Cybersecurity researchers have uncovered a sophisticated AsyncRAT campaign exploiting Cloudflare’s free-tier services and TryCloudflare tunneling domains to evade detection while delivering remote access trojan payloads through multi-stage infection chains that leverage legitimate infrastructure.
Threat actors behind this AsyncRAT operation are weaponizing Cloudflare’s trusted infrastructure to host WebDAV servers, effectively masking malicious activities under legitimate domains that bypass traditional security solutions.
The attack begins with phishing emails containing Dropbox links that lead victims to download malicious files disguised as pdf files.
These Internet Shortcut files redirect to WebDAV resources hosted on various TryCloudflare domains, including plus-condos-thy-redeem.trycloudflare.com and owners-insertion-rentals-pursuit.trycloudflare.com, initiating a complex multi-stage infection process.
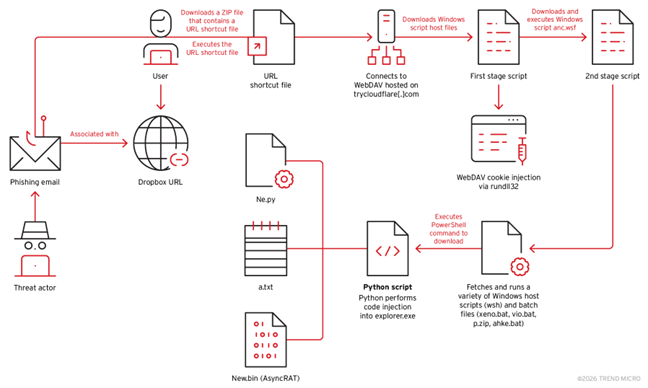
AsyncRAT demonstrates advanced techniques combining social engineering, legitimate tool abuse, and sophisticated code injection methods targeting Windows systems.
Technical Attack Chain
Once victims open the malicious shortcut file, the attack downloads Windows Script Host files (as.wsh and anc.wsf) that orchestrate the subsequent infection stages.
The scripts download batch files (vio.bat and xeno.bat) responsible for establishing a complete Python environment on the compromised system by fetching Python 3.14.0 directly from the official Python website a technique that appears legitimate to security monitoring tools.
The campaign employs sophisticated deception tactics by displaying legitimate PDF documents during execution, specifically downloading invoice-themed documents from ihk.de to convince victims that they’ve opened a standard business document.
Meanwhile, the malicious payload executes silently in the background, establishing persistence mechanisms and downloading additional components.
The attackers ensure persistence through multiple vectors, including startup folder scripts (ahke.bat and olsm.bat) that guarantee the malware executes upon system restart.
Meanwhile, rundll32.exe executes the DavSetCookie function from davclnt.dll with parameters specifying a WebDAV server (plus-condos-thy-redeem.trycloudflare[.]com) and an SSL connection.
The campaign leverages “living-off-the-land” techniques using native Windows utilities, including Windows Script Host, PowerShell, rundll32.exe, and the WebClient service, making detection significantly more challenging.
Python-Based Code Injection
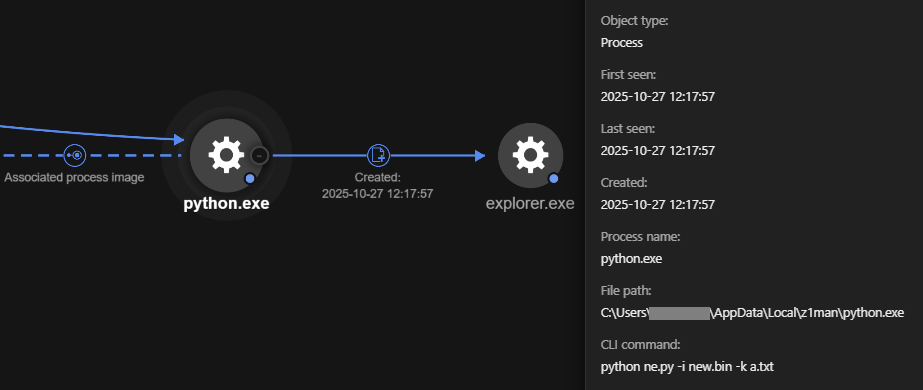
The core of the attack involves a Python script (ne.py) that performs Polymorphic Asynchronous Procedure Call (APC) injection to execute arbitrary code within legitimate Windows processes.
The script decrypts the main payload (new.bin) using keys stored in an accompanying text file (a.txt) and injects the AsyncRAT shellcode into explorer.exe processes, providing attackers with comprehensive remote access capabilities including keylogging, screen capturing, and remote command execution.
Analysis revealed that the shellcode was generated using Donut, an open-source framework for creating position-independent shellcode, demonstrating the threat actors’ technical sophistication and knowledge of advanced exploitation techniques.
Trend Vision One successfully detects and blocks the indicators of compromise associated with this campaign, providing customers with tailored threat hunting queries, threat insights, and intelligence reports.
Security researchers emphasize the importance of multi-layered security approaches, including monitoring for unusual WebDAV connections, PowerShell execution patterns, and unauthorized Python installations in user directories.
Organizations should implement enhanced email security controls, user awareness training focused on identifying phishing attempts with double-extension files, and network monitoring for connections to TryCloudflare domains.
This campaign underscores the ongoing challenge of distinguishing malicious activity when threat actors abuse legitimate cloud services and trusted infrastructure for payload delivery and command-and-control operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
