A sophisticated cyberespionage campaign leveraging kernel-mode rootkit technology has been discovered targeting government organizations across Southeast and East Asia, with Myanmar and Thailand bearing the brunt of attacks.
Security researchers identified a malicious driver delivering the ToneShell backdoor, a hallmark tool of the Chinese-nexus HoneyMyte APT group, also tracked as Mustang Panda or Bronze President.
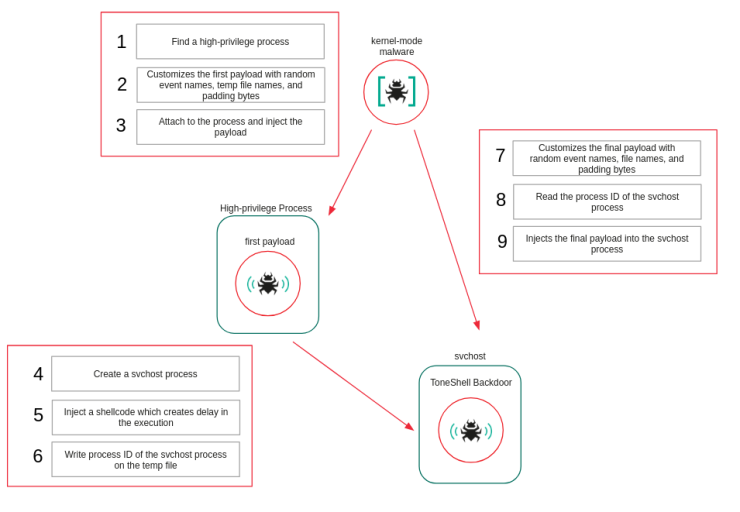
The campaign, which researchers assess began in February 2025, represents a significant evolution in HoneyMyte’s operational tradecraft, marking the first observed instance of ToneShell being deployed through a kernel-mode loader with advanced rootkit capabilities.
The malicious driver, named ProjectConfiguration.sys, is signed with a stolen digital certificate issued to Guangzhou Kingteller Technology Co., Ltd., valid from August 2012 to 2015.
The certificate bears serial number 08 01 CC 11 EB 4D 1D 33 1E 3D 54 0C 55 A4 9F 7F and has been observed signing other unrelated malware samples, suggesting multiple threat actors have obtained access to the compromised credential.
Telemetry analysis reveals nearly all victims had previously been infected with other HoneyMyte tools, including the ToneDisk USB worm, PlugX, and earlier ToneShell variants, indicating the threat actor likely leveraged existing compromises to deploy the rootkit.
Command-and-control infrastructure for the campaign was registered through NameCheap services in September 2024, utilizing domains avocadomechanism[.]com and potherbreference[.]com.
Advanced Rootkit Capabilities
The driver operates as a mini-filter with comprehensive protection mechanisms designed to evade detection and analysis.
It registers callback routines to intercept file operations, blocking deletion or renaming attempts through STATUS_ACCESS_DENIED responses to specific FileInformationClass values, including FileDispositionInformation and FileRenameInformation.
Registry protection is implemented through CmRegisterCallbackEx, with the malware dynamically selecting an altitude value starting at 330024 to position itself above legitimate security filters.
Critically, the rootkit tampers with Microsoft Defender WdFilter driver by changing its altitude to zero, effectively preventing it from loading into the I/O stack.
Process-level protection utilizes ObRegisterCallbacks to monitor handle operations, stripping access rights from any process attempting to interact with protected PIDs.
This shields both the driver itself and the svchost process containing the injected ToneShell backdoor from security tools and forensic analysis.
ToneShell Backdoor Evolution
The embedded ToneShell payload represents a notable evolution from previous variants. Rather than generating a 16-byte GUID as a host identifier, this version uses a 4-byte marker stored in C:ProgramDataMicrosoftOneDrive.tlb, derived from system-specific values including computer name and tick count.
Communication occurs over raw TCP port 443 with fake TLS 1.3 headers (0x17 0x03 0x04) instead of the TLS 1.2 pattern used in earlier versions.
The backdoor supports file upload/download, remote shell access via pipe, and session control through a command structure ranging from 0x1 to 0xD.
Researchers assess with high confidence the activity links to HoneyMyte based on ToneShell’s exclusive association with the group and the co-occurrence of PlugX and ToneDisk on compromised systems.
Because the shellcode executes entirely in memory, memory forensics becomes essential for detection.
Organizations in government sectors across Asia should prioritize memory analysis and behavioral detection to identify injection artifacts indicative of ToneShell presence.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
