Socket’s Threat Research Team has exposed a sophisticated credential-harvesting campaign that has operated through malicious Chrome extensions since 2017.
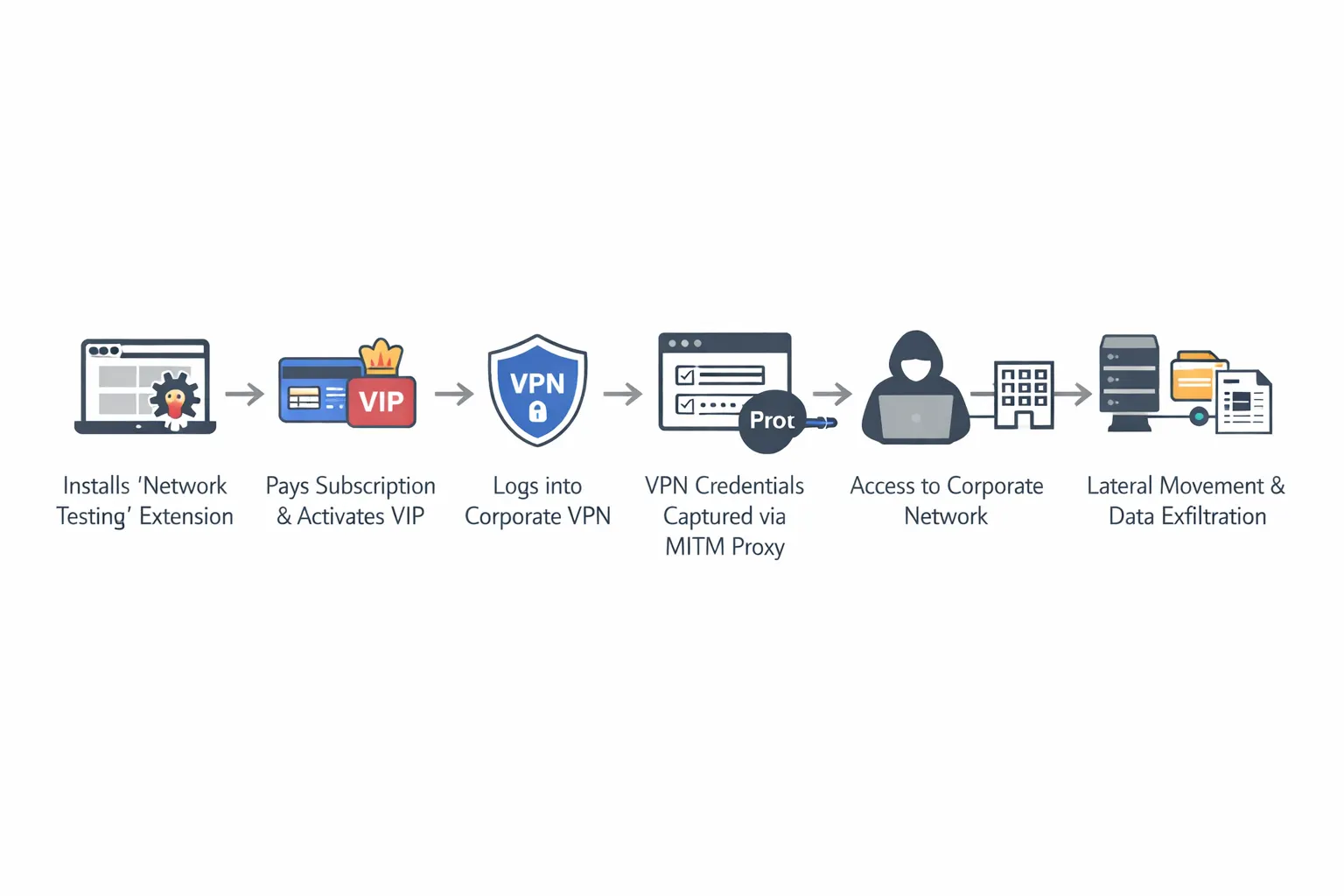
Two variants of an extension named Phantom Shuttle (幻影穿梭), published under the threat actor email [email protected], have compromised over 2,180 users by masquerading as legitimate network testing tools while executing complete traffic interception and credential theft.
The extensions market themselves as “multi-location network speed testing plugins” specifically targeting Chinese-speaking developers and foreign trade personnel.
Users pay monthly subscriptions ranging from ¥9.9 to ¥95.9 CNY ($1.40–$13.50 USD), believing they’re purchasing a functional VPN service.
Behind this commercial facade, both variants execute identical malicious operations: automatic credential injection into HTTP authentication requests, man-in-the-middle proxy positioning, and continuous exfiltration of user data to threat actor–controlled infrastructure.
The malware operates through two malicious JavaScript libraries bundled within the extension.
Using custom character-index encoding obfuscation, the code prepends malicious instructions to the legitimate jQuery v1.12.2 library code.
The malware automatically injects hardcoded proxy credentials (topfany / 963852wei) into every HTTP authentication challenge across all websites.
A Chrome webRequest listener intercepts authentication prompts before users see them, responding with threat actor credentials transparently. Users never witness the credential exchange the proxy authentication occurs silently in the background.
This design ensures seamless authentication to threat actor infrastructure while remaining completely invisible to victims.
Selective High-Value Domain Targeting
Once users activate VIP status through payment, the extension dynamically configures Chrome’s Proxy Auto-Configuration (PAC) script to route traffic from 170+ targeted domains through attacker-controlled proxies.
The domain list reveals sophisticated victim prioritization: developer tools (GitHub, npm registries, Docker), cloud service consoles (AWS, Azure, DigitalOcean), corporate platforms (Cisco, IBM, VMware), social media (Facebook, Twitter, Instagram), and adult content sites potentially for blackmail leverage.
With threat actor credentials already injected, traffic flows transparently through the malicious proxy infrastructure.
The attacker achieves complete man-in-the-middle positioning, capturing HTTP traffic, headers, POST data, form submissions, authentication cookies, and sensitive API tokens in real-time.
Beyond proxy-based traffic capture, the extension maintains a relentless 60-second heartbeat to its C2 server at phantomshuttle.space.
Every 5 minutes, it transmits user email addresses and plaintext passwords directly to the threat actor via unencrypted JSON requests, ostensibly for routine VIP status verification.
This dual-channel approach simultaneous proxy interception plus continuous plaintext credential exfiltration provides comprehensive data theft.
Impact and Recommendations
The 8+ year operational timeline demonstrates established operations rather than a short-term campaign.
The C2 domain, registered November 3, 2017, remains fully operational as of December 23, 2025, resolving to IP 47.244.125.55 on Alibaba Cloud in Hong Kong.
Multiple active API endpoints for configuration management, payment processing, and user status monitoring indicate a fully functioning commercial-grade criminal service.
The developer targeting creates significant corporate risk. Compromised credentials from GitHub, AWS, and npm repositories enable supply chain attacks and unauthorized code injection.
Organizations should immediately audit employee-installed extensions, deploy extension allowlisting policies, and block extensions requesting webRequest, authProvider, and proxy permissions simultaneously.
Users should review extension permissions before installation, avoid VPN extensions requesting sensitive permissions, and maintain separate credentials for personal and corporate systems.
Socket has submitted takedown requests to Google’s Chrome Web Store, though the extensions remain live at publication.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
