A renewed RTO scam campaign targeting Indian vehicle owners is gaining momentum. This follows a sharp rise in browser-based e-challan phishing operations that rely on shared and reusable fraud infrastructure. The latest findings indicate that attackers are exploiting trust in government transport services, continuing a pattern of RTO-themed threats that have persisted over recent years.
Unlike earlier campaigns that depended heavily on Android malware delivery, this new e-challan phishing campaign has shifted entirely to the internet browser. This change lowers the technical barrier for attackers while increasing the pool of potential victims.
Any user with a smartphone and a web browser can now be targeted, without requiring the installation of a malicious app. Cyble Research and Intelligence Labs (CRIL) investigation also aligns with coverage from mainstream Indian media outlets, including Hindustan Times, which have highlighted similar fake e-challan scams.
How the e-Challan Phishing Campaign Operates
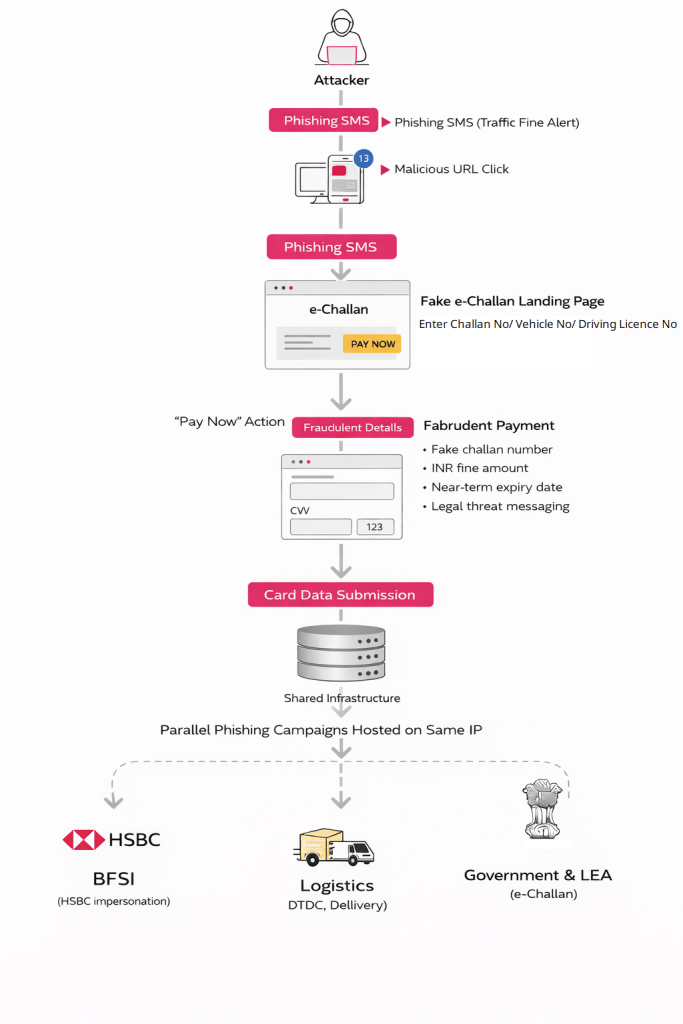
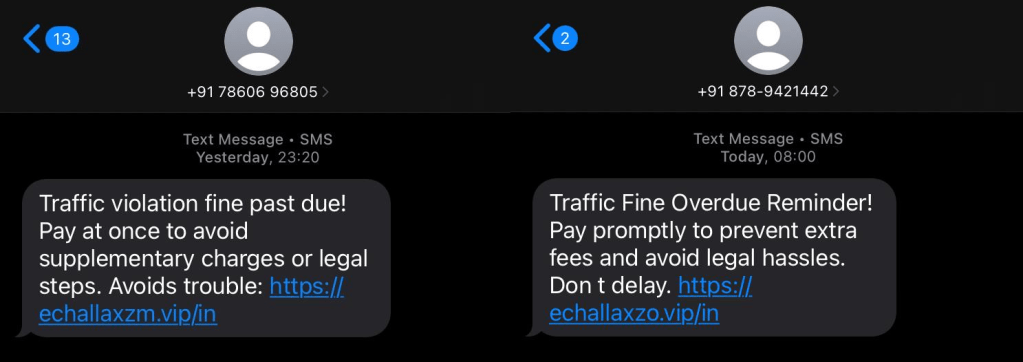
The e-challan phishing campaign primarily targets Indian vehicle owners through unsolicited SMS messages. These messages claim that a traffic violation fine is overdue and must be paid immediately to avoid legal consequences. The SMS typically contains threatening language referencing court action, license suspension, or additional penalties.
A shortened or deceptive URL, crafted to resemble an official e-challan domain, is embedded in the message. Notably, the messages lack personalization, allowing attackers to distribute them at scale. The sender appears as a regular mobile number rather than an identifiable shortcode, which increases delivery success and reduces immediate suspicion.

Clicking the link redirects the victim to a fraudulent e-challan portal hosted on the IP address 101[.]33[.]78[.]145. The phishing page closely mimics the branding and structure of legitimate government services, visually replicating official insignia, references to the Ministry of Road Transport and Highways (MoRTH), and National Informatics Centre (NIC) branding.


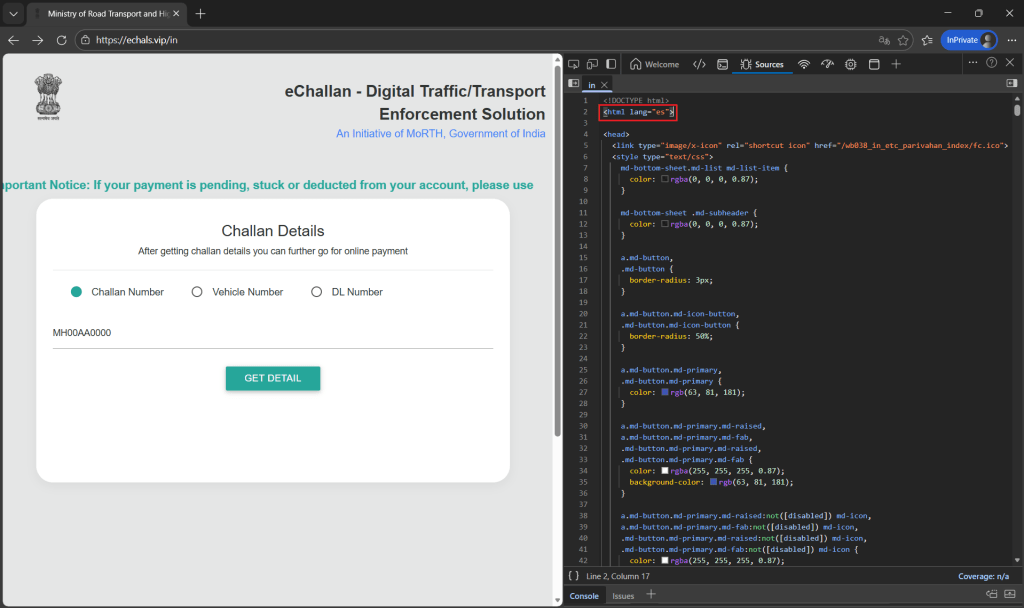

Technical analysis revealed that the page content was originally authored in Spanish and later translated into English via browser prompts, suggesting that attackers are reusing phishing templates across regions.
Fabricated Challans and Psychological Manipulation
Once on the fake portal, users are prompted to enter basic details such as a vehicle number, challan number, or driving license number. Regardless of what information is entered, the system generates a convincing-looking challan record.
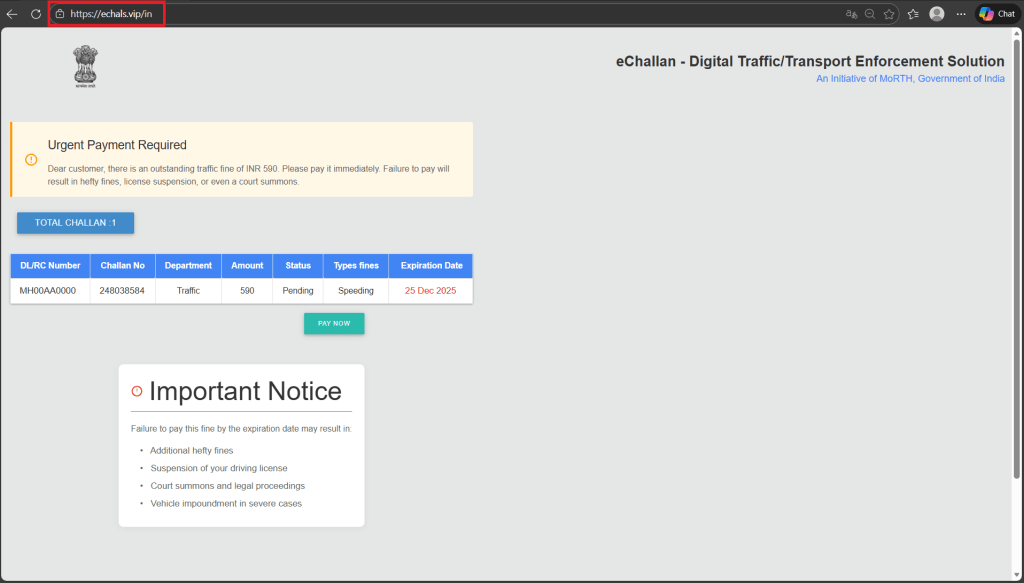

The fabricated record typically displays a modest fine amount, such as INR 590, along with a near-term expiration date. Prominent warnings about license suspension, court summons, or legal proceedings are displayed to heighten urgency.
This step is purely psychological. No real backend verification occurs. The goal is to convince victims that the challan is legitimate and time-sensitive, a hallmark of effective e-challan phishing and other RTO-themed threats.
Card Data Harvesting and Payment Abuse
When victims click “Pay Now,” they are taken to a payment page that claims to offer secure processing through an Indian bank.


However, the page only accepts credit or debit card payments, deliberately excluding UPI or net banking options that might leave clearer transaction trails. No redirection to an official payment gateway occurs. Instead, victims are asked to enter full card details, including card number, expiry date, CVV, and cardholder name.
Testing showed that the page accepts repeated card submissions without error, regardless of transaction outcome. This behavior indicates that all entered card data is transmitted directly to attacker-controlled servers, confirming the campaign’s focus on financial theft rather than legitimate payment processing.
Shared Infrastructure and Campaign Expansion
CRIL’s infrastructure analysis revealed that the same hosting environment is being used to support multiple phishing lures beyond e-challan scams. Another attacker-controlled IP address, 43[.]130[.]12[.]41, was found hosting domains impersonating India’s e-Challan and Parivahan services.


Several domains closely resemble legitimate branding, including lookalikes such as parizvaihen[.]icu. These domains appear to be automatically generated and rotated, suggesting the use of domain generation techniques to evade takedowns and blocklists.
Further investigation into IP address 101[.]33[.]78[.]145 uncovered more than 36 phishing domains impersonating e-challan services alone. The same infrastructure also hosted phishing pages targeting the BFSI sector, including HSBC-themed payment lures, as well as logistics companies such as DTDC and Delhivery.


Consistent user interface patterns and identical payment-harvesting logic across these campaigns confirm the existence of a shared phishing backend supporting multiple fraud verticals.
SMS Origin and Localized Credibility
The localized nature of this RTO scam, using Indian mobile numbers on domestic telecom networks and links to a State Bank of India account, shows how attackers deliberately exploit trust in familiar institutions to increase the success of e-challan phishing. Combined with realistic portal cloning, fabricated challan data, and urgency-driven messaging, this campaign reflects a mature and scalable fraud operation rather than an isolated activity.
The shift from malware-based attacks to browser-driven financial theft notes a digital world where awareness alone is not enough. As highlighted by Cyble and its research arm, CRIL, effective mitigation now depends on continuous threat intelligence, infrastructure tracking, rapid takedowns, and coordinated action across telecoms, banks, and security teams.
To stay protected from such RTO-themed threats and other large-scale fraud campaigns, organizations can leverage Cyble’s AI-powered threat intelligence capabilities.
Book a free demo to see how Cyble helps detect, disrupt, and prevent cybercrime at scale.
