ESET Research has uncovered a significant surge in CloudEye malware detections, with a 30-fold increase in the second half of 2025.
The security firm detected more than 100,000 infection attempts over the six months, signaling a widespread threat affecting organizations globally.
CloudEyE operates as a Malware-as-a-Service (MaaS) downloader and cryptor designed to conceal and deploy secondary payloads including Rescoms, Formbook, and Agent Tesla known information stealers and remote access trojans.
The proliferation of CloudEyE represents a notable shift in malware distribution tactics, leveraging the growing ecosystem of ransomware-as-a-service and malware-as-a-service platforms.
By functioning as a stealthy delivery mechanism, CloudEyE enables threat actors to distribute diverse malware families while maintaining operational flexibility and anonymity.
This modular approach allows attackers to customize payloads based on target environment, increasing the effectiveness of their campaigns.
Multi-Stage Infection Chain
CloudEyE’s infection methodology notes a sophisticated multi-stage architecture that maximizes evasion capabilities.
The initial downloader stage spreads through PowerShell scripts, JavaScript files, and NSIS (Nullsoft Scriptable Install System) executables.
These entry points are commonly delivered via spearphishing emails, drive-by downloads, and compromised websites. Once execution is achieved, the downloader retrieves the cryptor component the second stage which contains the final payload.
A critical characteristic distinguishing CloudEyE is its heavy obfuscation across all infection stages. This encryption and code obfuscation technique protects against endpoint detection and response (EDR) solutions, static analysis, and threat intelligence databases.
The layered obfuscation approach makes forensic analysis significantly more difficult for security researchers and incident responders, allowing the malware to persist longer within target environments.
Geographic analysis of CloudEyE’s attack distribution reveals concentrated targeting in Central and Eastern Europe, accounting for 32 percent of registered infection attempts during H2 2025.
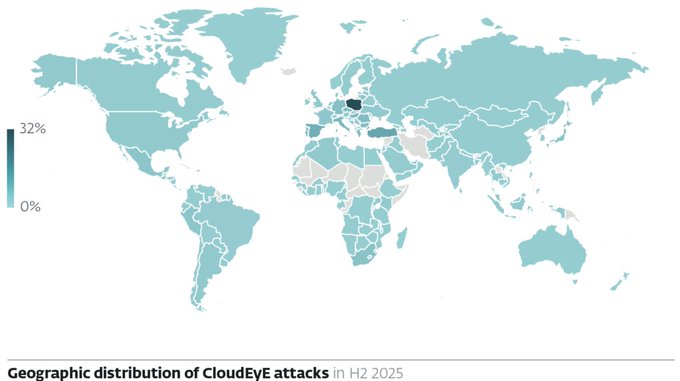
ESET observed coordinated email campaign waves throughout September and October 2025, suggesting organized distribution efforts by sophisticated threat actors.
The geographic concentration indicates targeted operations rather than indiscriminate distribution, pointing to specific industry sectors or organizational vulnerabilities within these regions.
Implications for Enterprise Security
The CloudEyE surge underscores the evolving threat landscape where modular malware architectures and MaaS platforms democratize malware distribution.
Organizations must recognize that traditional signature-based detection mechanisms prove insufficient against heavily obfuscated payloads.
The infection chain’s reliance on PowerShell and JavaScript legitimate system tools highlights the challenge of distinguishing malicious activity from normal administrative operations.
Organizations should implement behavioral-based detection systems capable of identifying suspicious PowerShell and JavaScript execution patterns.
Email security filtering should prioritize blocking NSIS executables and suspicious script attachments.
Additionally, endpoint detection and response solutions with advanced heuristics and machine learning capabilities provide superior visibility into obfuscated threat activity.
User security awareness training remains essential, as spearphishing remains the primary infection vector for CloudEyE distribution.
The 100,000+ infection milestone represents a watershed moment in malware prevalence, demonstrating the operational maturity and reach of CloudEyE’s infrastructure.
Continued monitoring of this threat remains critical as its modular design enables rapid evolution and adaptation.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
