Tax-themed phishing campaigns have intensified in recent months, capitalizing on the heightened awareness surrounding India’s Income Tax Return (ITR) filing season.
Public discussions about refund timelines and compliance deadlines create an ideal backdrop for attackers to craft credible lures.
Recent analysis of emails impersonating the Indian Income Tax Department reveals a sophisticated operation far more dangerous than typical credential-harvesting schemes a coordinated multi-stage infection chain designed to establish persistent remote access to victim systems.
The attack begins with a carefully crafted spear-phishing email spoofed from an Outlook.com domain, an immediate red flag since legitimate government agencies avoid public webmail services.
The subject line, “Tax Compliance Review Notice,” exploits recipient concerns about missed deadlines.
Rather than using text-based content that automated filters might detect, attackers embedded an image replicating an authentic ITD notice, complete with the Government of India emblem, fabricated office references, fake DIN numbers, and artificial urgency markers.
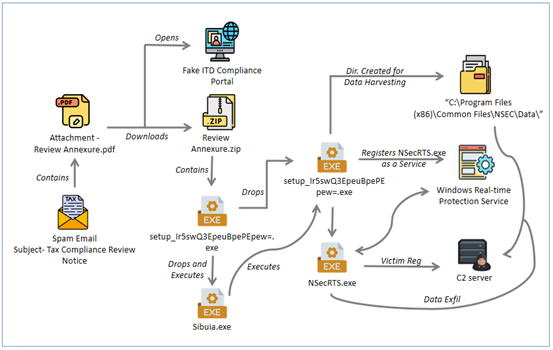
The attached “Review Annexure.pdf” escalates the social engineering pressure by claiming prior non-compliance and directing users to a fraudulent “Compliance Portal” via an embedded URL.
This narrative progression notification of alleged violation followed by a corrective action link represents textbook psychological manipulation designed to bypass critical thinking in time-pressured recipients.
The Infection Cascade
Notably, the portal displays an explicitly suspicious message: “To avoid false positives from security software, please disable your antivirus program in advance before using the client.”
No legitimate government service would request this a transparent signal of malicious intent that attempts to lower victim defenses through a false “compatibility” explanation.
The extracted executable, a 150MB NSIS installer digitally signed by a Chinese entity (Hengshui Shenwei Technology Co., Ltd.), operates as a silent loader.
It unpacks multiple components into temporary directories, executes supporting binaries without user interaction, and then self-destructs to minimize forensic evidence.
This handoff mechanism introduces a second-stage installer an additional 147MB NSIS package with a different digital signature (Shandong Anzai Information Technology CO., Ltd.); this effectively creates a two-layer deployment architecture that complicates attribution and detection.
The second stage installs a Chinese-language application package that extracts kernel drivers, remote desktop components, system utilities, and monitoring tools into “C:Program FilesCommon FilesNSEC” with hidden attributes.
The installer then achieves persistence by registering NSecRTS.exe as a Windows Service masquerading as “Windows Real-time Protection Service,” ensuring automatic execution at system startup.
The NSecRTS.exe service establishes encrypted command-and-control (C2) connections to multiple IP addresses (154[.]91[.]84[.]3, 45[.]113[.]192[.]102, and 103[.]235[.]46[.]102) across non-standard ports, enabling remote task execution and additional payload deployment.
Threat Implications
This campaign exemplifies a fundamental shift in tax-themed phishing: beyond credential theft, it delivers full-featured Remote Access Trojan capabilities with persistent access, extensive surveillance, and command-and-control infrastructure.
Sibuia.exe spawns another “setup_Ir5swQ3EpeuBpePEpew=.exe” as a child process from the temporary � directory, effectively handing off execution to the another signed installer payload.

Once persistence is established, the malware begins harvesting extensive system information OS version, installed applications, running services, and hardware configuration storing this data in a structured directory format.
Multiple technical indicators Simplified Chinese language usage, installer ecosystem architecture, and code-signing entities suggest China-linked development or packaging.
For defenders, the lesson is clear: finance-themed phishing emails remain effective social engineering vectors precisely because they exploit legitimate seasonal concerns.
Organizations must implement email filtering beyond text analysis, scrutinize suspicious requests to turn off security controls, and monitor for unauthorized service registrations and non-standard C2 communications.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
