CloudSEK has uncovered a sustained nine-month campaign by the RondoDoX botnet operation, revealing rapid exploitation of emerging vulnerabilities including the critical React2Shell vulnerability.
Analysis of exposed command-and-control logs spanning March through December 2025 demonstrates how threat actors swiftly adapted attack infrastructure following public disclosure, pivoting from traditional IoT targets to weaponizing Next.js applications within days of vulnerability research publication.
On December 10, Darktrace reported React2Shell exploitation patterns from honeypot telemetry, yet RondoDoX operators immediately changed infrastructure to evade detection.
CloudSEK observed new C2 servers emerge just three days later, maintaining active campaigns through present day.
During our routine scans for malicious infrastructure, CloudSEK’s TRIAD found loggers in use by threat actors.
The operation targets vulnerable web applications and IoT devices through automated exploitation frameworks deploying botnet payloads, web shells, and cryptocurrency miners across multiple architectures.
Three-Phase Attack Evolution
The campaign evolved through distinct operational phases, beginning with manual reconnaissance in March 2025 before transitioning to automated daily attacks by mid-April.
Initial exploitation testing focused on SQL injection, Java deserialization vulnerabilities, and WebLogic vulnerabilities, systematically probing internet-facing infrastructure for weaknesses.
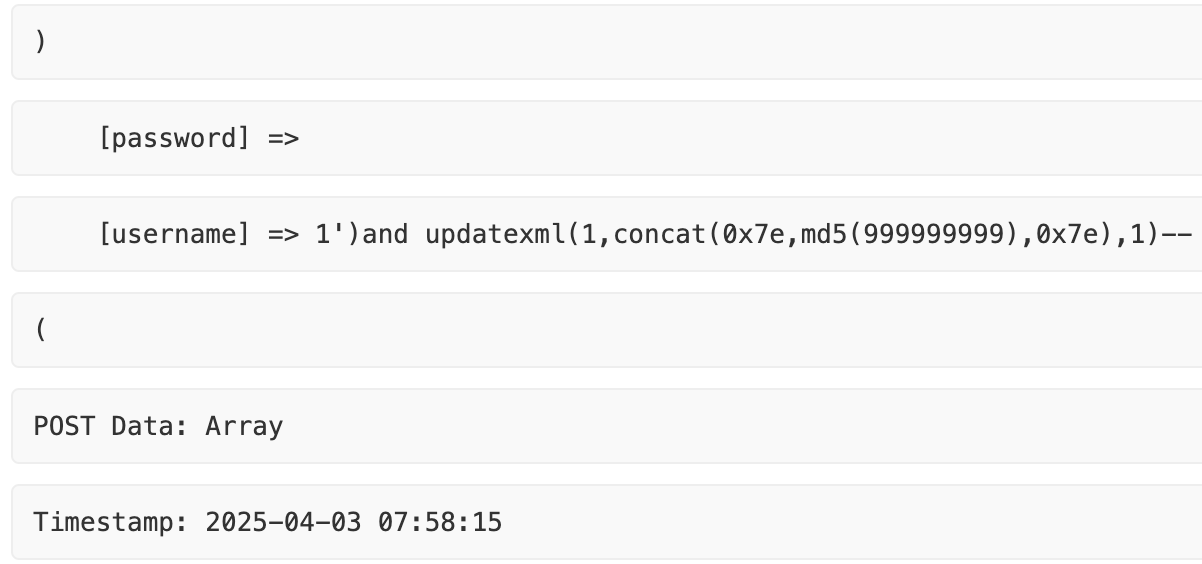
Phase two intensified during April through June with mass vulnerability scanning targeting CMS platforms including Drupal OGNL injection, Struts2 framework exploits, and WordPress plugin vulnerabilities.
Simultaneously, operators expanded IoT device targeting to Wavlink routers and network diagnostic interfaces vulnerable to command injection attacks.
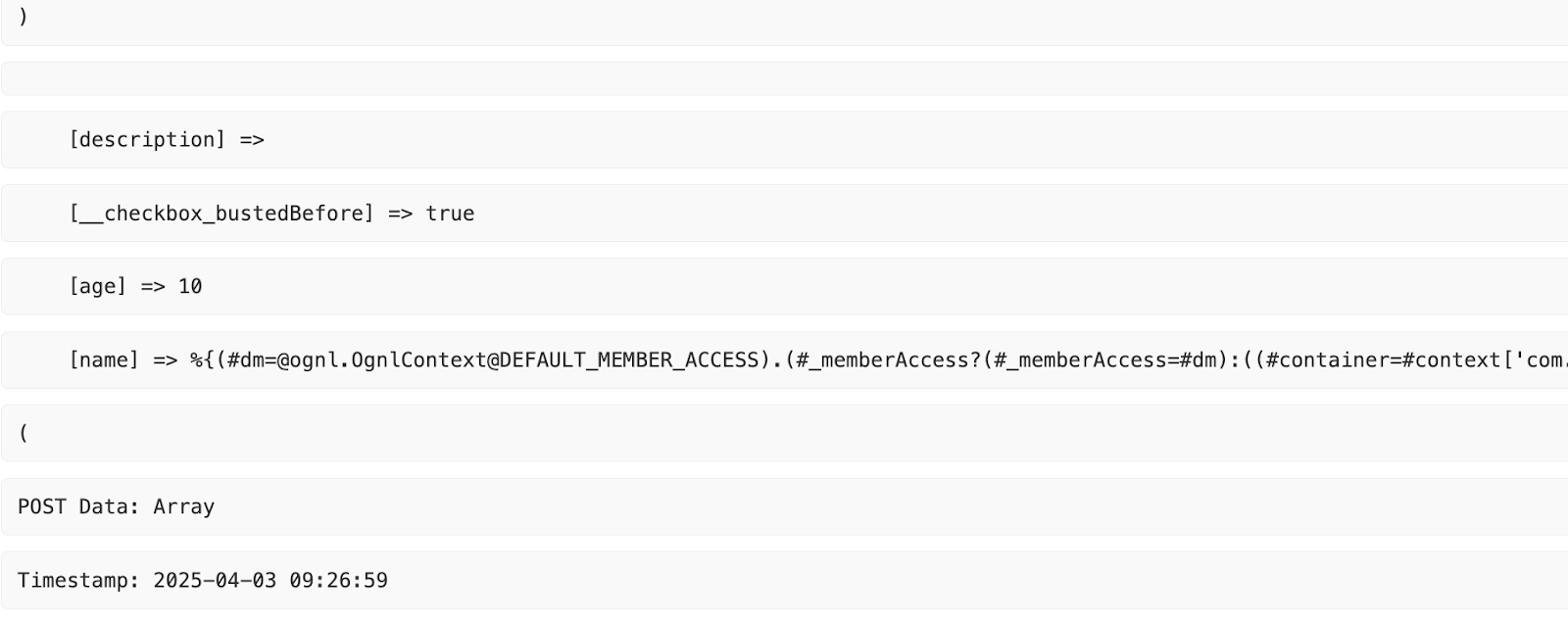
The campaign reached peak automation during phase three from July through December 2025, deploying the Rondo botnet infrastructure with hourly exploitation attempts.
CloudSEK identified six confirmed C2 servers operating across overlapping periods, delivering over ten variants of Rondo malware tailored for specific device architectures.
Attack frequency surged from sporadic manual testing to continuous hourly deployment cycles, with December 2025 marking the highest activity period coinciding with Next.js RCE exploitation.
React2Shell Exploitation Wave
Following React2Shell disclosure, RondoDoX operators rapidly weaponized CVE-2025-55182 through two distinct attack waves.
Initial scanning operations between December 8-16 identified vulnerable Next.js servers through blind RCE testing with output exfiltration via HTTP redirects, executing commands including whoami and arithmetic validation tests.
Wave two commenced December 13 with active IoT botnet deployment leveraging Node.js process execution capabilities.
Attackers established new C2 infrastructure at 5.255.121.141 and 51.81.104.115, distributing ELF binaries through /nuts/poop (cryptocurrency miner), /nuts/bolts (persistence framework), and /nuts/x86 (Mirai variant) endpoints.
The “bolts” payload functions as a Linux dominance framework, terminating competing malware and enforcing persistence through crontab modifications while continuously scanning /proc to eliminate rival botnet processes every 45 seconds.
CloudSEK recorded over 40 repeat attacks on identical vulnerabilities within six days, demonstrating persistent targeting of unpatched infrastructure.
Organizations running Next.js Server Actions face critical RCE exposure, with complete server compromise possible through prototype pollution attacks in deserialization processes.
Security teams must conduct emergency audits of Next.js applications using Server Actions, implementing strict input validation on serialized data and upgrading to patched versions immediately.
IoT devices require network segmentation into dedicated VLANs with egress filtering, while identified C2 infrastructure should be blocked at perimeter firewalls.
Deployment of behavioral monitoring for suspicious /tmp directory execution and chmod operations enables detection of persistence mechanisms before full compromise occurs.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
