A sophisticated phishing campaign is currently circulating within the Cardano community, utilizing high-trust social engineering to distribute malware under the guise of a new wallet application.
The campaign centers on a professionally crafted email announcement titled “Eternl Desktop Is Live Secure Execution for Atrium & Diffusion Participants,” which directs users to download a fraudulent software installer capable of establishing remote access to victim machines.
The attack vector is notable for its polished presentation and deep knowledge of the Cardano ecosystem.
The malicious emails leverage specific governance narratives, promoting themes of security, decentralization, and staking incentives.
By referencing legitimate ecosystem elements such as Atrium and the Diffusion Staking Basket, along with promises of NIGHT and ATMA token rewards, the attackers effectively establish a façade of credibility.
The email employs persuasive technical language, positioning the fake “Eternl Desktop” as a “local-first, non-browser signing” solution a feature often requested by security-conscious crypto users.
Infrastructure and Installer Red Flags
Despite the convincing email, the distribution infrastructure raises immediate alarms. The download link points to hxxps://download[.]eternldesktop[.]network, a newly registered domain with no historical reputation or association with the official Eternl team.
There has been no verification of this software on official Eternl communication channels.
Furthermore, the software is distributed as a raw MSI installer (Eternl.msi) lacking digital signature transparency, release notes, or public checksums.
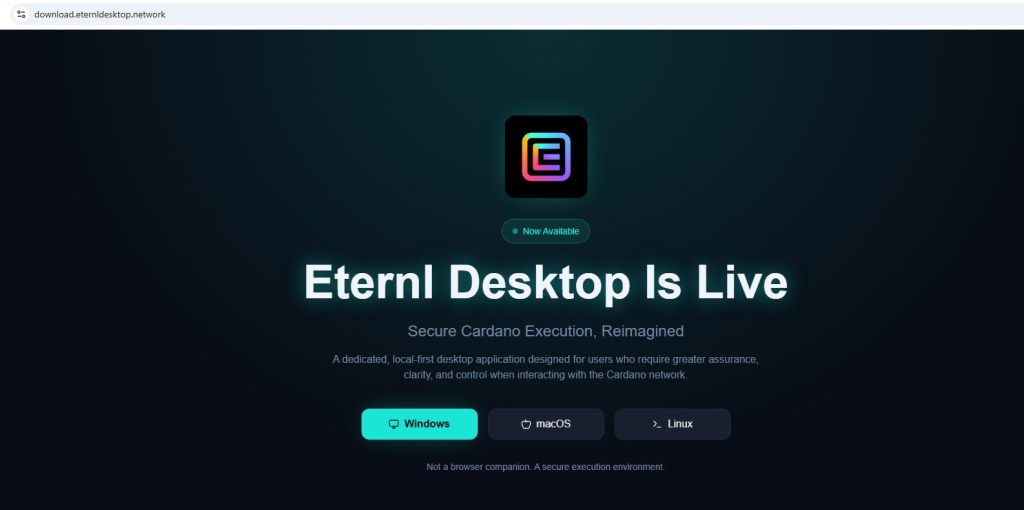
This opacity prevents users from verifying the integrity of the file before execution a critical red flag for any cryptocurrency software.
The communication lacks the spelling errors typical of low-effort phishing, culminating in an authoritative call to action claiming that “Eternl Desktop is where Cardano decisions are finalized.”
Technical Analysis: RMM Abuse
Technical analysis of the 23.3MB installer reveals that it is not a wallet application at all. Instead, it serves as a wrapper for legitimate Remote Monitoring and Management (RMM) software.
Inside the MSI package is an executable named unattended-updater.exe, which is identified as LogMeIn Resolve Unattended (GoTo Resolve).
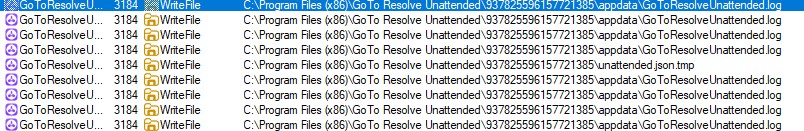
Upon execution, the installer creates a directory at C:Program Files (x86)GoTo Resolve Unattended and deploys JSON configuration files, specifically unattended.json.
This configuration is designed to enable “unattended access,” allowing a remote technician in this case, the threat actor to connect to the system without user intervention.
Network traffic analysis confirms the malware attempts to communicate with various subdomains of gotoresolve.com, including dumpster.console.gotoresolve.com and zerotrust.services.gotoresolve.com.
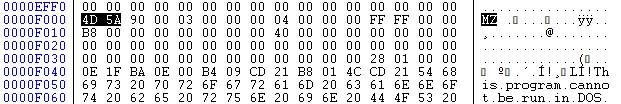
This campaign represents a high-risk combination of new infrastructure and RMM abuse. By bundling legitimate administrative tools like LogMeIn inside a wallet installer, attackers can often bypass standard antivirus detection, as the underlying software is technically “clean.”
However, once installed, it grants the attacker persistent, administrative control over the victim’s device, allowing them to drain wallets, harvest credentials, and monitor user activity.
Users are advised to avoid the “Eternl Desktop” email, strictly download software from official repositories, and treat any unsolicited software announcements with extreme caution.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
