL VPN Bruteforcer, allowing customers to quickly block malicious IP addresses.
The company is continuing to monitor the campaign and will provide updates as new information emerges.
This attack underscores the persistent pressure targeting enterprise VPN infrastructure and highlights the importance of strong access controls and continuous monitoring at network perimeters.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
