Ransomware attacks don’t begin with encryption. They start with reconnaissance and security researchers just documented a significant reconnaissance operation that unfolded over the Christmas holiday.
Between December 25 and 28, a single operator systematically scanned the internet for vulnerable systems, testing more than 240 different exploits against targets and logging every successful hit.
That harvested data a fresh inventory of confirmed vulnerabilities will likely fuel targeted intrusions throughout 2026 and potentially be weaponized by criminal marketplaces and threat actors seeking initial access points.
Initial Access Brokers (IABs) function as the reconnaissance units of the ransomware economy. Rather than executing encryption or data theft operations, IABs specialize in identifying exploitable systems and building catalogs of vulnerable targets.
This operational specialization reflects the modern cybercriminal division of labor: IABs focus exclusively on finding entry points, while ransomware crews handle monetization and extortion.
The transaction model operates through criminal marketplaces where access to a compromised corporate network might command prices ranging from several thousand dollars to significantly higher amounts, depending on the target’s value.
The reconnaissance operation observed over Christmas represents the supply-side of this illicit market actively replenishing its inventory.
Campaign Technical Details
The operation originated from two IP addresses registered to CTG Server Limited (AS152194): 134.122.136.119 and 134.122.136.96.
Requests arrived at intervals of 1–5 seconds, and each target was tested against 11 different exploit types.
The attacker deployed Out-of-Band Application Security Testing (OAST) domains to confirm vulnerabilities when a system falls victim to exploitation, it transmits outbound requests to the attacker’s callback infrastructure.
Researchers identified over 57,000 unique OAST subdomains, all connected to ProjectDiscovery’s Interactsh platform.
The tooling characteristics align with Nuclei, an open-source vulnerability scanner, operating at industrial scale.
The attacker’s specific domain selection enabled security analysts to decode subdomains using techniques previously outlined in a 2024 LabsCon presentation on OAST infrastructure analysis.
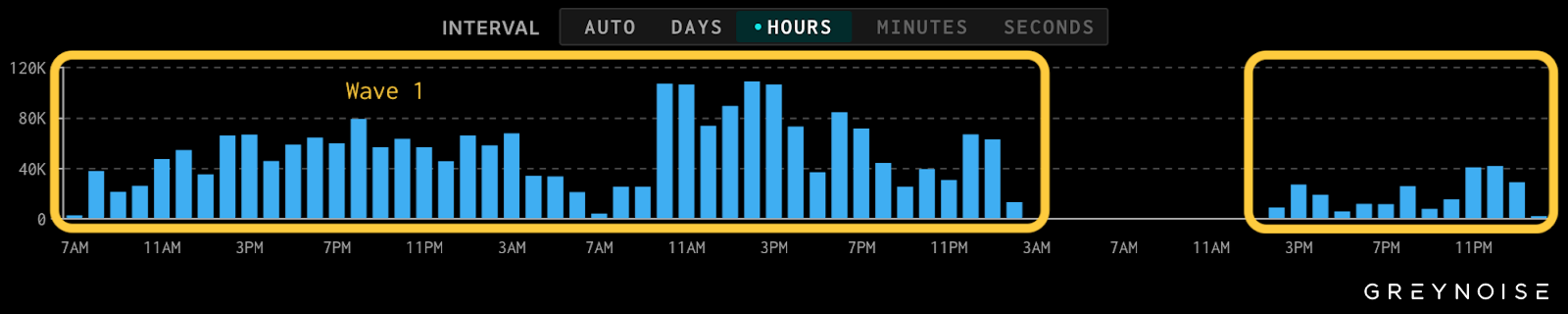
The campaign executed in two distinct waves. The initial wave utilized both IP addresses during Christmas day, while the second wave appeared 12 hours later using a single IP address and introducing 13 additional exploit templates apparently overlooked during the first phase.
JA4 network fingerprints and shared Machine ID signatures across 98 percent of attempts confirm this represents a single operator rather than a coordinated group effort.
The timing reflects calculated operational planning. Attackers understand precisely when security defenses weaken.
Holiday periods create conditions ideal for sustained reconnaissance: skeleton security crews, delayed alert response, and reduced log review capacity.
A scanning campaign that detection systems would identify and block within hours during normal operations can persist for days during holiday weekends.
The December 25–28 window provided this operator four uninterrupted days to probe internet-connected systems.
Vulnerability data harvested during this campaign window retains value long after the operation concludes, becoming a reusable catalog for future intrusions.
Infrastructure Assessment
CTG Server Limited presents notable concerns. Despite existing for approximately one year, this Hong Kong-registered hosting provider manages roughly 201,000 IPv4 addresses distributed across 672 prefixes.
Prior research identified AS152194 as the leading ASN for phishing domains within the FUNNULL CDN infrastructure. The network also announces bogon routes a network hygiene indicator and multiple IP ranges appear on various abuse blocklists.
This profile suggests a provider operating with minimal abuse enforcement mechanisms, making it attractive infrastructure for operations requiring resilience and evasion capabilities.
Organizations should review server and network logs from December 25–28 for connections from the identified IP addresses. DNS log examination for queries to OAST domains (.pro, .site, .me, .online, .fun, .live) provides additional detection opportunities.
Identified matches indicate confirmed vulnerabilities in the organization’s environment meaning attackers possess technical knowledge of how to establish access, and this intelligence may already be listed for sale in criminal marketplaces.
While no evidence currently ties this campaign to state-aligned actors, high-quality vulnerability intelligence historically circulates beyond criminal markets.
State-aligned groups have previously acquired similar reconnaissance data through broker purchases or parallel collection efforts, enabling long-term objectives including critical infrastructure access and espionage operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
